Method for implementing credible recovery system in operating system
An operating system and recovery system technology, applied in the field of operating systems, can solve the problems of destroying the consistency and security protection performance of the operating system, lack of operating system security, and lack of foundation for computer system security, etc., to meet the requirements of high throughput and reliability. Effects of Sexual Demand, Good Scalability, and Robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The invention discloses a method for realizing a trusted recovery system in an operating system, and adopts the method to establish a trusted recovery system on a Linux operating system (issue version Fedora Core 3, kernel version 2.6.8).
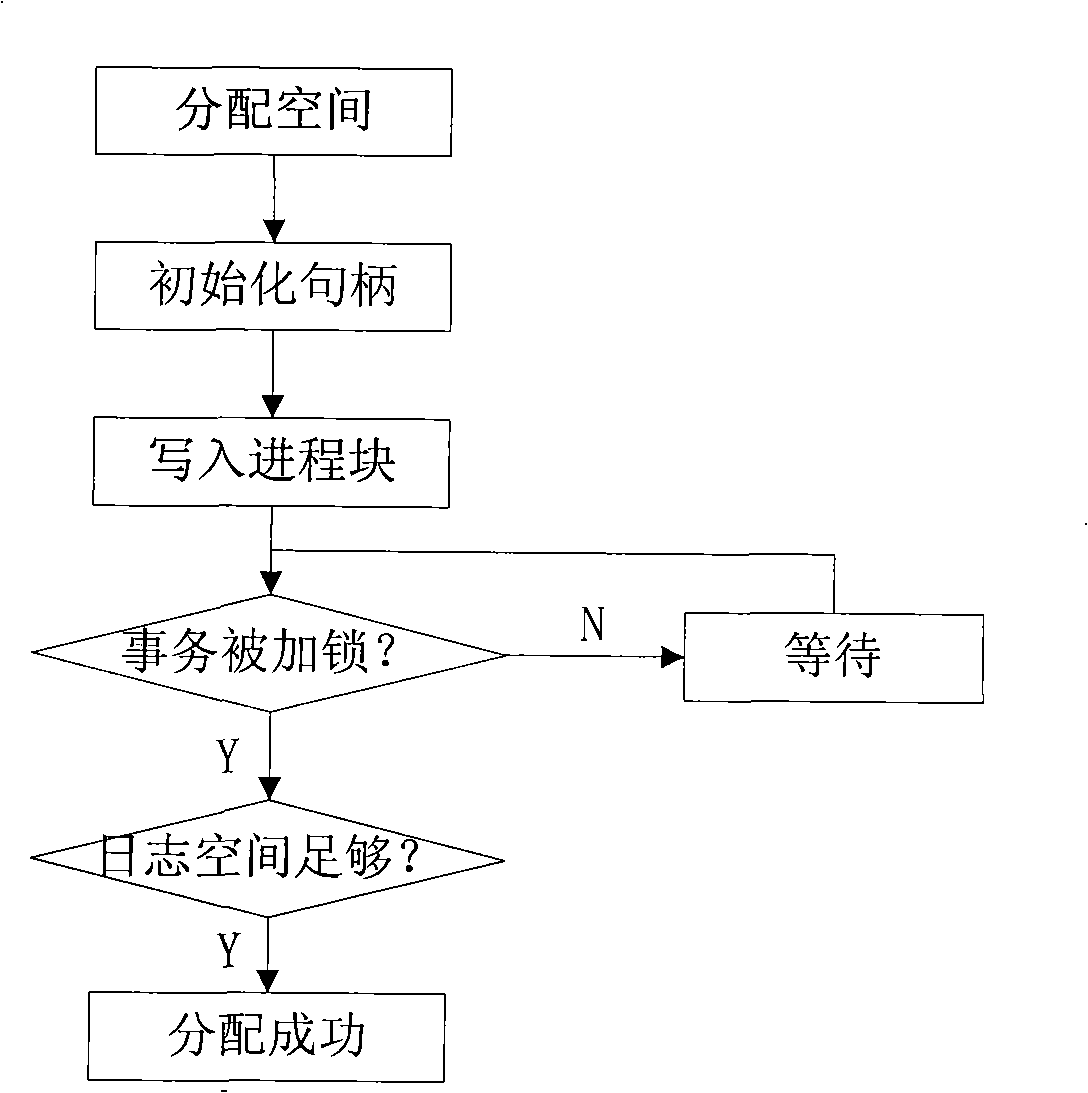
[0040] The method for realizing a trusted recovery system in an operating system includes the following steps:
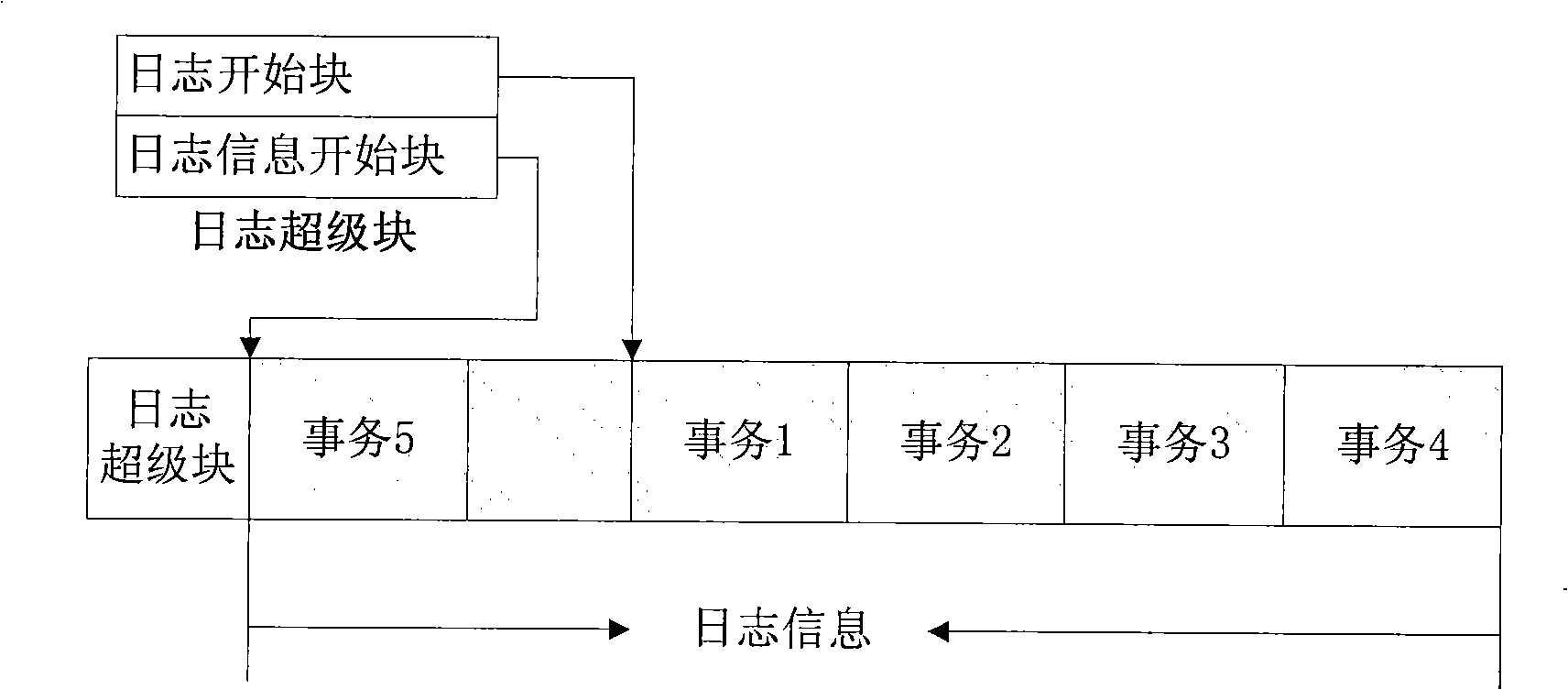
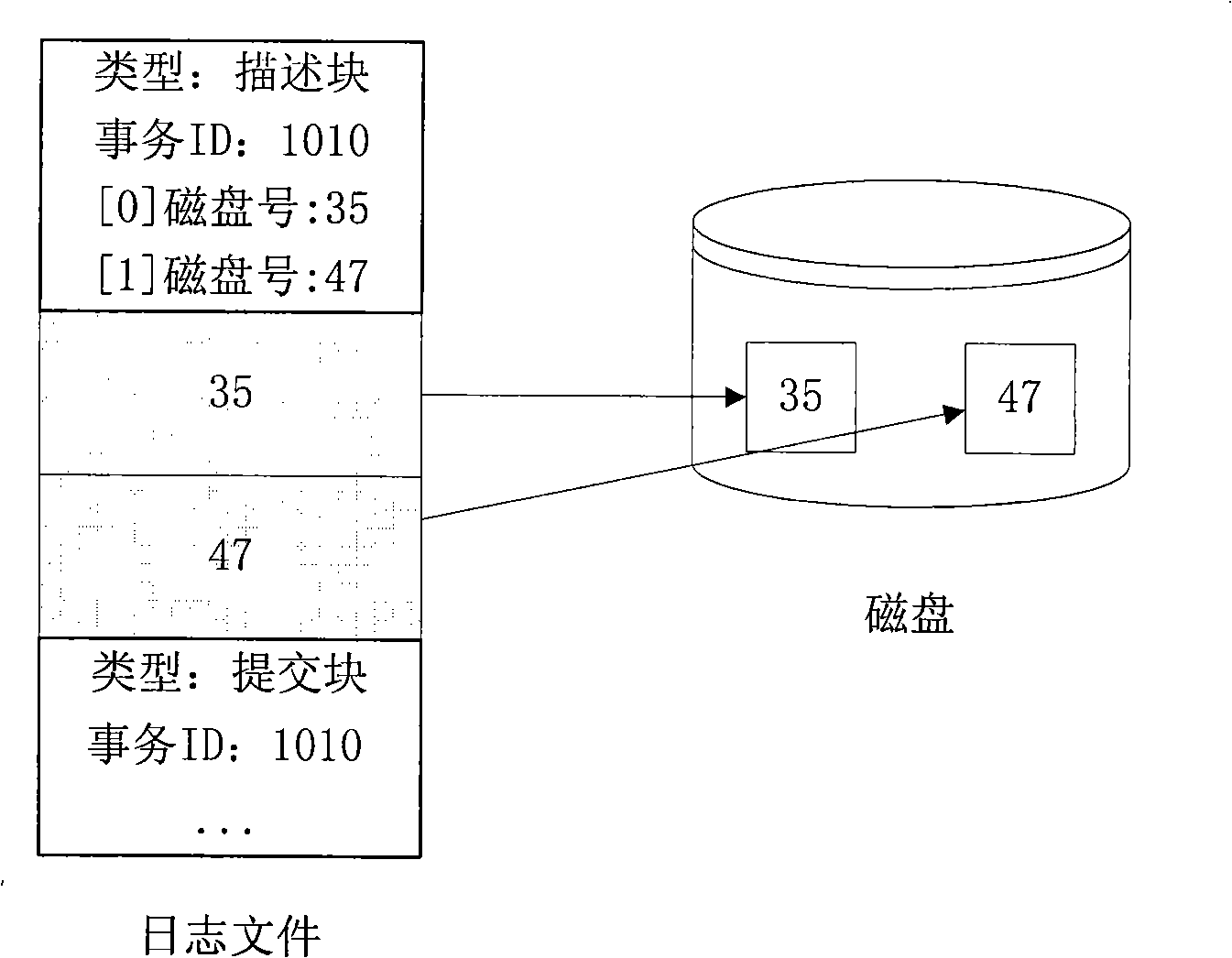
[0041] 1) Create a log file designed for disk blocks. It consists of a long sequence of disk blocks. Each disk block has a serial number. It is logically regarded as a circular queue, and the log data blocks are written in sequence. ;
[0042] A log file is a very long sequence of disk blocks, each with a unique sequence number. System recovery requires quick access to this log but most of it can be kept offline or discarded. Online log files are used to hold the "useful" parts of the log. The log files are managed as a ring buffer. The log file can be regarded as a circular queue logically, and the log data blocks are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com