Method for solving IMS network DNS spoofing attack based on chaos encryption algorithm
A DNS spoofing and chaotic encryption technology, applied in the field of information security, can solve problems such as DNS spoofing attacks, and achieve the effect of ensuring real-time performance and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
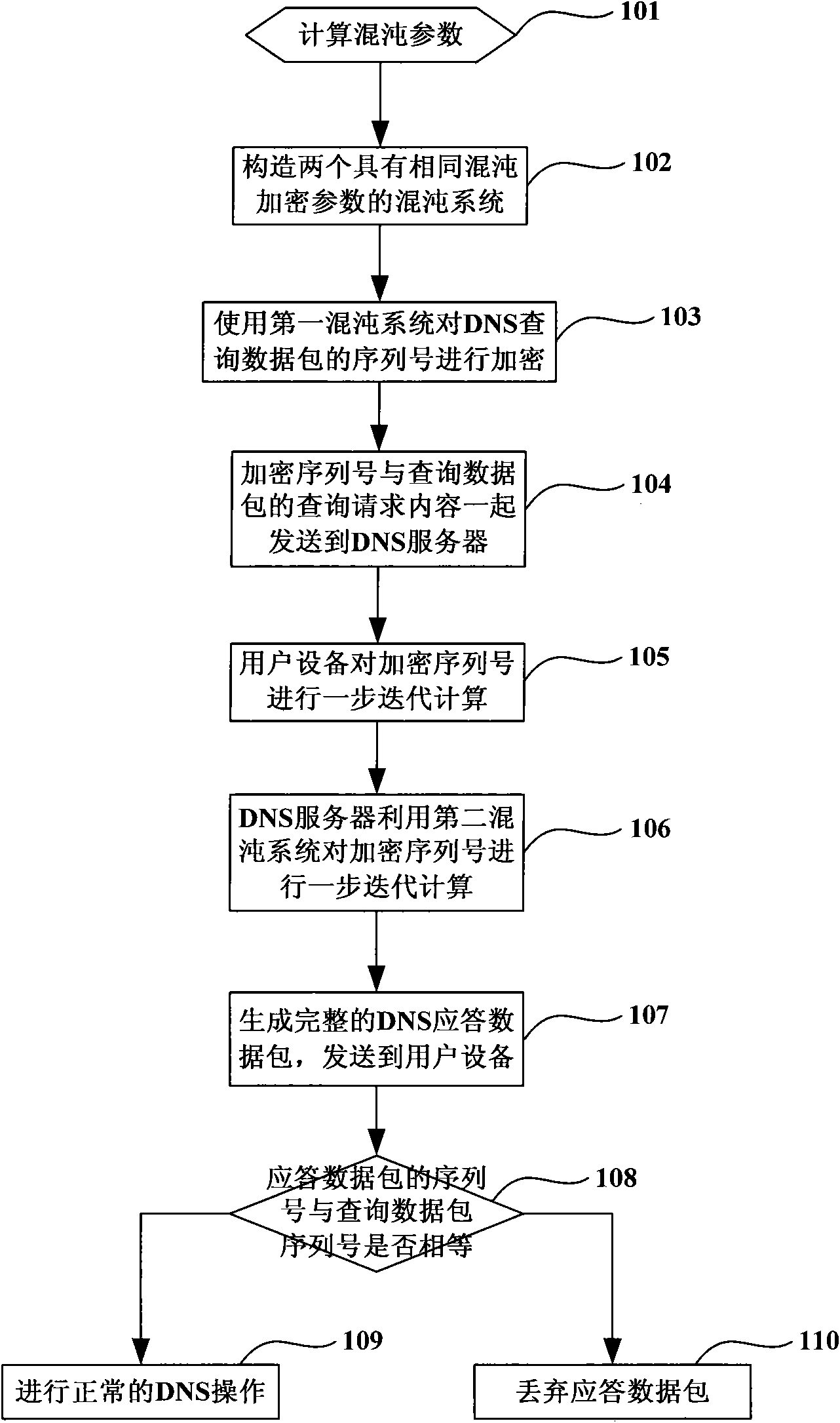
[0031] image 3 It is the flowchart of Embodiment 1 provided by the present invention. image 3 Among them, in the method for solving the DNS spoofing attack on the IMS network based on the chaotic encryption algorithm provided in Embodiment 1 of the present invention, the DNS query party specifically uses a user device, that is, a DNS terminal, and the user initiates a DNS query request; the DNS responder specifically uses a DNS server , the DNS server receives the query data packet sent by the user equipment and returns the query result. This embodiment specifically includes the following steps:
[0032]Step 101: When the user equipment initiates a DNS query request, firstly calculate the chaos parameter through the shared key K of the ISIM module.
[0033] As a DNS client, the user equipment can read the shared key from the ISIM module of the smart card. The smart card is the commonly used SIM card (Subscriber Identity Module, Subscriber Identity Module). To register use...
Embodiment 2
[0065] Figure 5 It is the flowchart of Embodiment 2 provided by the present invention. Figure 5 Among them, in the method for solving the DNS spoofing attack on the IMS network based on the chaotic encryption algorithm provided in Embodiment 2 of the present invention, the DNS query party specifically uses a DNS query server to initiate a DNS query request; the DNS responder specifically uses a DNS response server, It is used to receive the query packet sent by the DNS query server and return the query result. This embodiment specifically includes the following steps:
[0066] Step 201: When the DNS query server initiates a DNS query request, the DNS query server and the DNS response server use the key pair distributed by the IMS network domain SA (Security Association), through the formula Calculate the chaotic parameters, and construct chaotic systems with the same parameters on the DNS query server and DNS query responder respectively, which are respectively denoted as...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap