Safety processing method and apparatus
A security processing and security technology, applied in the field of password verification, can solve the problems of occupying security processing system resources and low efficiency, and achieve the effect of reducing system resources, improving efficiency, and efficient security processing process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
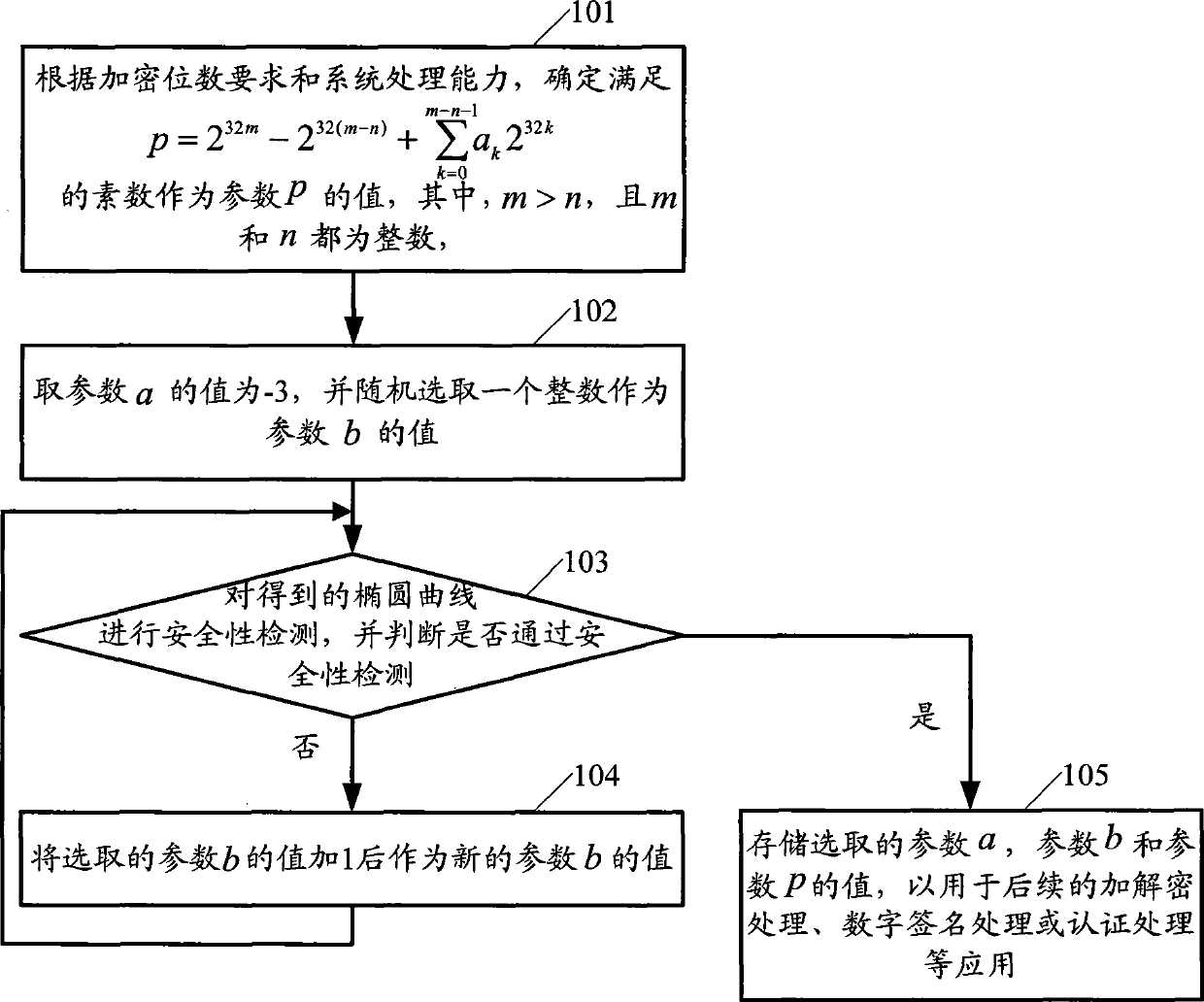
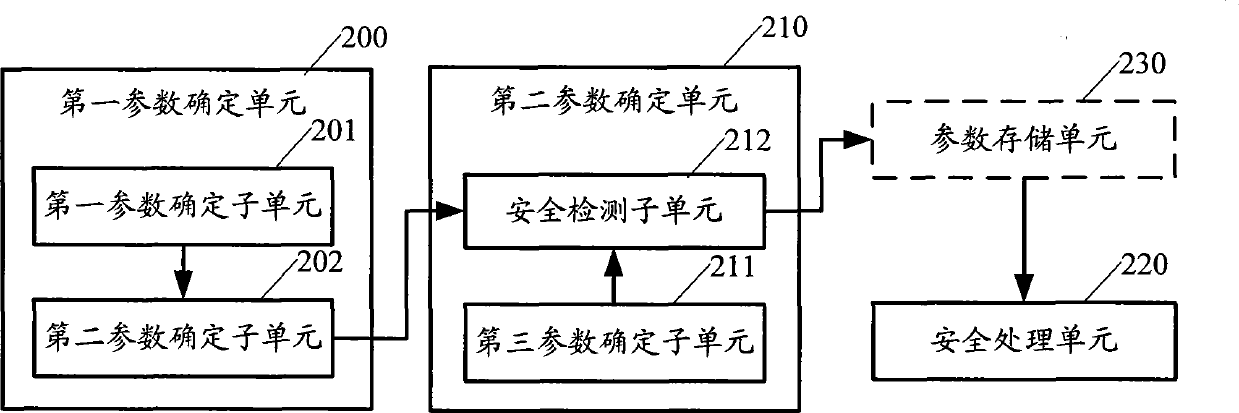
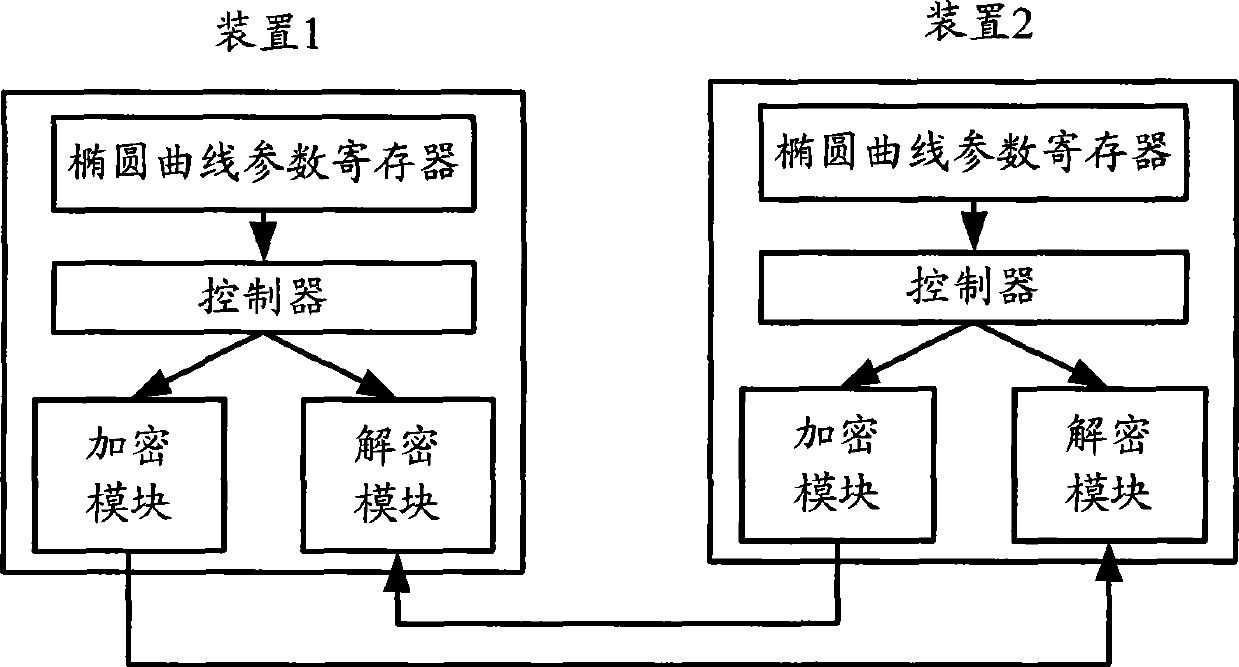
[0025] The method provided by the present invention mainly includes: determining in the finite field of the elliptic curve that satisfies The prime number of is used as the value of the parameter p; among them, h is the number of processing digits of the security processing system, hm meets the requirement of encryption digits of the security system, m>n, and both m and n are integers, a k ∈{-1, 0, 1}; use the determined parameter p to determine other elliptic curve parameters, and use the determined elliptic curve parameters to perform data security processing.
[0026] Describe above-mentioned method in detail below in conjunction with specific embodiment, figure 1 The method flowchart provided for the embodiment of the present invention, such...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com