Method and device for detecting buffer overflow and code instrumentation method and device
A buffer and code technology, used in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of wasting time and high false alarm rate, and achieve the effect of reducing false alarm rate, improving pertinence and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
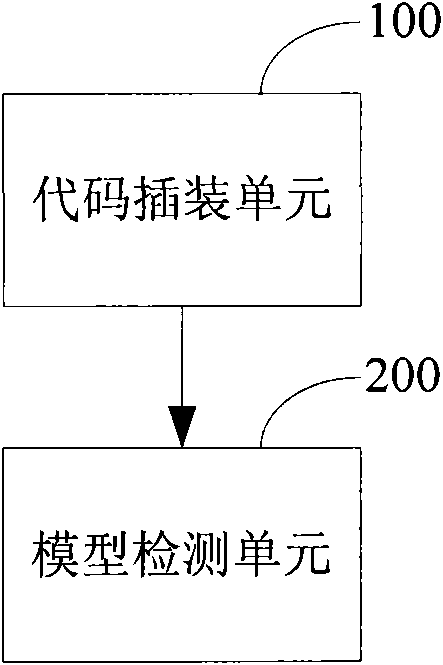
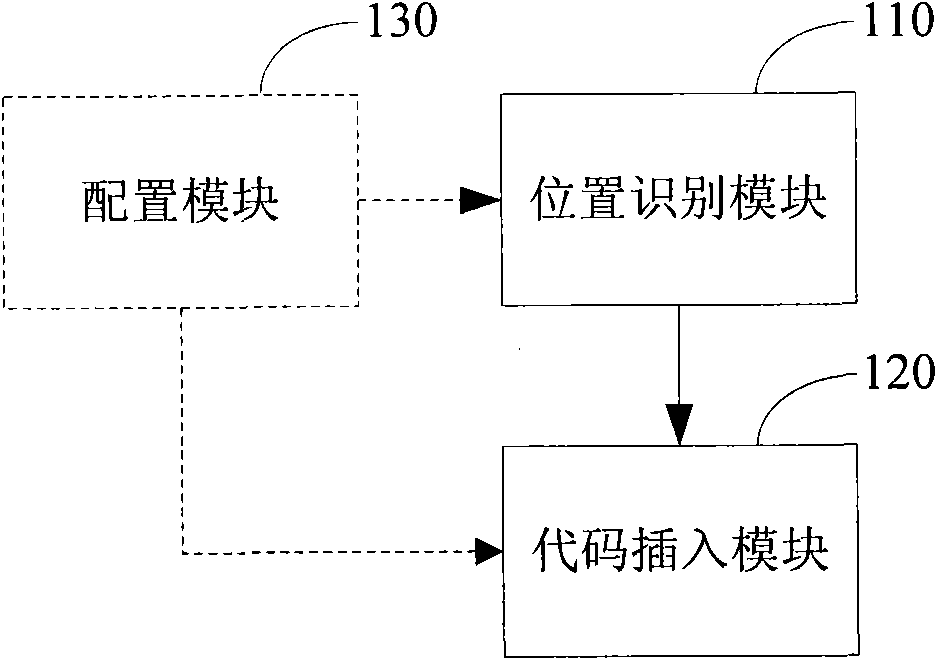
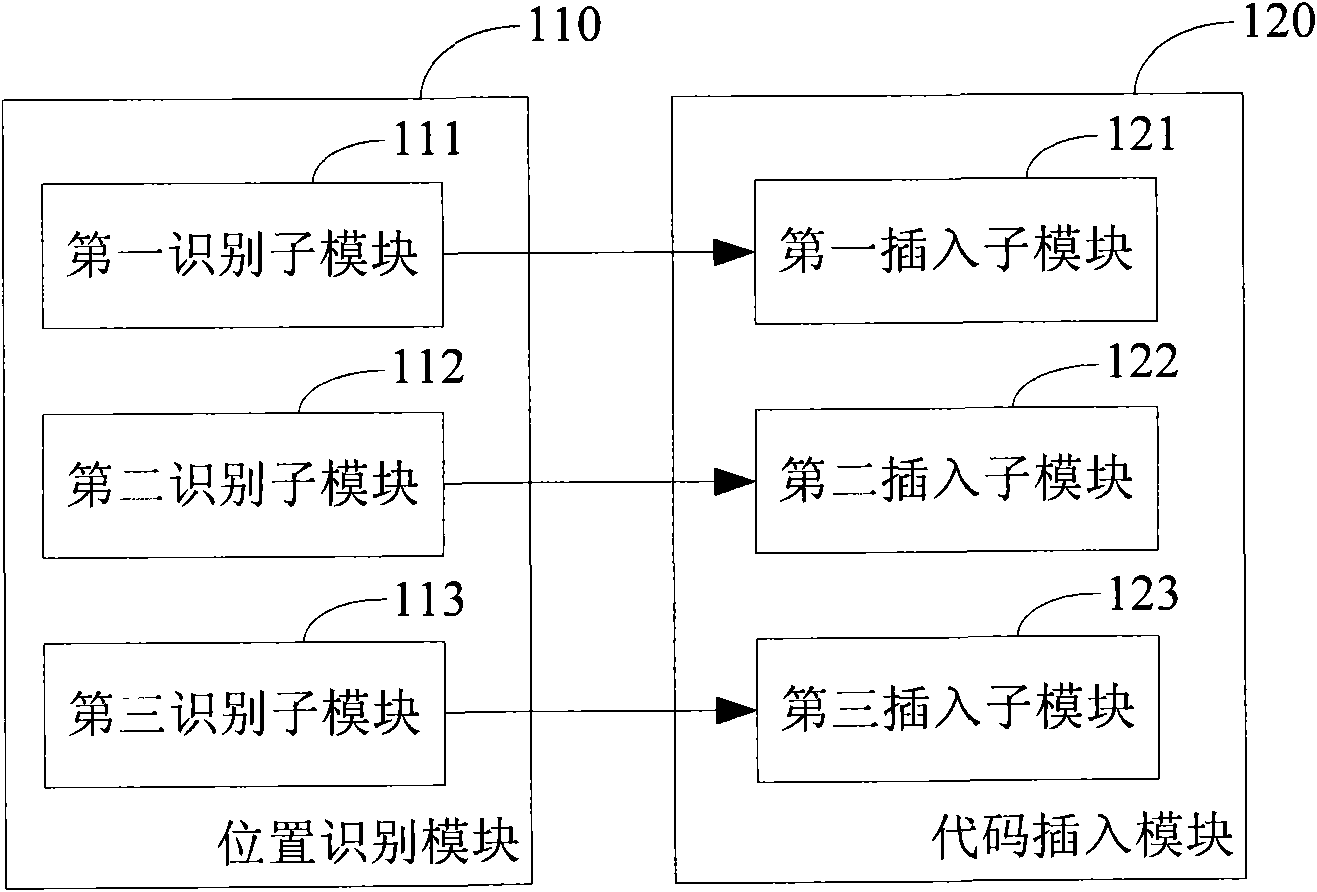
[0064] In the embodiment of the present invention, in order to detect the real loophole of buffer overflow, the program code can be model-tested, that is, the program code can be virtually executed, the program code can be converted into a finite state machine, and the program code in the finite state machine The state space of the system is exhaustively searched to determine whether there is a buffer overflow, and to find out the code execution trace that causes the buffer overflow. Wherein, the code execution trace that causes the buffer overflow refers to a collection of a series of codes of a certain execution path that causes the buffer overflow. However, in this process, when judging whether there is a buffer overflow, it needs to be judged according to the length information of the buffer. However, for these programming language codes that may have buffer overflow vulnerabilities, such as C / C++ codes, there is usually no Provide the length information of the buffer, suc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com