Realization method and system of computer network security communication
A computer network and secure communication technology, applied in the field of computer network secure communication implementation methods and systems, can solve problems such as insecurity, inability to meet the isolation and determinability of network services, and achieve strong isolation, enhanced predictability, Guaranteed effect of reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The following is an embodiment of the present invention:
[0020] Development Platform:
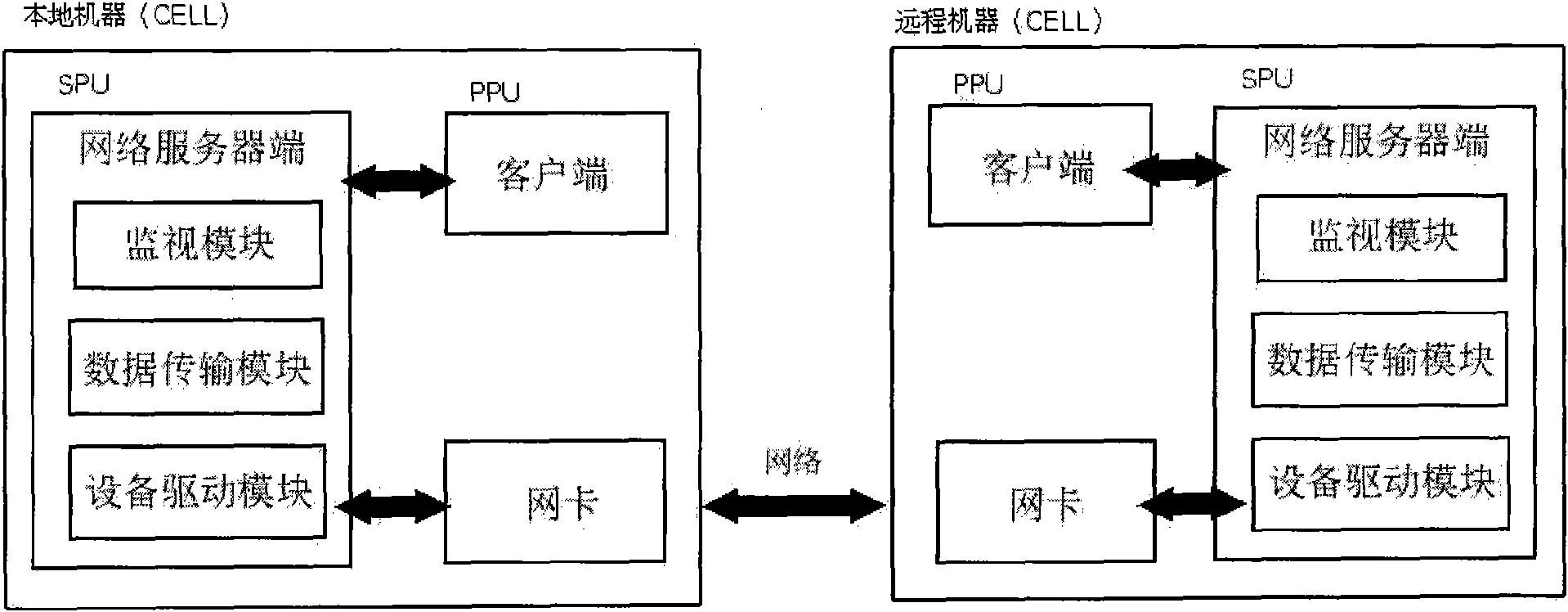
[0021] Hardware: Choose Playstation3 (PS3), whose core is CELL processor.
[0022] Software: choose Gentoo Linux as the operating system, use Git document version control software to manage documents, development language: C, assembly.
[0023] vim editor, PowerPC-gcc cross compiler.
[0024] Design ideas:
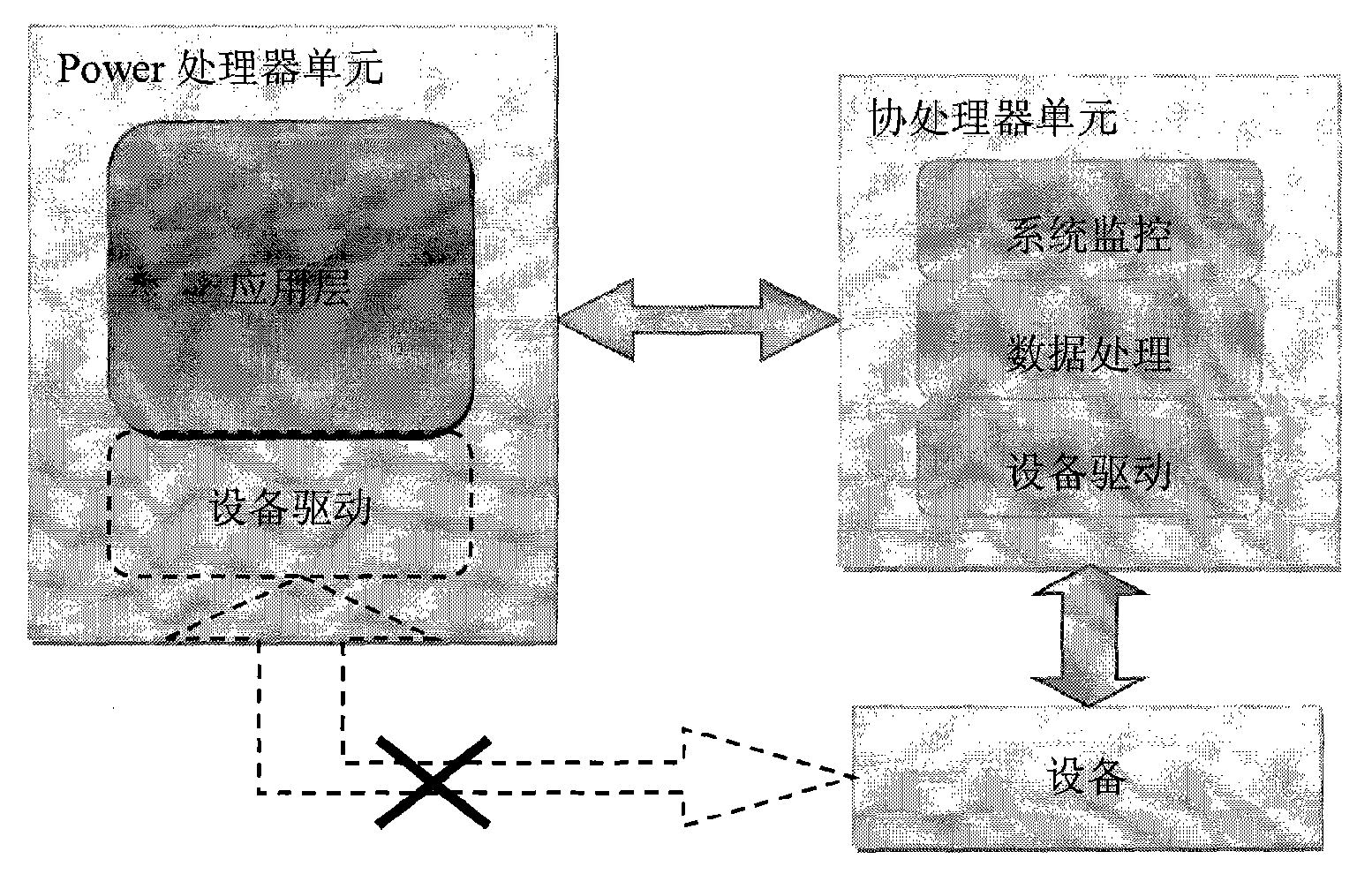
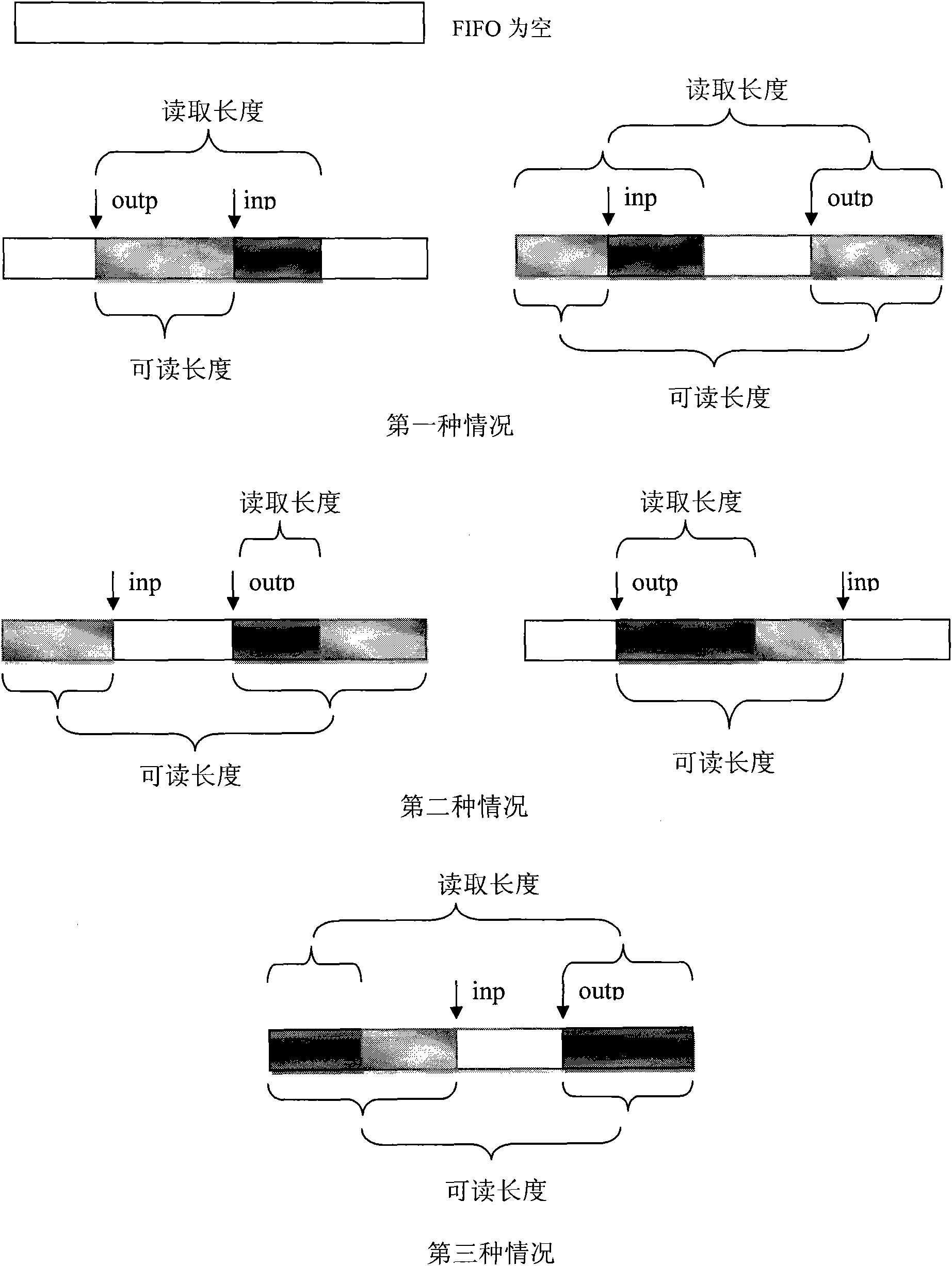
[0025] One processor is used as the application layer, and another co-processor is used as the server side. Considering the relevant constraints of the PS3 hardware and the testing and debugging issues for model building, the system was not run on a real hardware device: the coprocessor was designed to be able to simulate the hardware device with another coprocessor unit A hardware device that sends and receives data. Two fifos (fifo[1], fifo[2]) are used between the device driver module and the virtual device. The application module uses fifo[0] when receiving data from ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com