Method for detecting, tracking and identifying object abandoning/stealing event
A recognition method and object technology, applied in character and pattern recognition, computer parts, image data processing, etc., can solve the problems of monitoring personnel being unable to do it, monitoring, monitoring personnel's slack thinking, etc., to achieve real-time object retention/stealing The effect of event recognition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
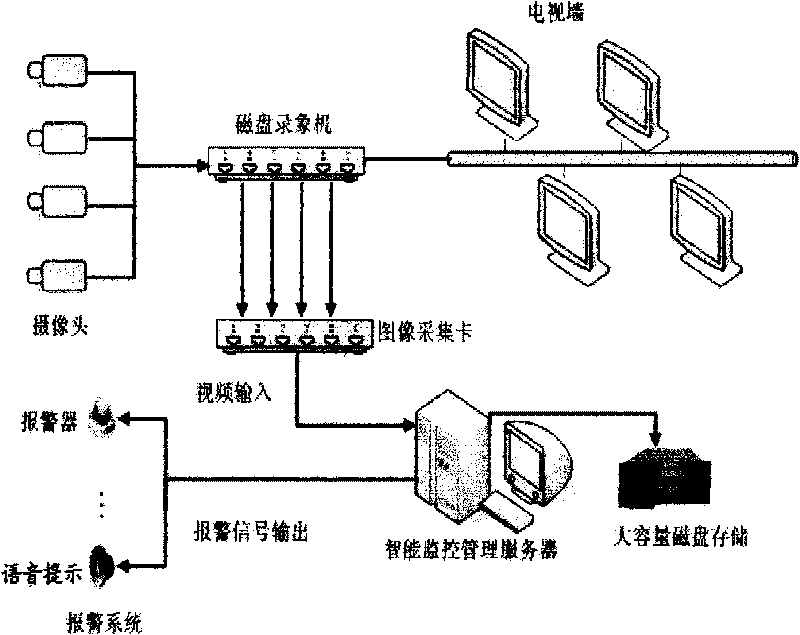
[0035] figure 1 Shown is a schematic diagram of the intelligent video surveillance system architecture. The intelligent video monitoring system includes three parts: video acquisition unit, intelligent event analysis and processing unit, and alarm unit. The video acquisition unit includes several cameras, which input video to the intelligent monitoring management server through the image acquisition card. The intelligent monitoring management server analyzes and processes the multi-channel video at the same time. After detecting the alarm event, it generates alarm information and outputs it to the alarm system for voice alarm. At the same time, information such as alarm information and evidence pictures are saved to the disk.
Embodiment 2
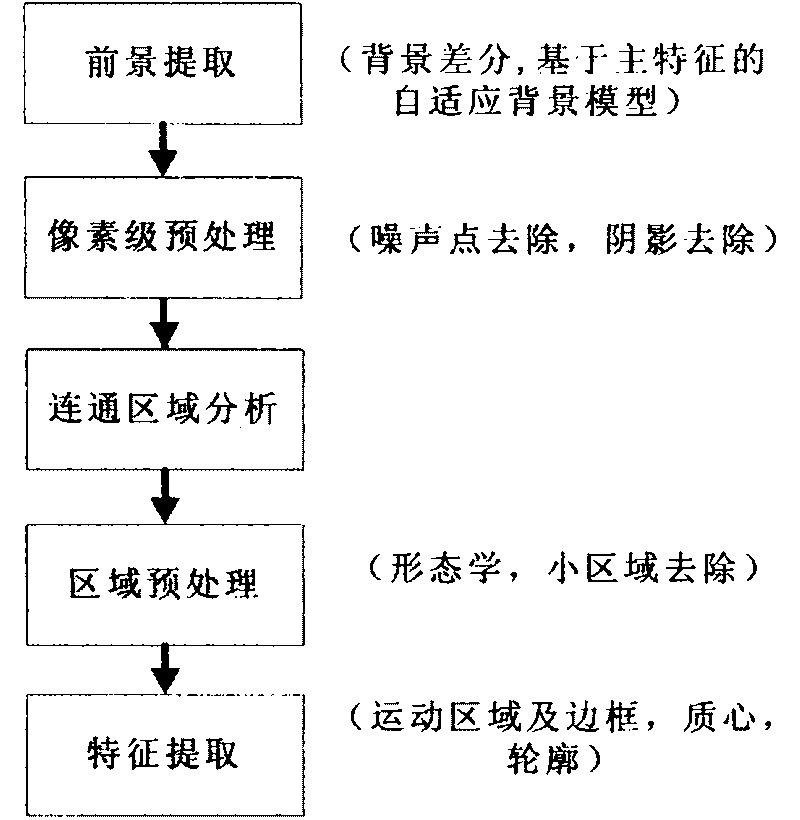
[0037] figure 2 It is a flow chart of the processing of moving object detection. The processing steps are as follows: 1) Foreground extraction. Foreground extraction adopts background difference method, and background modeling adopts adaptive background model based on main features. 2) Pixel-level preprocessing. The area detected by the foreground contains a lot of noise points, so the pixels need to be further processed, mainly including noise point removal and shadow removal. 3) Connected region analysis, which mainly solves the fusion and segmentation of foreground regions. 4) Regional preprocessing. Use morphology to remove holes and noise, and remove small foreground objects, because small foreground objects may be noise points caused by environmental influences. Finally, mark the moving target. 5) Feature extraction. Feature extraction is mainly to extract the position, size, centroid, contour, and color histogram of each moving target to provide feature informat...
Embodiment 3
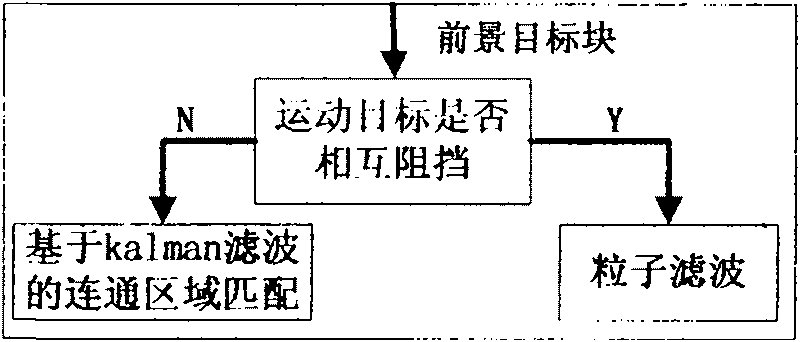
[0061] image 3 Process flow chart for moving target tracking. The tracking algorithm first uses a Kalman filter to predict whether an obstruction will occur. In the case of no obstruction between targets, the connected component tracking method based on Kalman filter is adopted; in the case of obstruction between targets, the particle filter tracking method is adopted. Kalman filtering can only solve nonlinear and non-Gaussian systems. In the case of non-blocking, the time interval between two adjacent frames of images is short enough that it can be assumed that the target is moving at a uniform speed per unit time, so Kalman filtering can be used to achieve tracking. In the case of blocking, the posterior probability distribution of the tracking process is often nonlinear and non-Gaussian, which is suitable for particle filtering.
[0062] The condition for judging the occurrence of blocking is: whether there is a foreground connected area in the kth frame intersecting wit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com