Method and device for supervising traffic based on token bucket
A token bucket and traffic technology, applied in the field of data transmission, can solve problems such as inapplicability, achieve good compatibility, high processing rate, and break through the bottleneck of processing capacity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
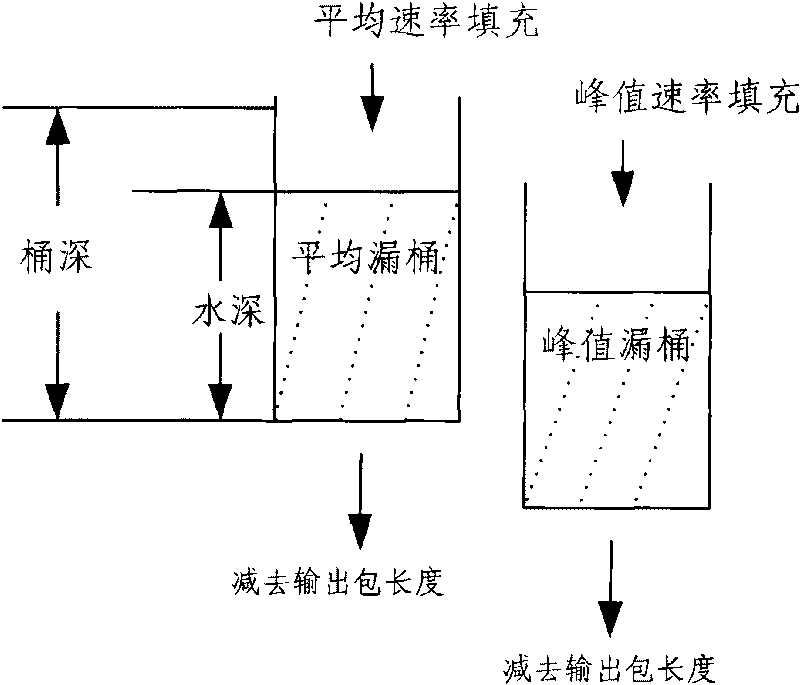
[0042] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
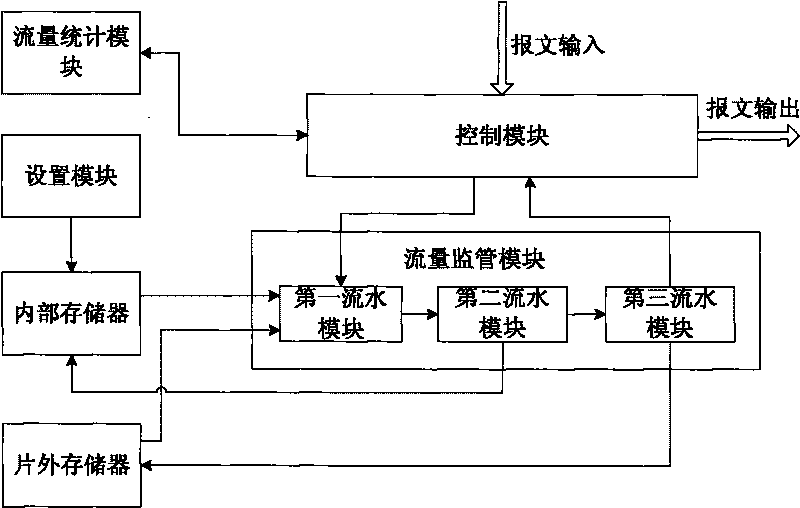
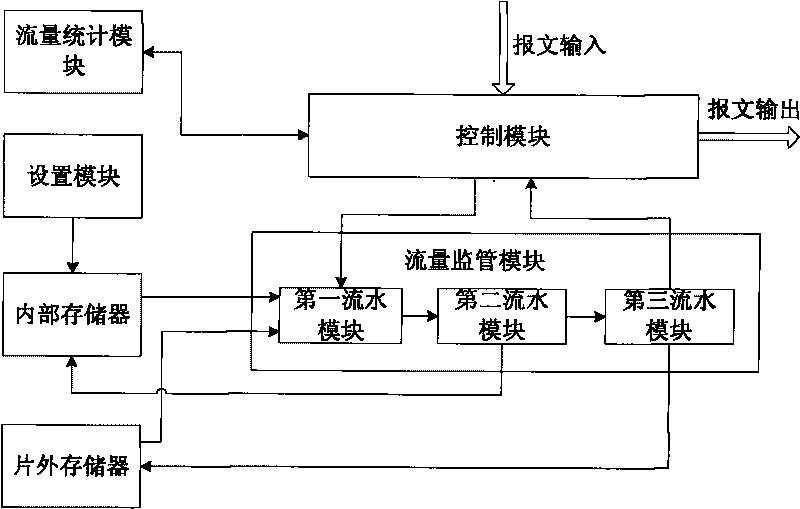
[0043] see figure 2 , which is a structural diagram of the traffic monitoring device proposed by the present invention, and the components of the device are:
[0044] The setting module is connected with the internal memory, and is used to pre-set various parameters of different leaky bucket algorithm rules, and simultaneously establishes a mapping relationship table between the flow ID and the leaky bucket algorithm rules, and lists the different leaky bucket algorithm rules and the mapping relationship The table is stored in internal memory;
[0045] The control module is connected to the traffic statistics module and the traffic supervision module respectively, and is used to obtain the packets to be supervised and send them to the traffic supervision module for processing; it is also used to receive the packets sent by the traffic supervis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com