Network security management method and system thereof
A network security and management method technology, applied in the management system field based on local data encryption and transmission encryption to realize a secure network, can solve problems such as imperfect security functions and low security levels, and achieve perfect security functions, high security levels, and ensure safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
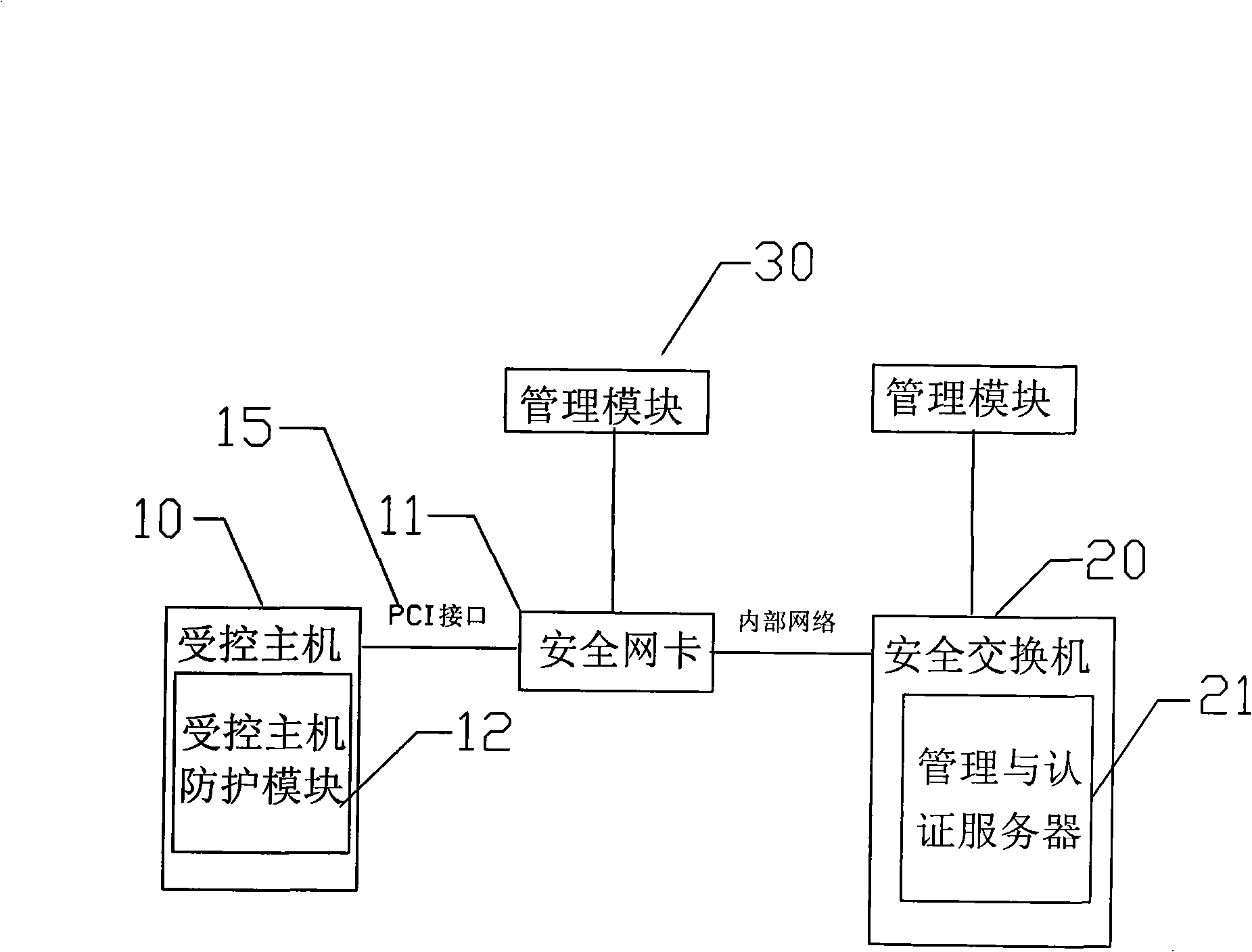
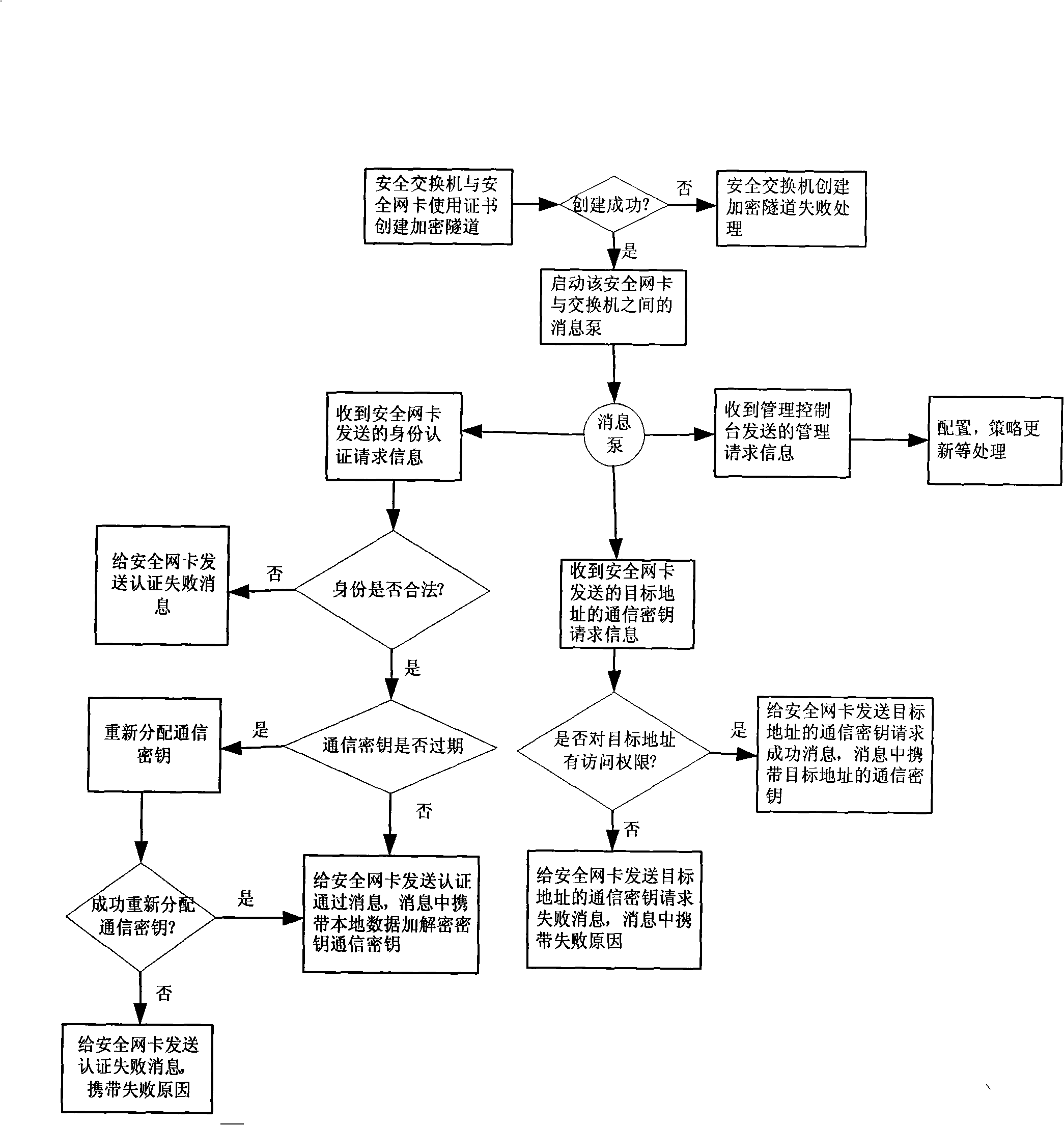
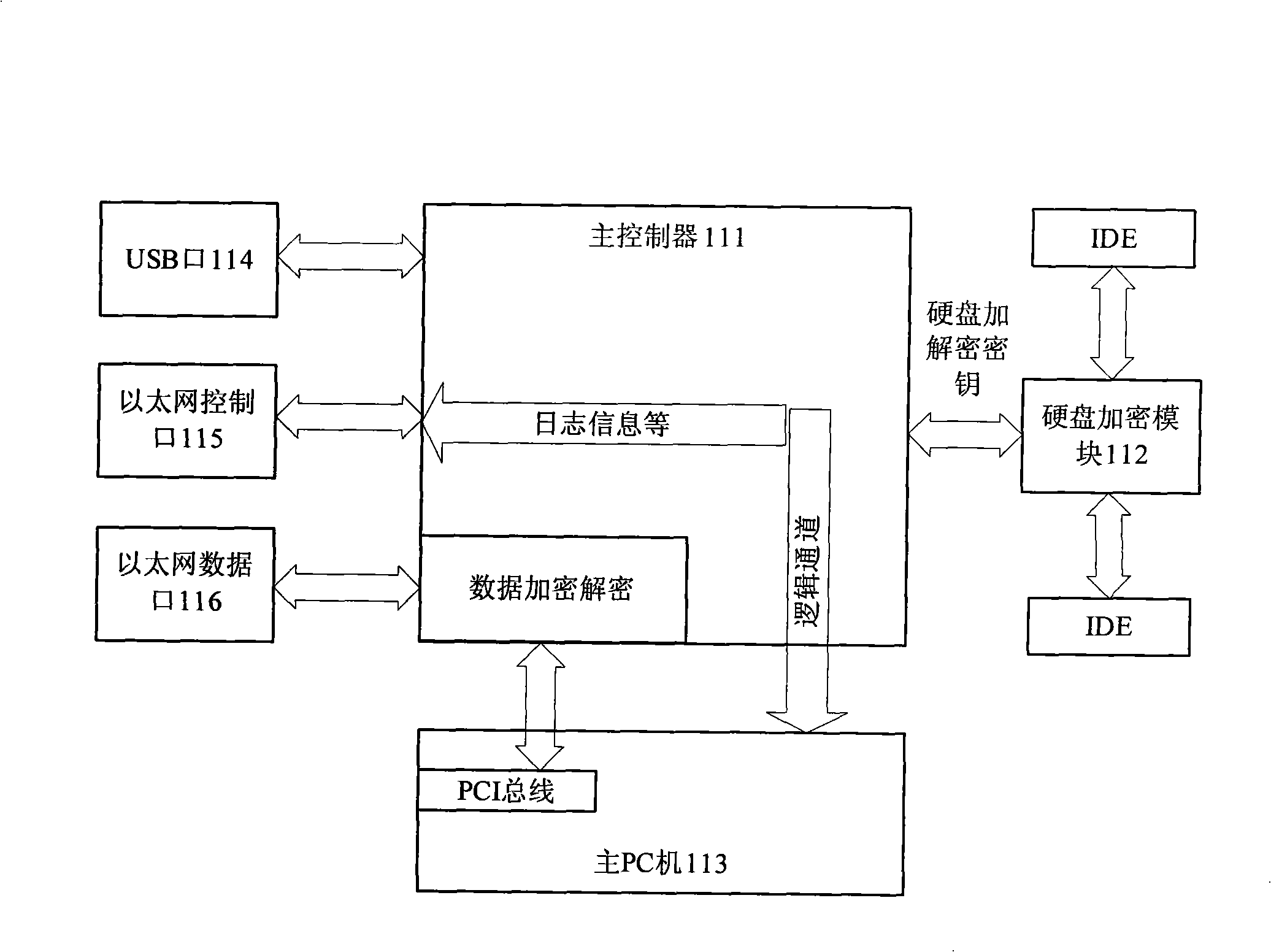
[0026] The principle of the network security management method and system of the present invention can be found in figure 1 . It mainly embodies the multiple network security defense mechanism of the three-level defense of information source defense, information transmitter defense and information user defense, truly providing a safe information exchange environment for network users and ensuring the security of network data transmission and local data.
[0027] The network security management method of the present invention comprises the following steps:
[0028] Step 1: the secure network card 11 and the secure switch 20 use the certificate to create an encrypted tunnel;
[0029] Step 2: the security network card 11 requests identity verification from the security switch 20;
[0030] Step 3: When the security switch 20 has passed the identity authentication of the security network card 11, generate the communication key of the security network card 11, and notify the secur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com