Method for detecting network attack behaviors
A network attack and behavior technology, applied in the theoretical fields of network information security and mathematical statistics, can solve the problems of difficult to find system information, large amount of data, weak reliability, etc. The effect of low detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] Below in conjunction with accompanying drawing and example the present invention is described in further detail:
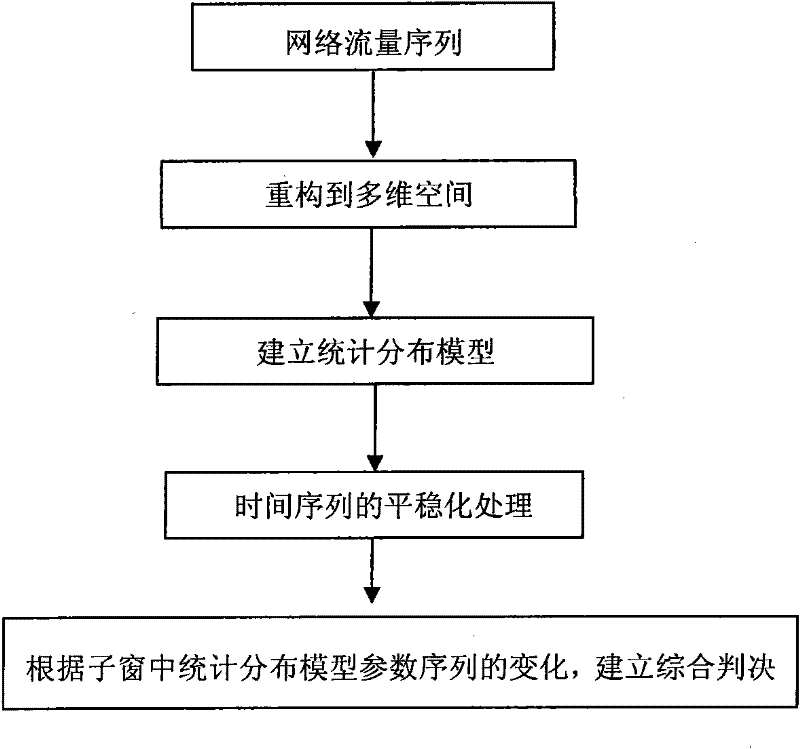
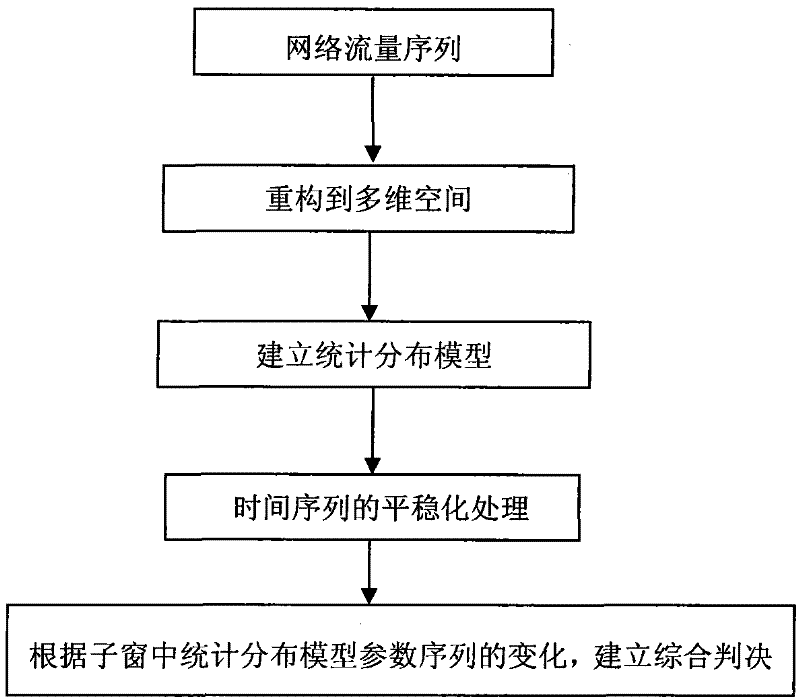
[0016] (1) Phase space reconstruction of network traffic time series, and establish a statistical distribution model based on normal network traffic time series.
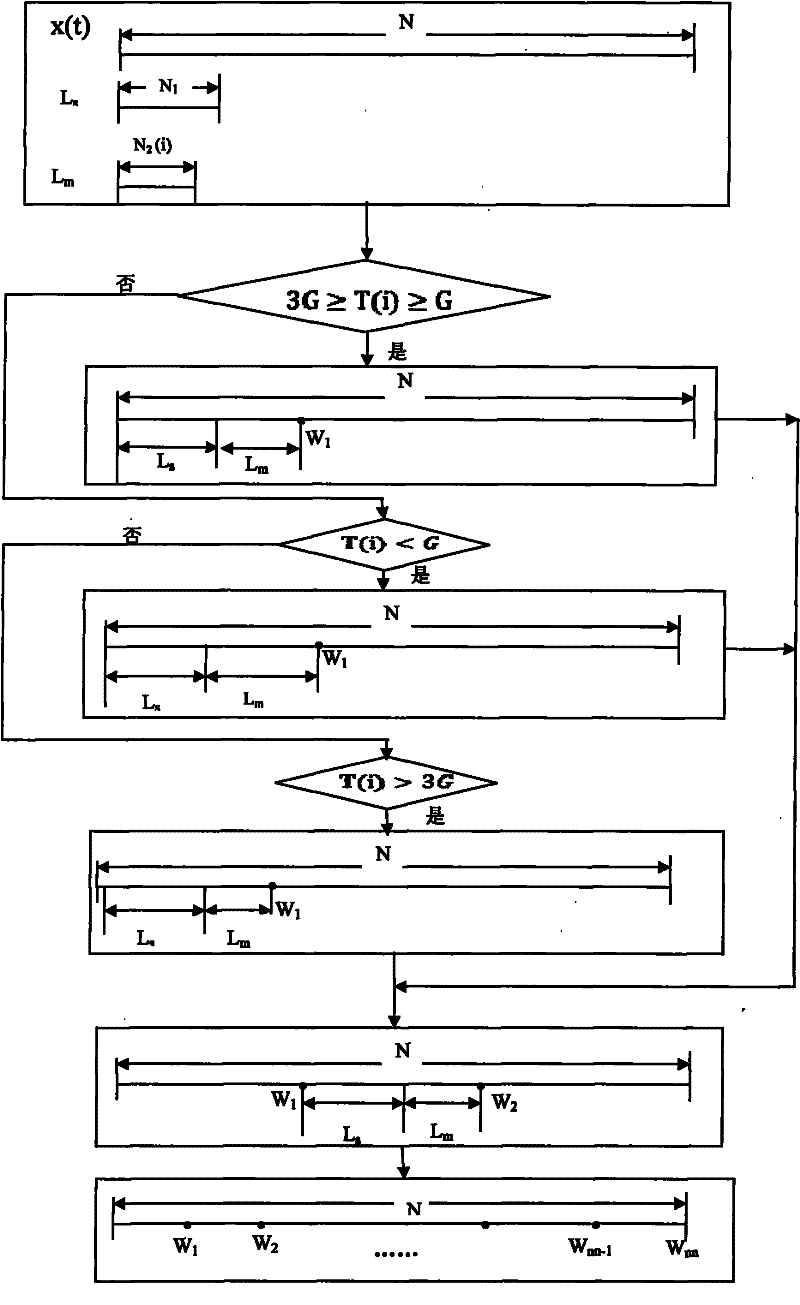
[0017] (1.1) According to the complex nonlinear characteristics of network traffic time series, the method of phase space reconstruction is selected, and the network traffic time series is reconstructed into multi-dimensional phase space. It has been proved that when the embedding dimension m and the time delay τ are determined, the reconstructed phase space can have the same geometric and information properties as the actual dynamical system, and have all the characteristics of the real space. Therefore, we use the method of phase space to study and analyze abnormal network traffic. After reconstruction, the phase space can maintain the invariance of the internal structure of the original networ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com