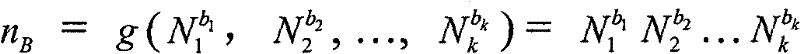mobile identification system based on nfc
An identification system and mobile terminal technology, applied in the fields of identity authentication and information security, can solve the problems of unification, inconvenience for commodity manufacturers and consumers, inability to identify the authenticity of commodities or authenticity identification, etc., to prevent anti-counterfeiting behaviors, The effect of preventing copying and preventing reuse
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] Embodiment 1: Select Elliptic Curve Digital Signature Algorithm
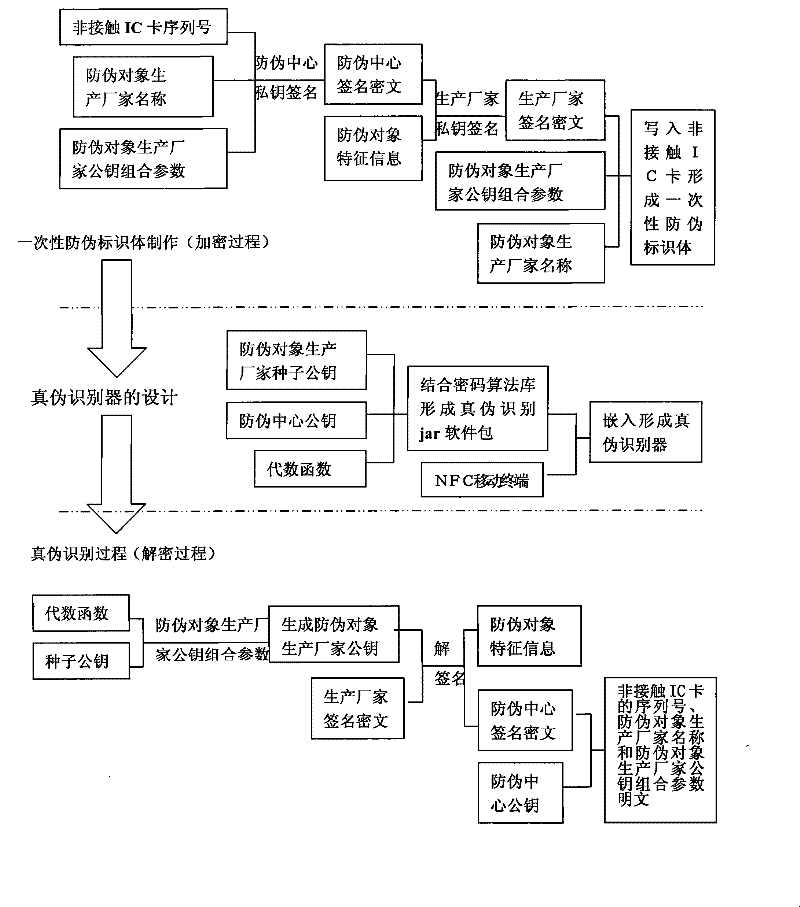
[0053]1. Making anti-counterfeiting identification body
[0054] The anti-counterfeiting method of the invention uses the non-contact IC card as the carrier of the anti-counterfeiting identification information, and the anti-counterfeiting identification body is an integral body composed of the non-contact IC card and the anti-counterfeiting object. First of all, according to the needs of the anti-counterfeiting object, the non-contact IC card is made into a shape and size suitable for the anti-counterfeiting object, and then the non-contact IC card is integrated with the anti-counterfeiting object. Once the non-contact IC card leaves the anti-counterfeiting object, it will be Physical or technical methods damage the non-contact IC card, so that the digital signature in the non-contact IC card can no longer be read and utilized, preventing the non-contact IC card from being reused.
[0055] 2. Key combin...
Embodiment 2
[0119] Embodiment 2: Select RSA digital signature algorithm
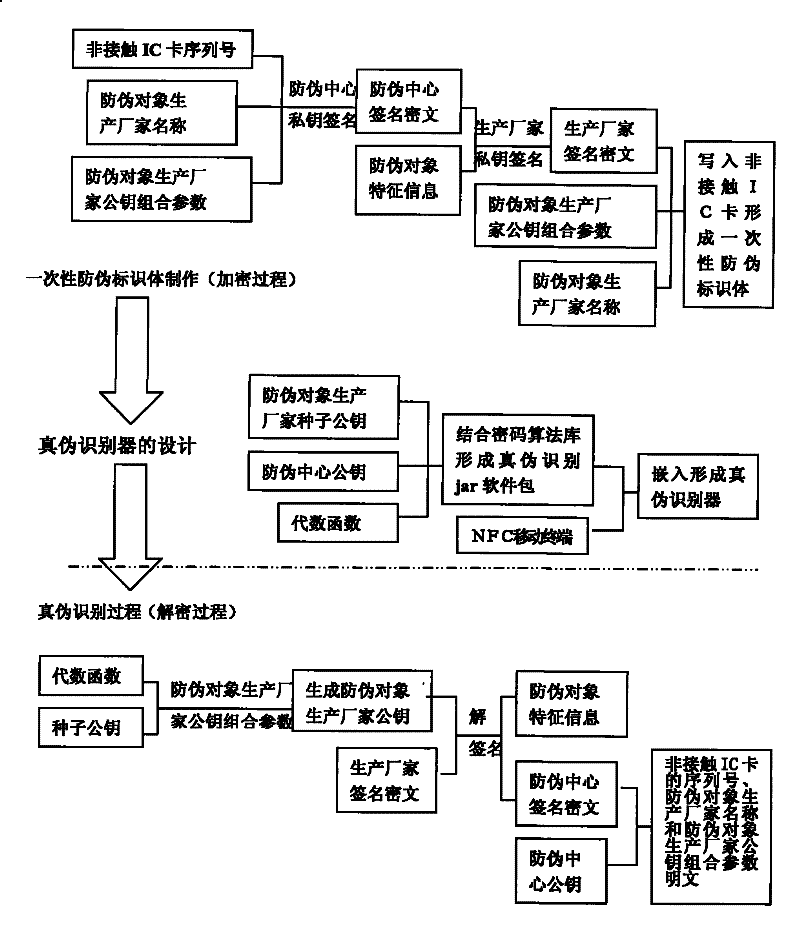
[0120] 1. Making anti-counterfeiting identification body
[0121] The anti-counterfeit method of the invention uses the non-contact IC card as the carrier of the anti-counterfeit identification information, and the anti-counterfeit identification body is an integral body composed of the non-contact IC card and the anti-counterfeit object. First of all, according to the needs of the anti-counterfeiting object, the non-contact IC card is made into a shape and size suitable for the anti-counterfeiting object, and then the non-contact IC card is integrated with the anti-counterfeiting object. Once the non-contact IC card leaves the anti-counterfeiting object, it will be Physical or technical methods damage the non-contact IC card, so that the digital signature in the non-contact IC card can no longer be read and utilized, preventing the non-contact IC card from being reused.
[0122] 2. Key combination process
[0123...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com