Encryption method based on virtual optics and device therefor
An encryption method and optical technology, applied in the field of information security, can solve problems such as the inability to apply PKI, the inability to effectively prevent data forgery and tampering, and the inability to achieve data integrity authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] Attached below Figures 1 to 4 Embodiments of the present invention will be described in detail.
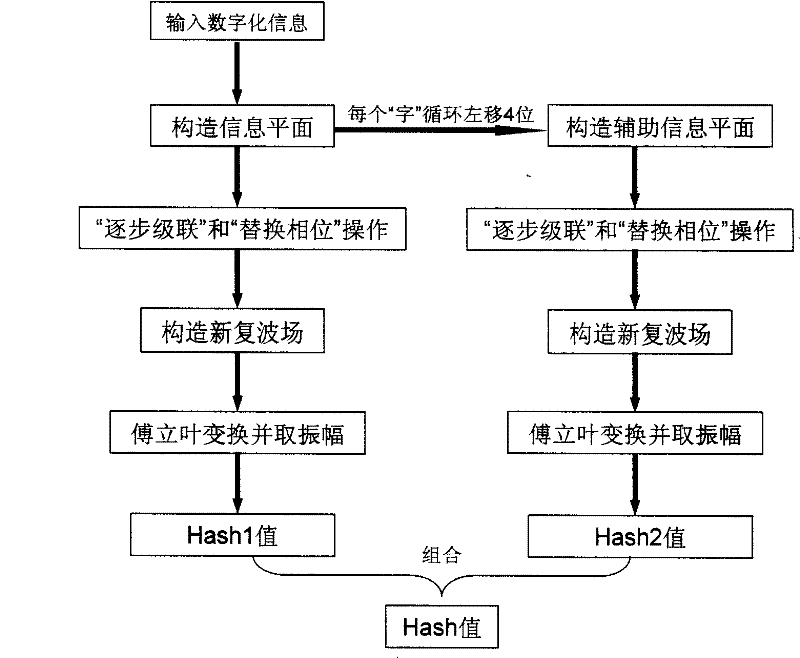
[0072] figure 1 The flow principle of the method of the present invention is shown. Proceed as follows:
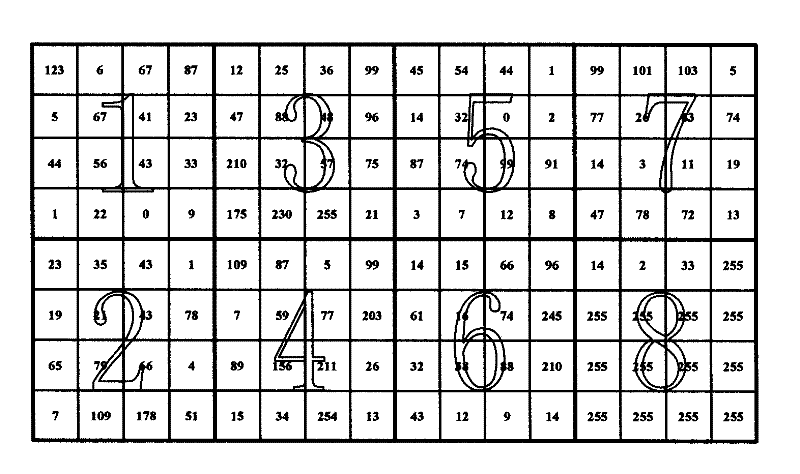
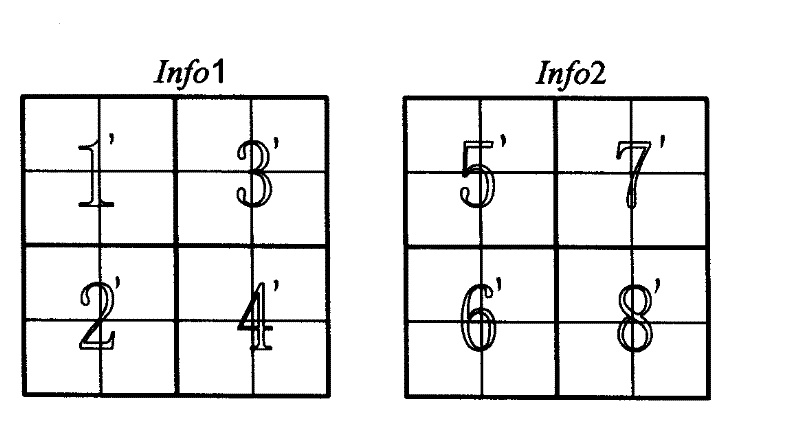
[0073] 1) if figure 2 As shown, construct the digital information plane Info: Divide the digital information to be processed into 128bit integers, and finally fill all the data blocks less than 128bit with 1, construct an even number of data blocks, or construct an odd number of data blocks and then add a full The 128bit data blocks of 1 form an even number of data blocks; then the even number of data blocks are divided into two rows to finally construct two rows of 4×4×N numerical matrices, where the value of N depends on the length of the digitized information, and each data The block is 128bit, and a 4×4 numerical matrix matrix is formed with an 8bit "unsigned word" as the minimum unit.
[0074] Taking the processing of 1024bit data (the last 104bits are all...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com