Fixed hardware security unit backup and recovery method and system
A technology of hardware security and recovery method, the redundancy applied in the operation is used for data error detection, response error generation and other directions, which can solve the problem that attackers leave backdoors, cannot synchronize hardware security units and restore, and affect hardware security units. Firmness and other issues to achieve the effect of overcoming inconsistencies in state information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
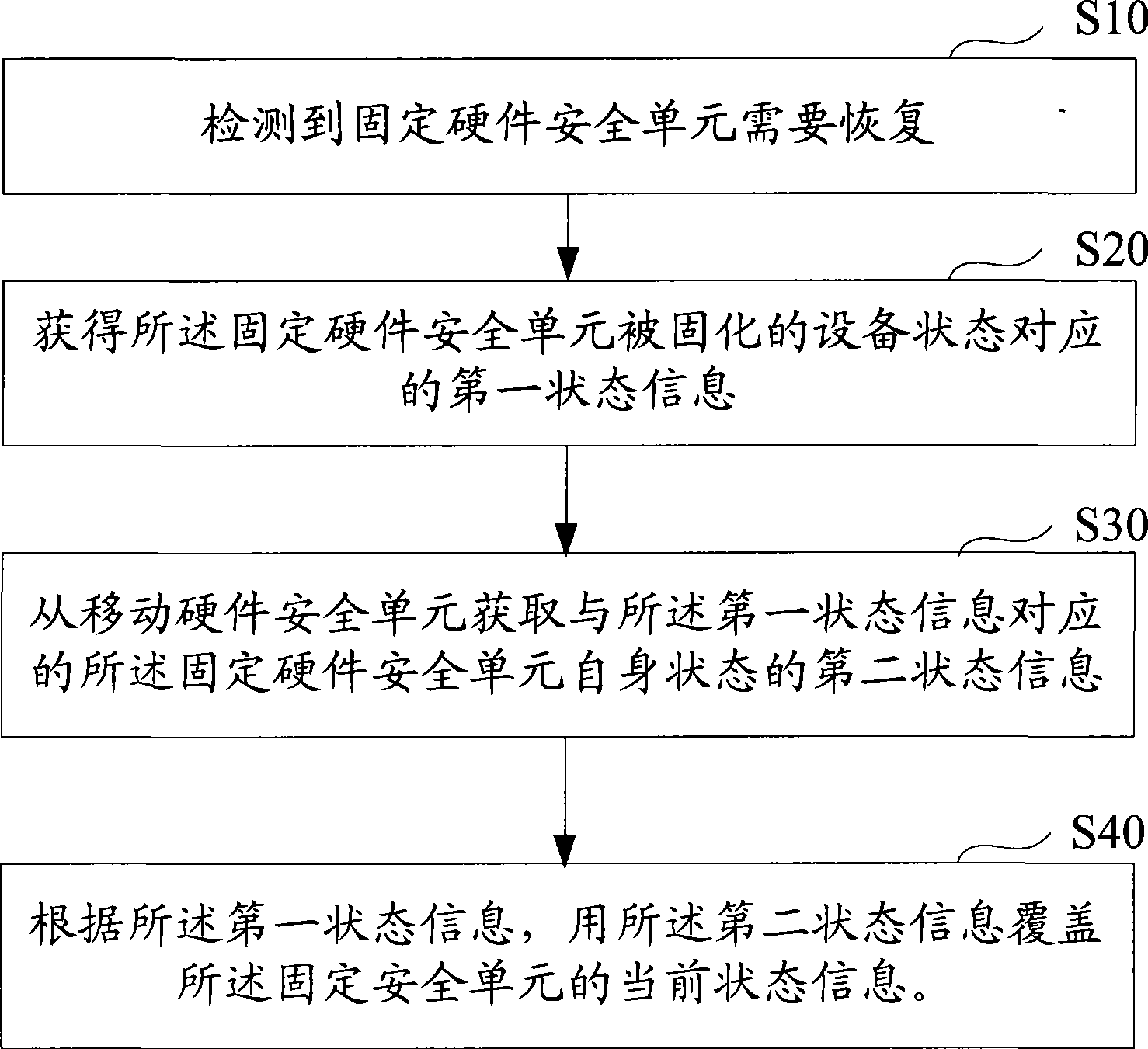
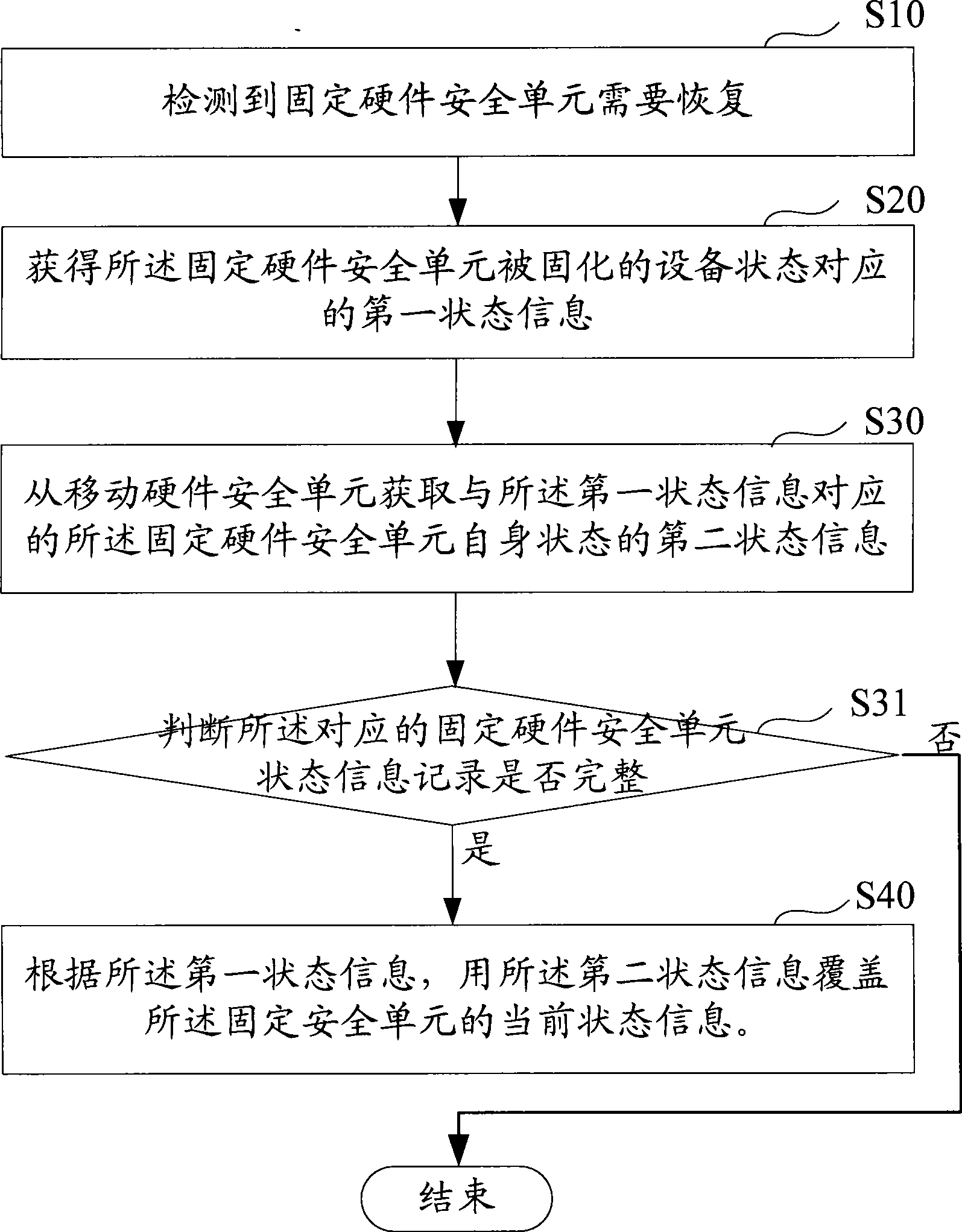
[0069] The present invention provides a backup and recovery method and system for a fixed hardware security unit, which is used to meet the requirement that the state information recorded by the fixed hardware security unit is consistent with the state information of its solidified computer equipment or other equipment.
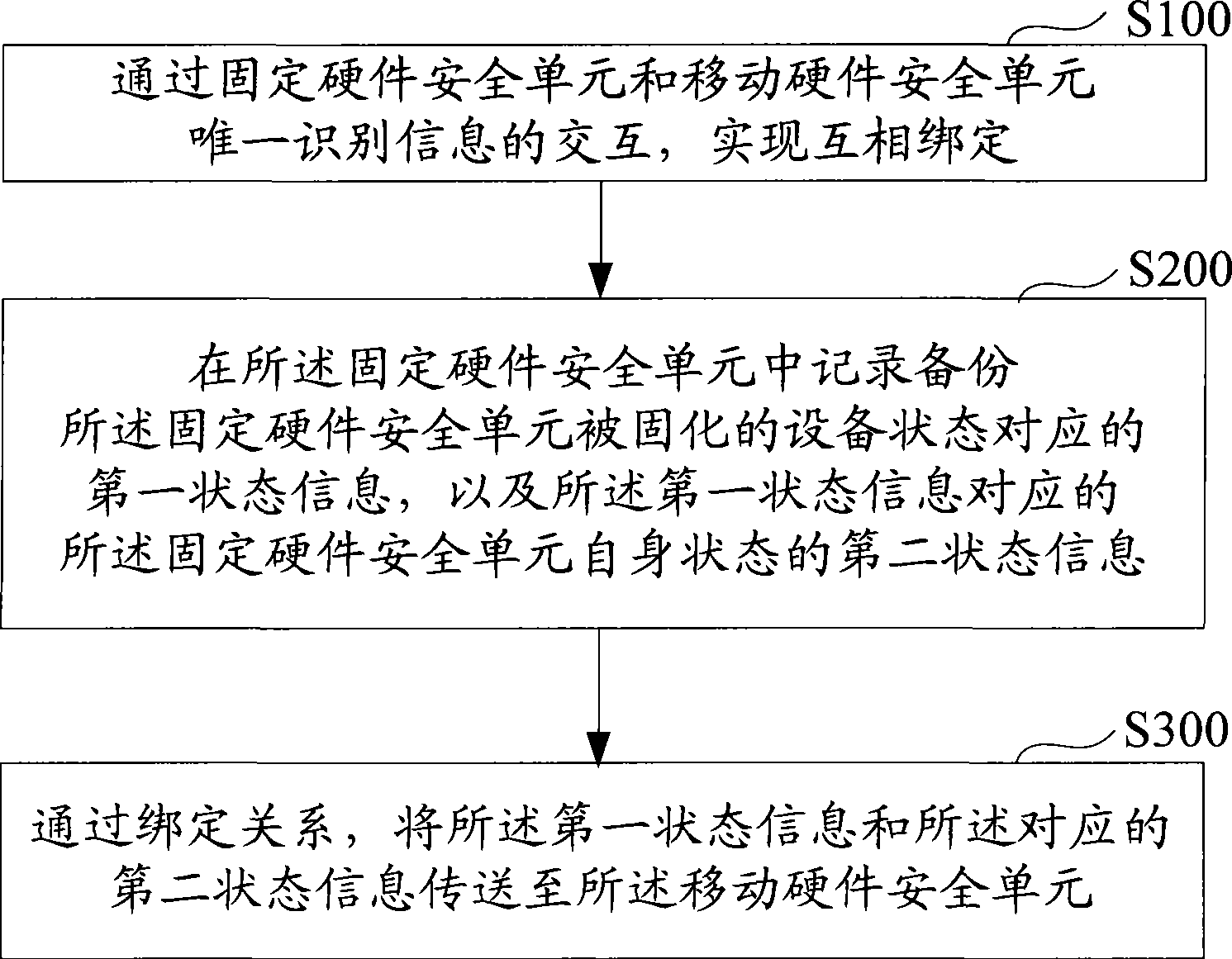
[0070] see reference figure 1 , which is a flow chart of the first embodiment of the method for backing up a fixed hardware security unit according to the present invention.
[0071] The fixed hardware security unit backup method described in the first embodiment of the present invention includes the following steps:
[0072] S100. Through the interaction of the unique identification information of the fixed hardware security unit and the mobile hardware security unit, mutual binding is realized.
[0073] The binding between the fixed hardware security unit and the mobile hardware security unit can be realized through the following steps:
[0074] S101. Set...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com