Method, device and system for authenticating terminal based on home base station network
A home base station and terminal technology, applied in the field of network communication, can solve the problems of RAND security risks, unfavorable users and communication counterparties, malicious user utilization, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example approach
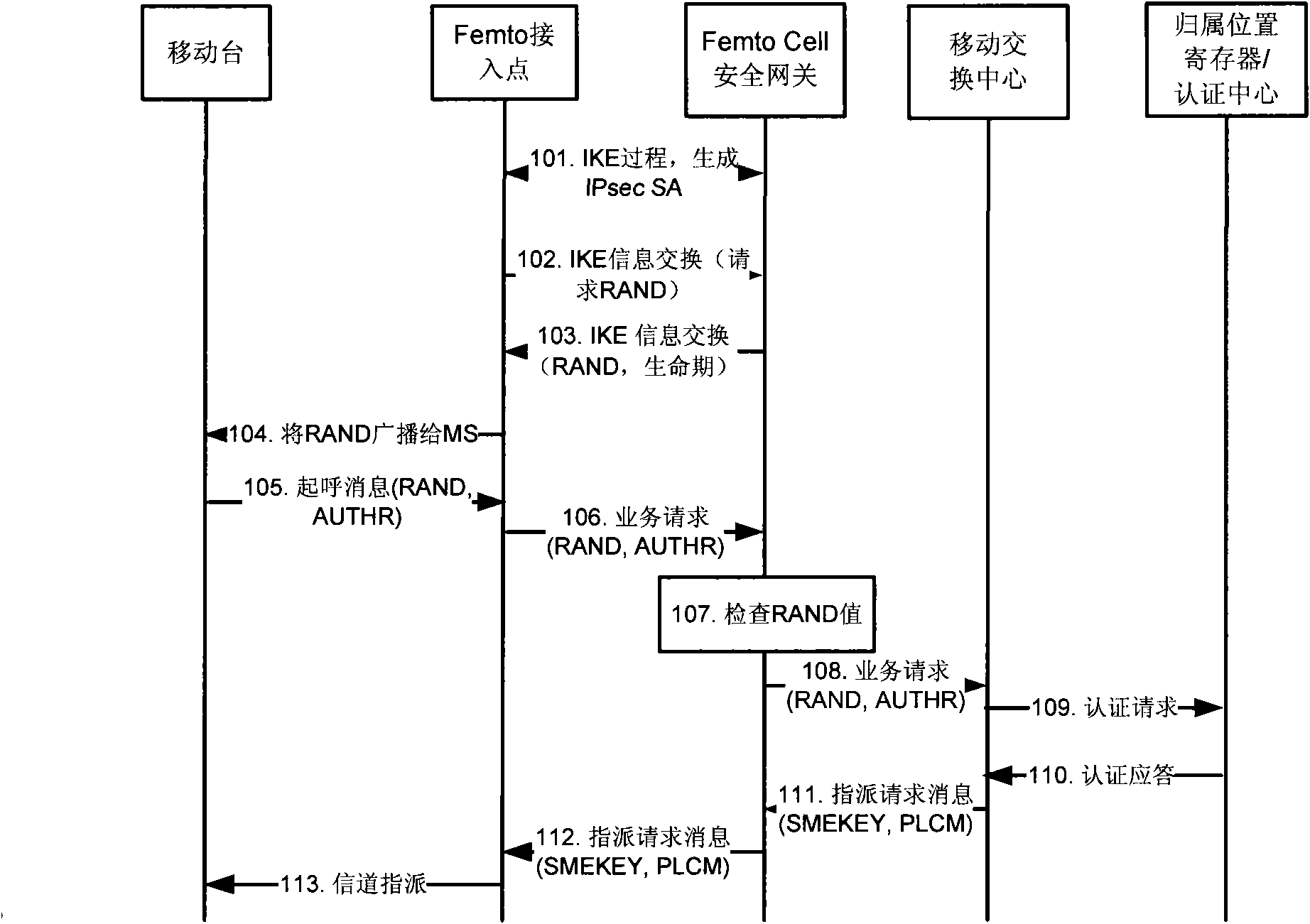
[0035] see image 3 , based on the method flowchart of the first embodiment of the present invention.
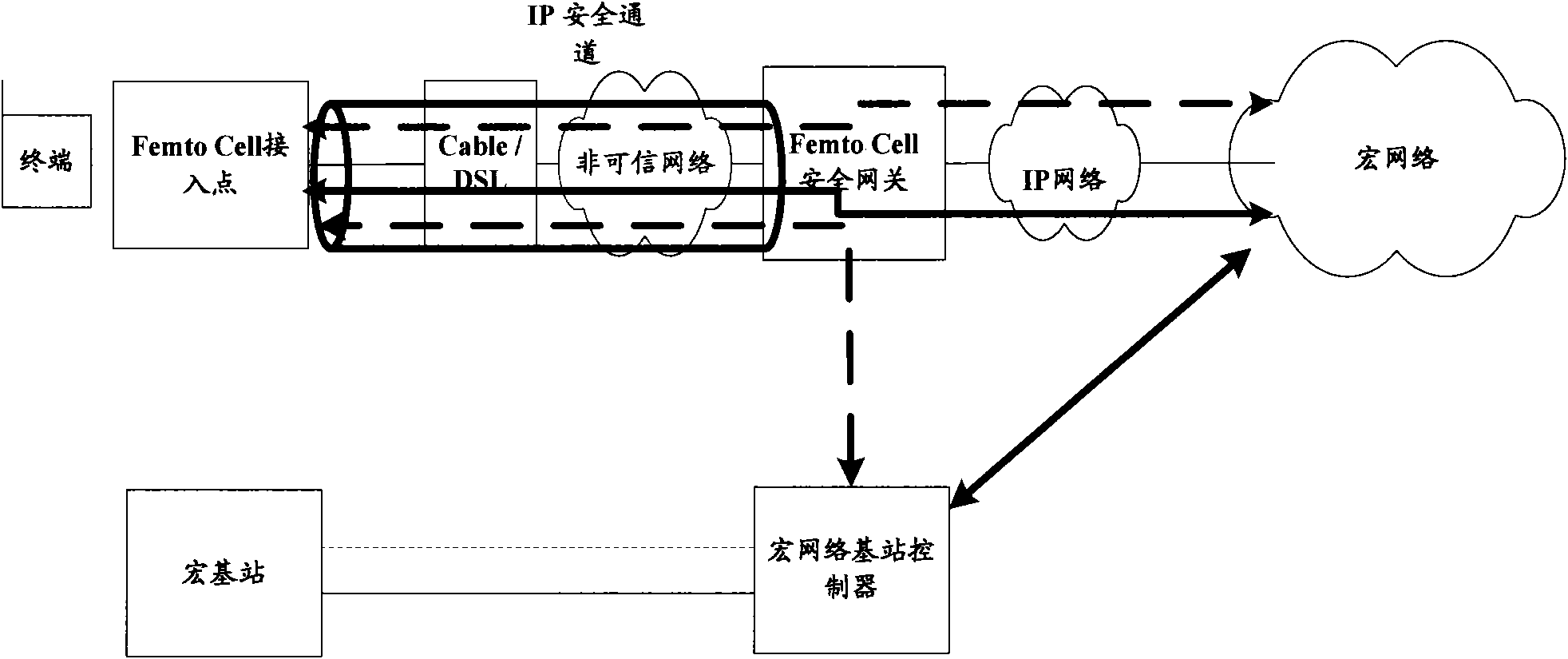
[0036] In the network structure of this embodiment, the external interface of the Femto Cell access point is the BSC and MSC interface, that is, the A1 / A1p interface, and the terminal is the MS. In this embodiment, the random number RAND is generated by the Femto Cell security gateway, and this method needs to extend the Internet Key Exchange message (IKE, Internet KeyExchange).
[0037] 101. In order to ensure the security of the Femto network signaling and user data transmitted by the Femto Cell access point and the Femto Cell security gateway, the Femto Cell access point first negotiates with the Femto Cell security gateway through the IKE protocol for IPsec security associations (SA, Security Association), and use the SA to protect signaling and user data.
[0038] 102. The Femto Cell access point requests the random number RAND from the Femto Cell security gateway thr...
Embodiment 2
[0053] see Figure 4 , based on the method flowchart of the second embodiment of the present invention.
[0054] Embodiment 2 is the processing flow when the RAND is different when the step 107 in the embodiment 1 checks, wherein the steps 201-206 are the same as the steps 101-106 in the embodiment 1, and will not be repeated here, only the subsequent processing flow is described. as follows:
[0055] 207. The Femto Cell security gateway sends the updated RAND to the Femto Cell access point through the IKE message.
[0056] 208. The Femto Cell access point broadcasts the RAND to the MS after receiving the RAND. The MS can resend the origination message, using the updated RAND. Its work flow is the same as that of Embodiment 1.
[0057] The IKE message in this embodiment is preferably an IKE information exchange message, and of course other types of IKE messages can also be selected to implement this method.
Embodiment 3
[0059] see Figure 5 , based on the method flowchart of the third embodiment of the present invention.
[0060] Same as Embodiment 1, in the network structure of this embodiment, the external interface of the Femto Cell access point is the BSC and MSC interface, that is, the A1 / A1p interface, and the terminal is the MS. Different from Embodiment 1, in this embodiment, the random number RAND is generated by the MSC, and this method needs to extend A1 / A1p.
[0061] Step 301 is the same as step 101 in Embodiment 1, and will not be repeated here.
[0062] 302. The Femto Cell access point requests a random number RAND from the MSC through an A1 / A1p message, where the A1 / A1p message carries an identifier (FAP ID, Femto Access PointIdentifier) of the Femto Cell access point.
[0063] 303. The MSC generates a RAND, and sends the RAND and the lifetime of the RAND to the Femto Cell access point through an A1 / A1p message.
[0064] Steps 304-305 are the same as steps 104-105 in Embod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com