Method and system for accessing mobile IP service of CDMA2000 system
An access method and server technology, applied in the field of communications, can solve problems such as poor operability, poor scalability, and single security policy, and achieve the effects of avoiding connection difficulties, simplifying system configuration, and improving availability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
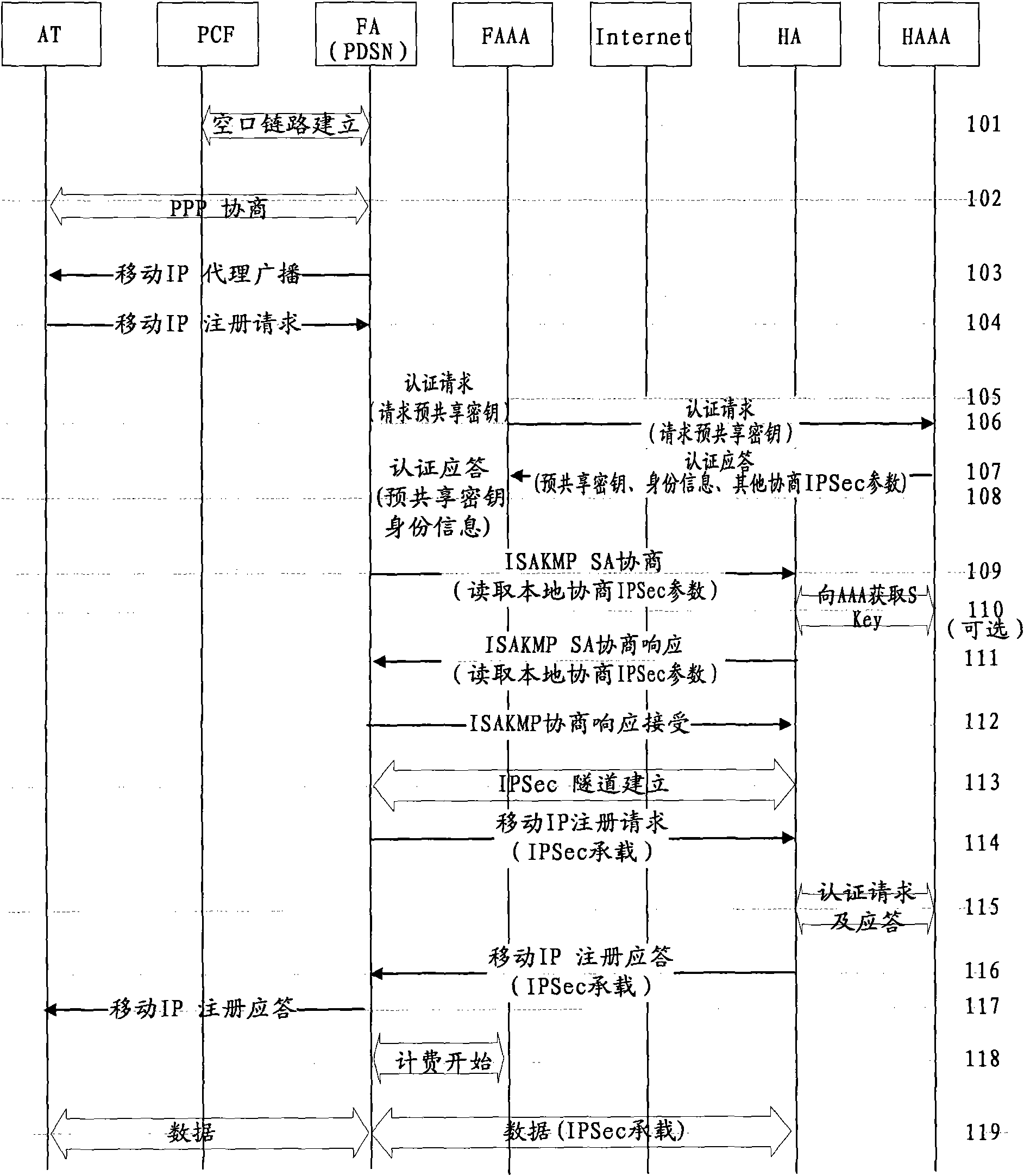
[0070] Such as figure 2 As shown, the access system of the CDMA2000 system mobile IP of this example, its CDMA2000 system mobile IP access method includes the following processing steps:
[0071] Step 201, PCF (Packet Control Function, packet control function subsystem) establishes an air interface link with the FA;
[0072] Step 202, the access terminal negotiates PPP (Point to Point Protocol, Point-to-Point Protocol) with the FA, and the FA sends a proxy broadcast to the access terminal;
[0073] Step 203, the access terminal obtains mobile IP related information through proxy broadcast;
[0074] Step 204, the access terminal initiates mobile IP registration to the FA;
[0075] Step 205, the FA sends an authentication request to the FAAA and requests a pre-shared password at the same time;
[0076] AAA includes HAAA (Home Authentication Authorization Accounting server) and FAAA (Foreign Authentication Authorization Accounting server), where HAAA is used to select and iss...
Embodiment 2
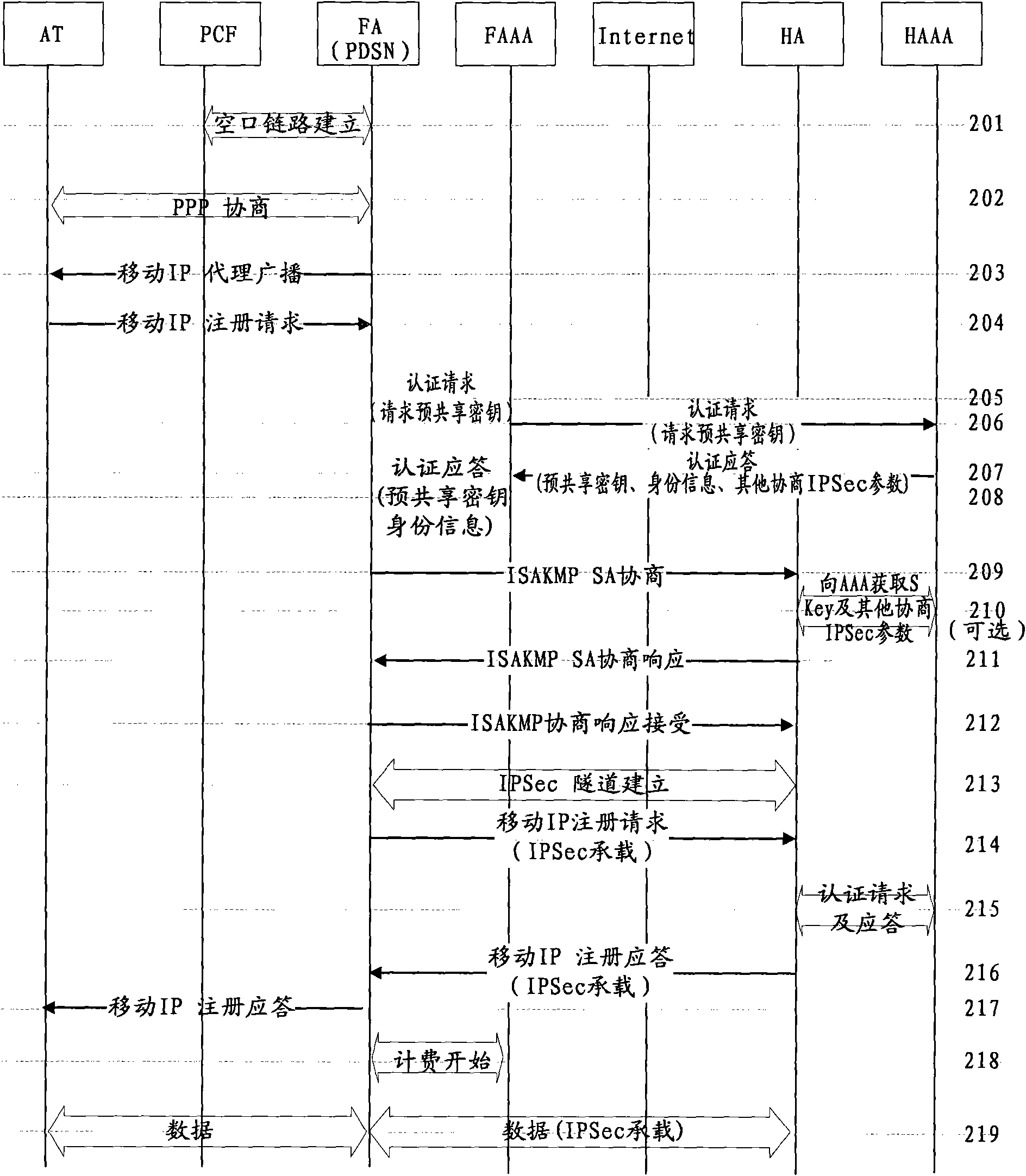
[0096] Such as image 3 As shown, in the second embodiment of the CDMA2000 system mobile IP access method of the present invention, the diversified security strategy includes the following steps:
[0097] Step 301, the access terminal accesses the CDMA2000 system, and the PCF establishes an air interface link with the FA; the access terminal negotiates PPP with the FA, and the FA sends a proxy broadcast to the access terminal; the access terminal obtains mobile IP related information through the proxy broadcast; the access terminal Initiate mobile IP registration; FA sends an authentication request to AAA and requests a pre-shared password at the same time;
[0098] Step 302, AAA provides different negotiated IPSec parameters according to the security level of the access terminal, that is, provides different levels of security policies, and sends them to the FA;
[0099] Security policies are reflected in different negotiated IPSec parameters. For example, the negotiated IPSe...
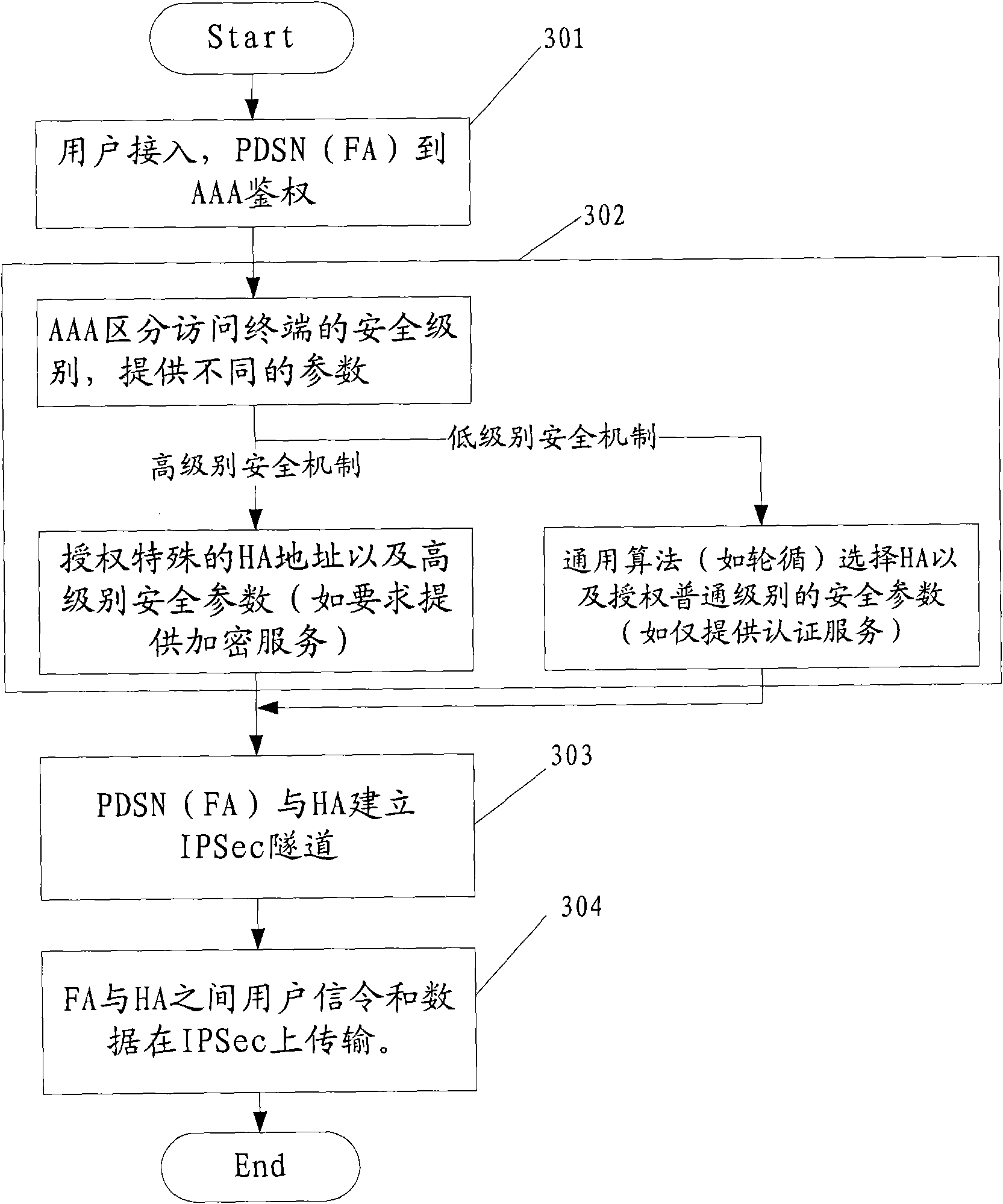
Embodiment approach
[0105] Step 207a, HAAA selects and sends an authentication response to FAAA according to the security level of the access terminal, the authentication response includes the profileID, pre-shared key, identity information, etc. corresponding to the negotiated IPSec parameters;
[0106] Step 208a, FAAA forwards the authentication response to FA;
[0107] Step 209a, the FA obtains the negotiated IPSec parameters locally according to the profileID corresponding to the negotiated IPSec parameters, and the FA sends a negotiation request for establishing an ISAKMP SA to the HA according to the information about the negotiated IPSec parameters, and the negotiation request for establishing an ISAKMP SA carries the proposed ISAKMPSA information , key material, and identity information;
[0108] Step 110a, after receiving the negotiation request established by the ISAKMP SA, the HA restores the FA address according to the identity information therein, and sends the request to obtain the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com