Trojan horse virus scanning method based on WEB page
A virus scanning and WEB server technology, applied in the field of virus scanning, can solve problems such as server threats, and achieve the effect of improving real-time performance and reducing labor management costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
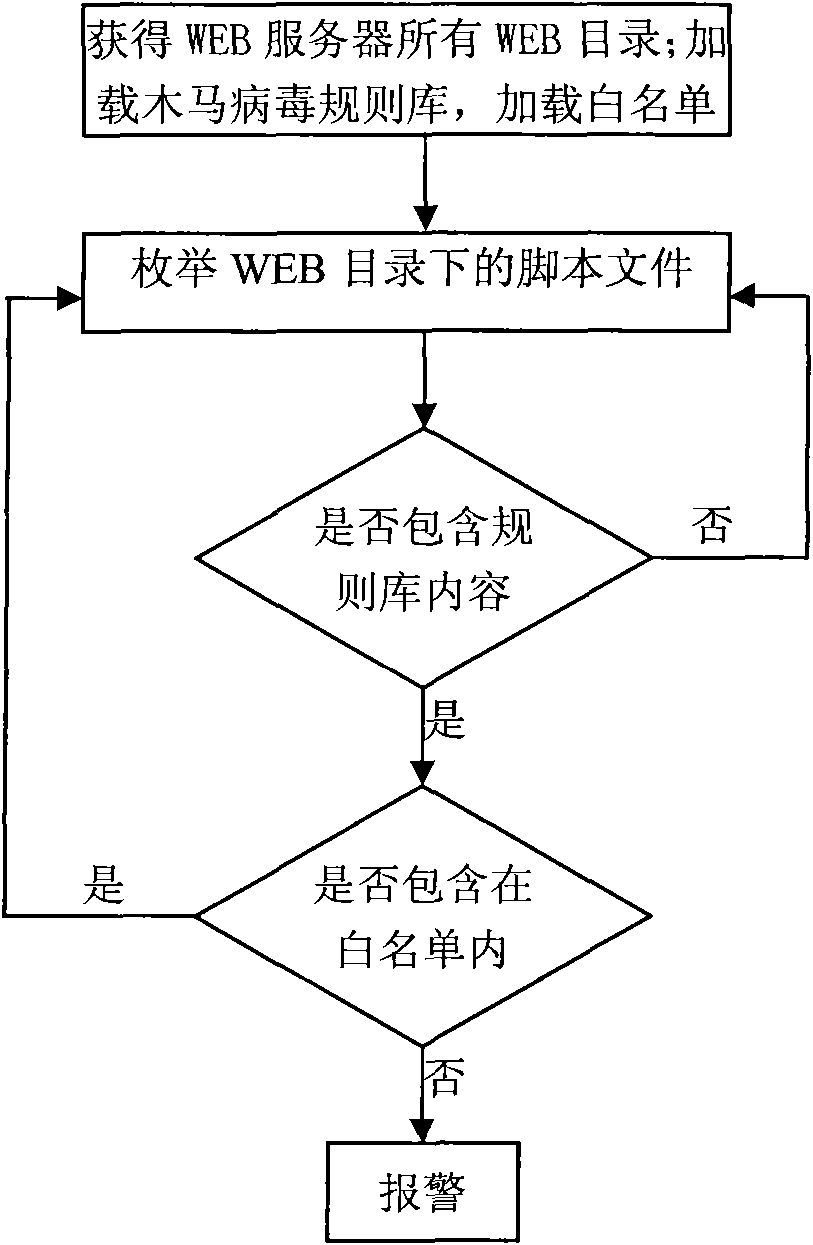
[0013] An embodiment of the Trojan virus scanning method based on WEB pages of the present invention is as follows: figure 1 As shown, the Trojan horse virus scanning tool is installed on the WEB server side, and the webpage Trojan horse virus files uploaded maliciously by hackers or utilizing WEB vulnerabilities to write are scanned. When there is a characteristic word containing a web page Trojan horse virus in the script file, it will alarm and output the information to a text file. Include the following steps:
[0014] 1. Obtain all WEB directories (including site directories and virtual directories) based on WINDOWS+IIS (that is, the platform is WINDOWS operating system and IIS WEB engine) or LINUX; search for Trojan horse virus samples in scripting languages such as ASP, JSP, PHP, and ASPX , extracting the Trojan horse virus rule base information, loading the Trojan horse virus rule base and the white list according to the Trojan horse virus rule base information;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com