Safety management method and safety management system of virtual safety management center
A technology of security management and central server, which is applied in the field of intranet security management, can solve the problem of not analyzing and processing information, and achieve the effect of flexible formulation, security guarantee, and solution to the burden of management equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
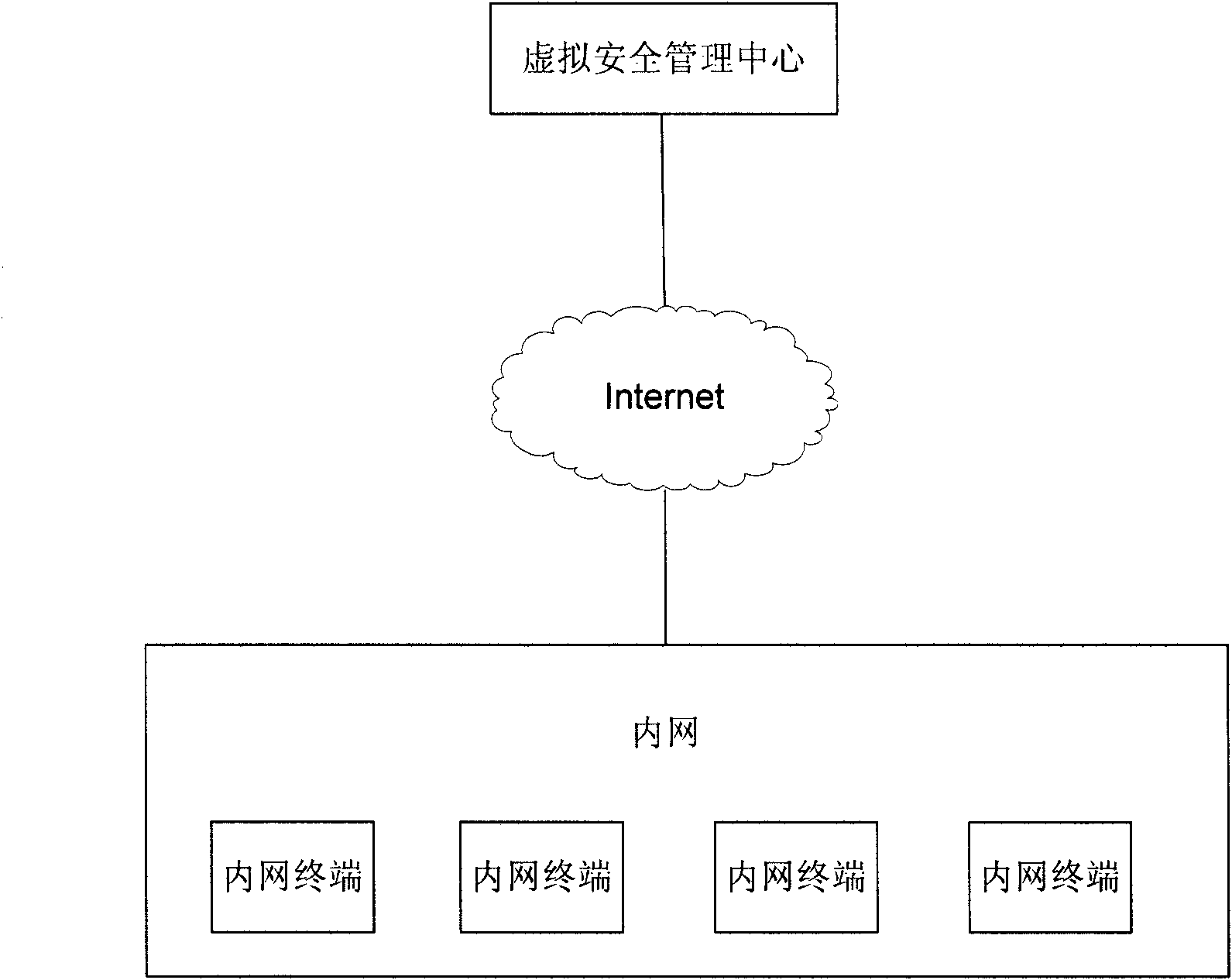
[0024] exist figure 1 Among them, the virtual security management center is connected to the Internet, all or part of the terminals in the intranet can be connected to the Internet, and one or more of them are connected to the virtual security management center through the Internet.
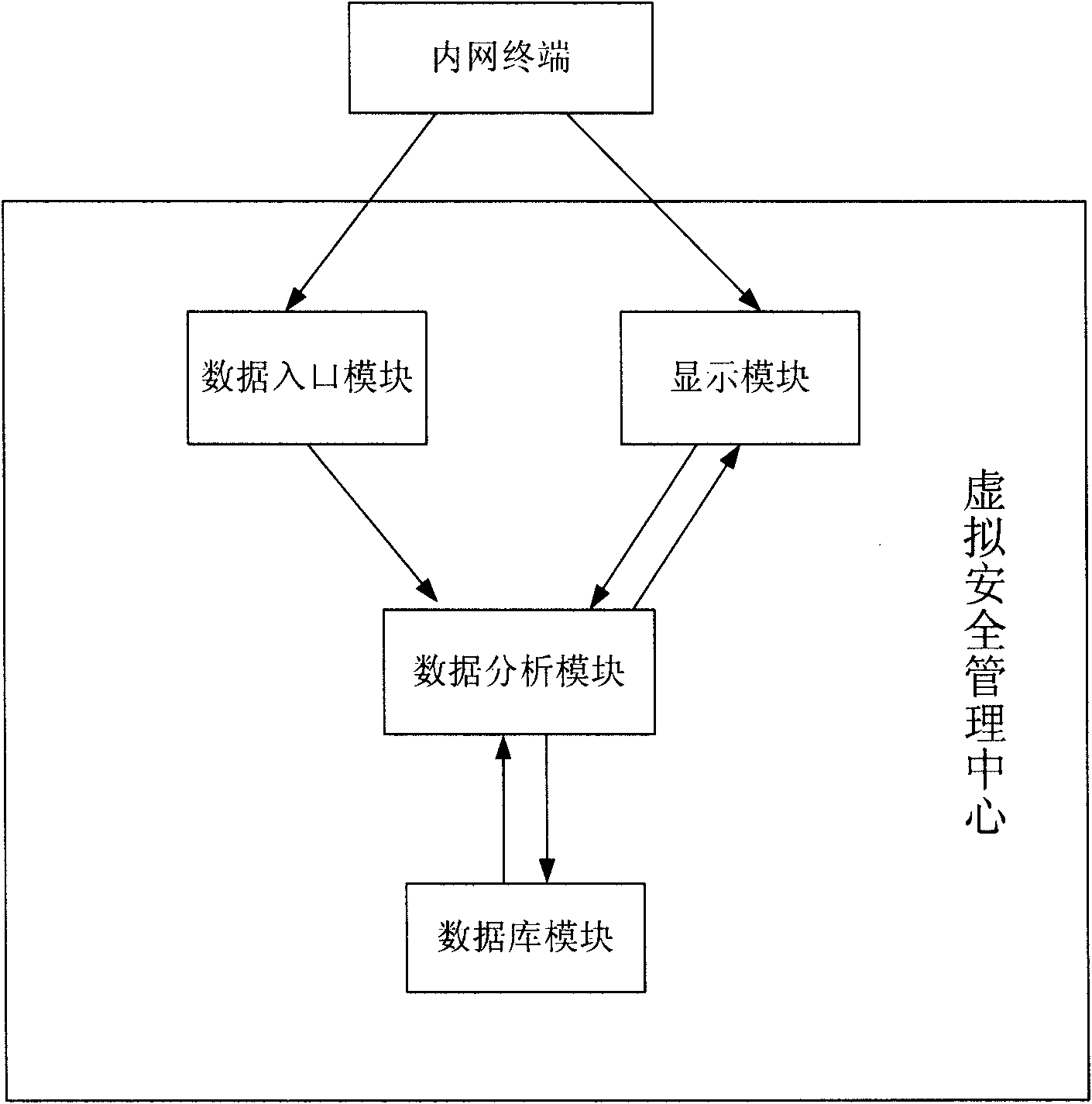
[0025] exist figure 2 In the above, a terminal in the intranet sends virus data to the virtual security management center, and the data entry module is used to receive the data sent by the intranet terminal. These data information are entered into the virtual security management center from the data entry module and then handed over to the data analysis module. Analysis, after the data analysis module obtains the data information of the intranet terminal, it will perform statistics, analysis, judgment and classification processing on it, and store the final complete information into the database module.
[0026] When you need to view and manage security information and terminals, log in to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com