Identity recognition method based on user keystroke characteristic
An identification and keystroke technology, applied in the field of computer information security, can solve problems such as poor usability, complex deployment of identification technology, and high cost, and achieve high application and promotion value, high pass rate of legitimate users and high rejection rate of illegal users , The identification method is simple and effective
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
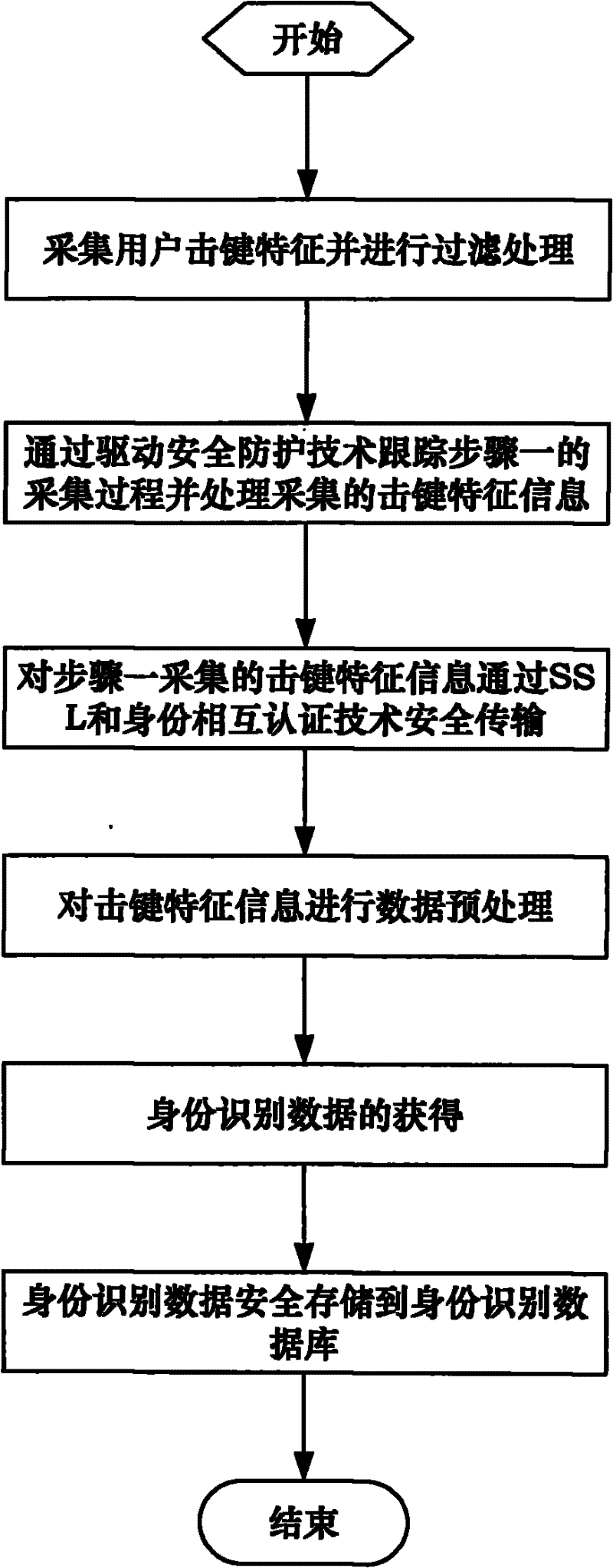
[0063] Applying an identity recognition method based on user keystroke features provided by the present invention, when registering a user, the specific flow of the recognition method is as follows: Figure 4 As shown, the steps are as follows:
[0064] Step 1. The user first enters a user name that meets the rules; then the user will enter the password multiple times according to the system requirements, for example, enter the password password 3 to 8 times;
[0065] Step 2, collect keystroke characteristic information of the user.
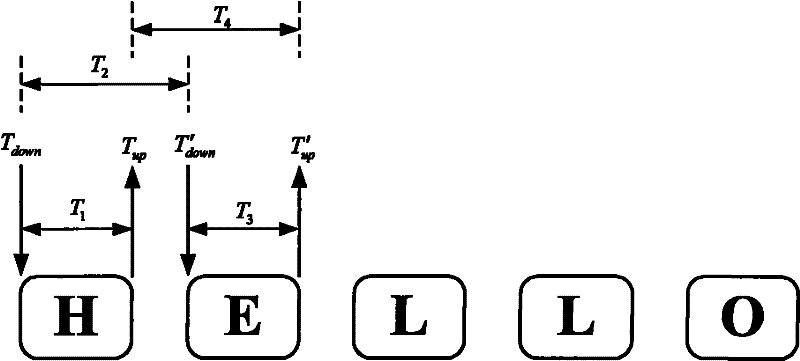
[0066] For the keystroke event when the user enters the user name and password, collect the user's dwell time T on each key 1 and the interval time T between adjacent keys 2 , as well as the keystroke strength and keystroke feature information meet the system requirements, the system will collect the user’s keystroke features according to a certain data format; For input, the dwell time T collected on each key 1 , the interval time between ad...
Embodiment 2
[0072] Applying the identification method based on the keystroke characteristics of the user provided by the present invention, the flow chart for user login identification is as follows: Figure 5 As shown, the specific steps are:
[0073] Step 1. The user accesses the system and performs user login;
[0074] Step 2. The system requires the user to enter the registered user name;
[0075] Step 3: The user enters the password used for registration;
[0076] Step 4. The system first verifies whether the user's password is correct. If the password is wrong, return to step 3 to re-enter the password; if the password is correct, the system continues to verify whether the user's keystroke characteristics are correct.
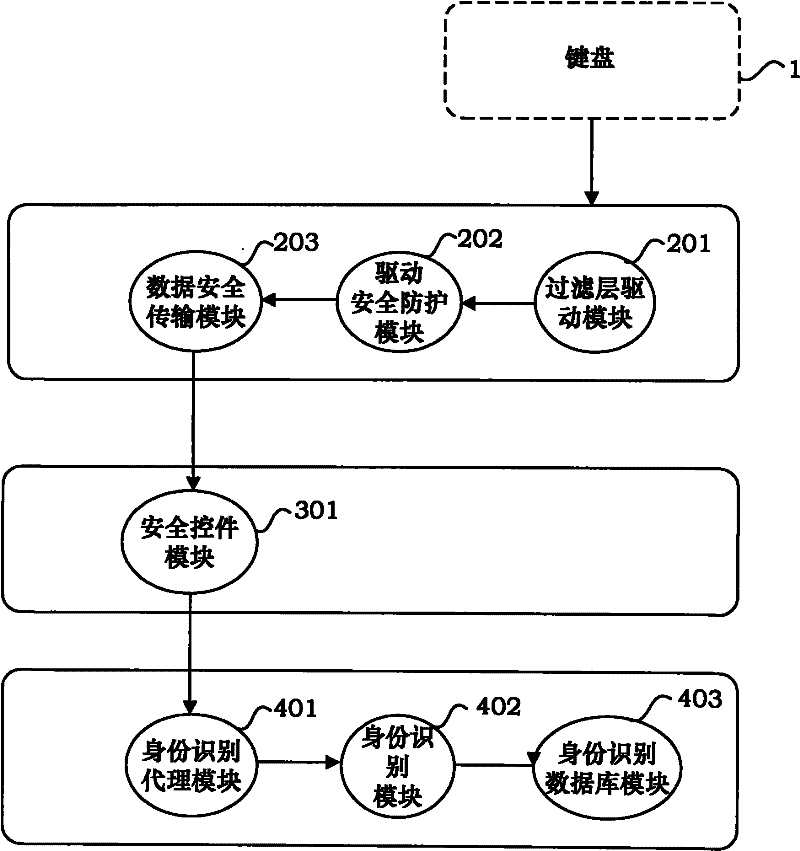
[0077] Step 5, the system collects the keystroke characteristic information of the user while the user inputs the user name and password, and matches the keystroke characteristic information with the identification data stored in the identification database module ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com