Mass storage device with automated credentials loading
A technology of large-capacity storage and host device, applied in computer security device, protection of storage content to prevent loss, digital data authentication, etc., can solve problems such as inconvenience and restrict user acceptance, and achieve the effect of risk reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
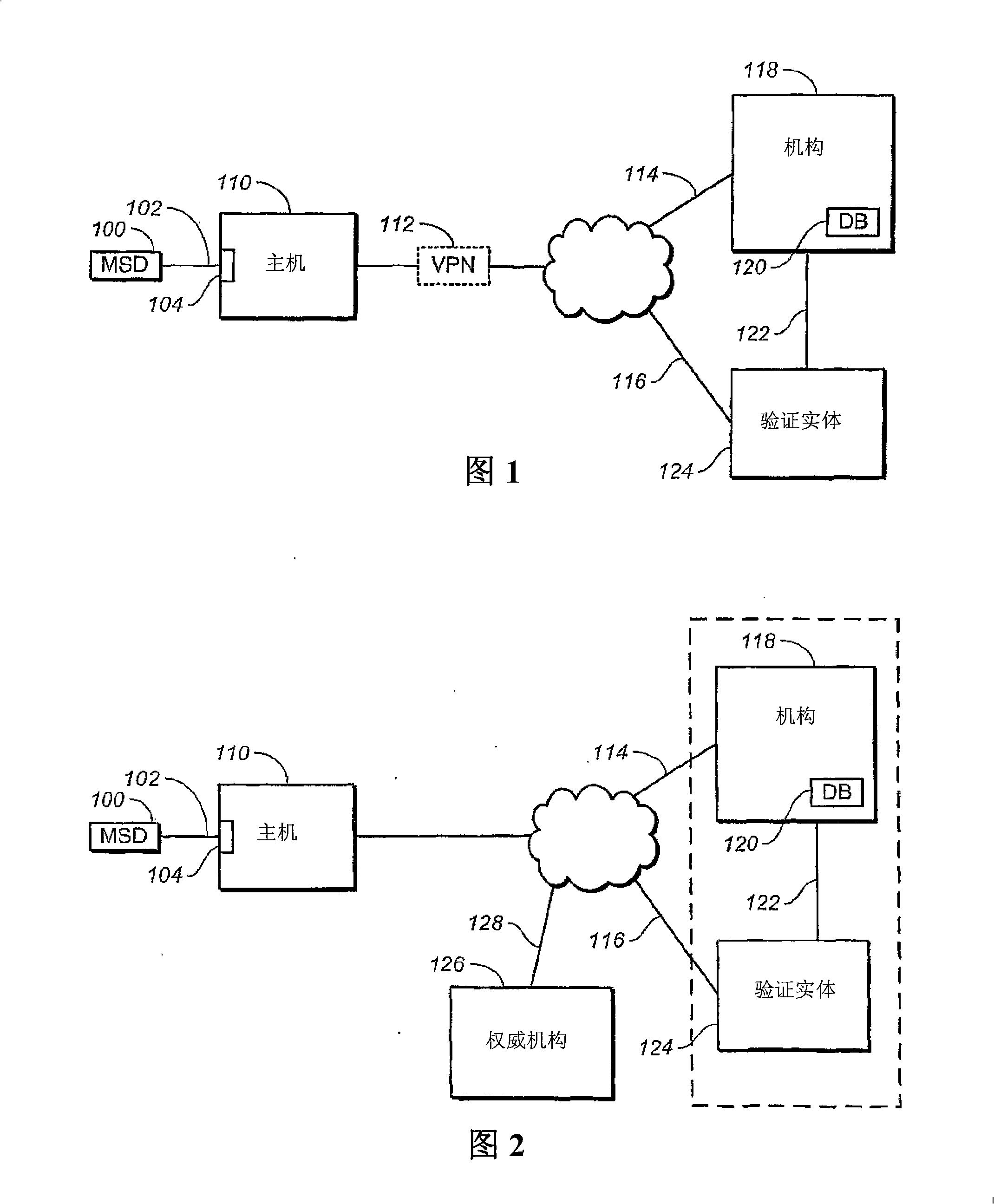
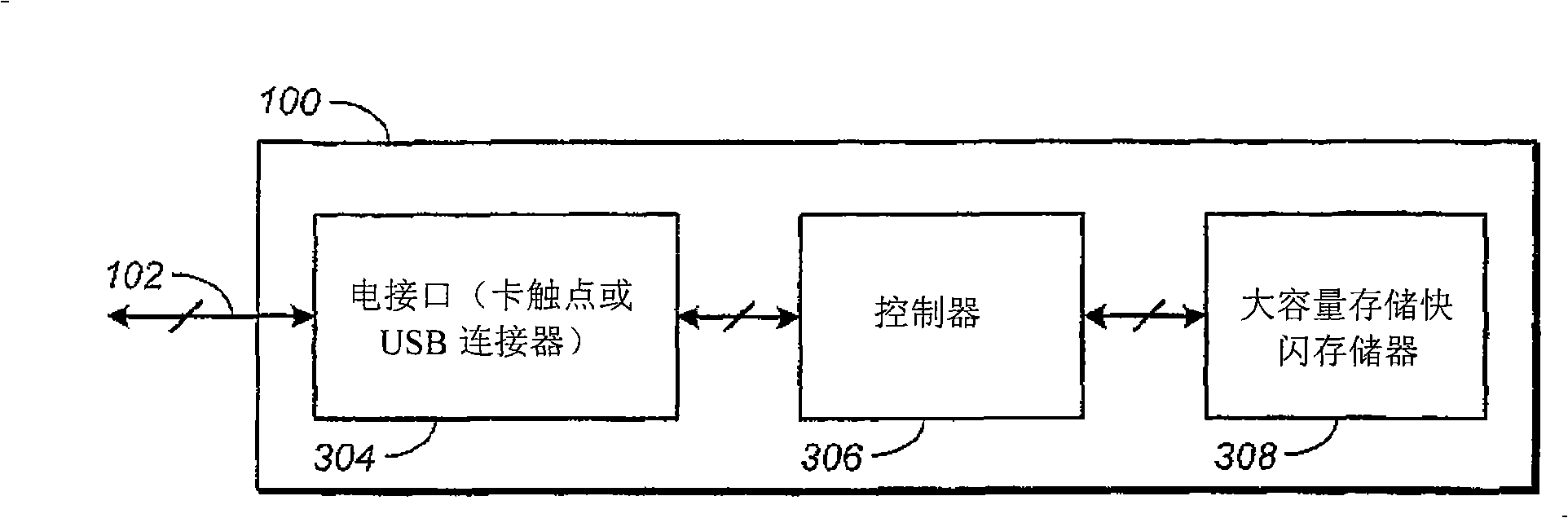
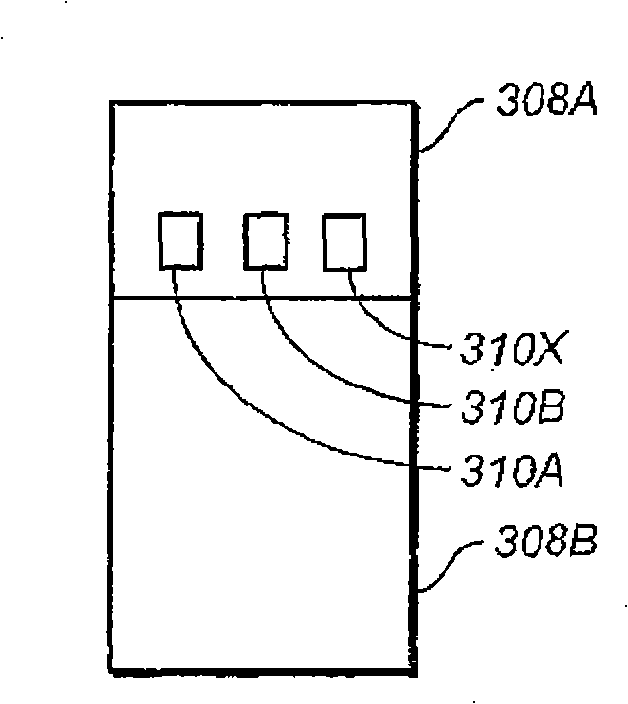
[0038] Portable mass storage devices are widely used to store digital content such as photos, music, videos and documents. It's also large enough to store large software applications. Typically, portable mass storage devices now use flash memory for storage purposes and have a memory card or portable USB drive form factor. These mass storage devices differ from other portable devices that can only store minimal information such as that required for transaction or identification purposes. Mass storage devices also differ from other special-purpose devices, such as key fobs and tokens used for authentication, in that while special-purpose devices may have small amounts of memory to store relevant user-identifying information, they are not designed to Store and transfer relatively large and often encrypted files frequently and in a repeatable manner.
[0039] For example, a memory card, one embodiment of a portable mass storage device, must be able to quickly store pictures of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com