Implementation method of security event monitoring in security center system
A security center, security event technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of asynchronous monitoring, information blockage, information cannot be shared, etc., to achieve the effect of broad application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
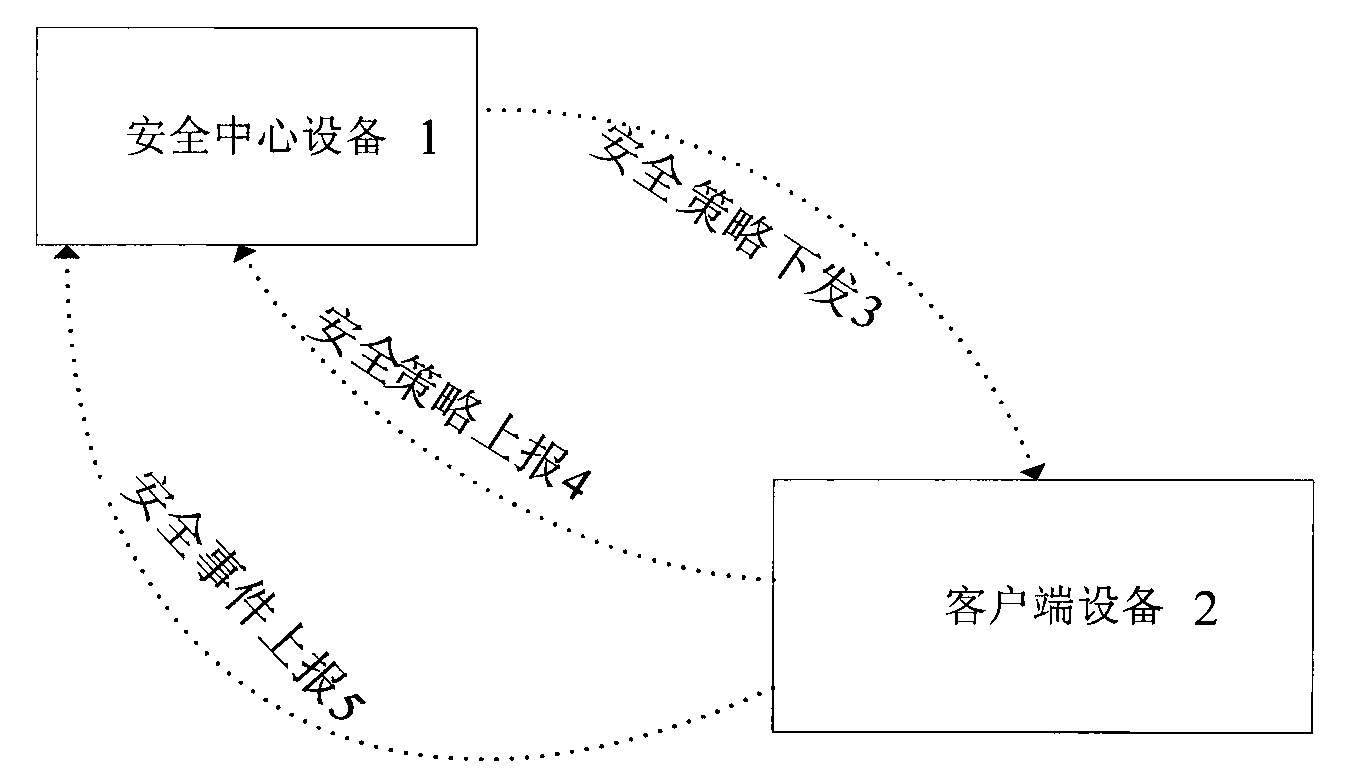
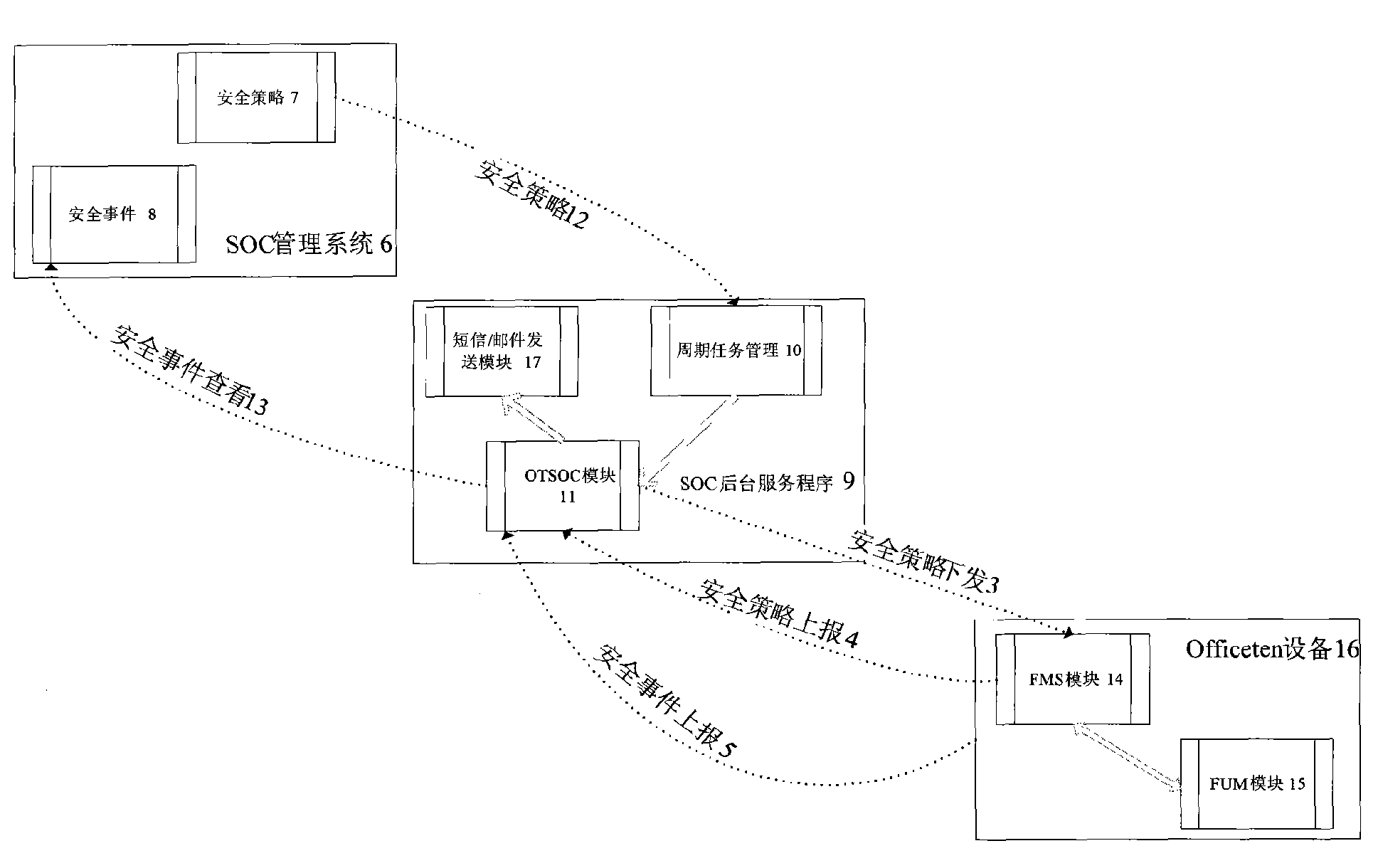
[0026] The implementation method of security event monitoring in the security center system uses SOCKET to realize the server / client two-way connection technology, and the processing of data services is divided into two categories: the server issues security policies, and the client receives security policies from the server. Report the local security policy to the server. When the terminal triggers a security event, it will report the triggered security event in real time.
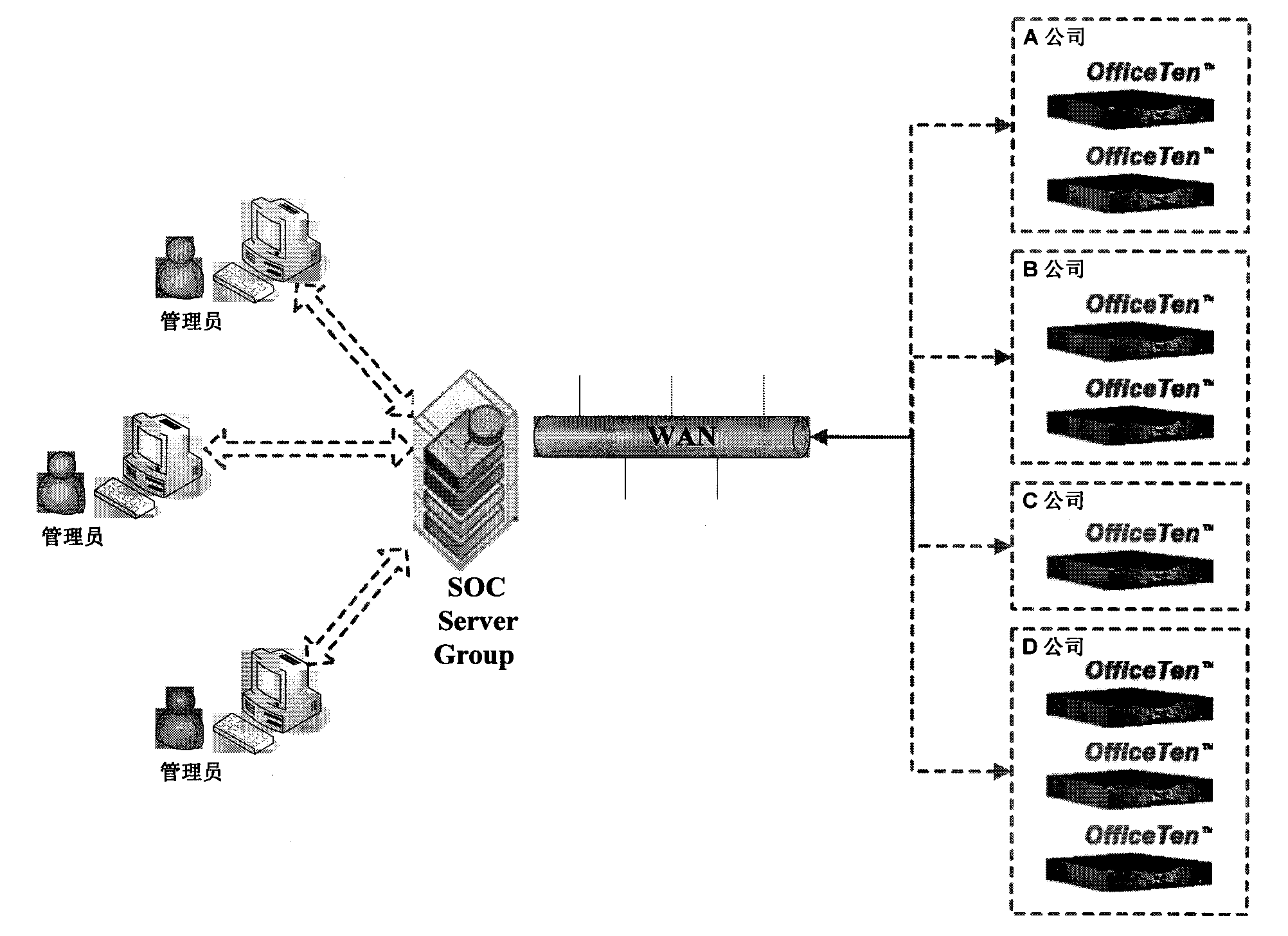
[0027] The design framework of the distributed network behavior real-time monitoring system based on the B / S model, the monitoring equipment reports security events to the security center in real time, the security center issues security policies to the monitoring equipment, and the security center analyzes the security events and notifies the relevant management personnel. Multiple monitoring devices are connected to the security center, and the security event monitoring is divided into two parts. One is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com