Method for evaluating trust of user action in trusted network
A user and network technology, applied in electrical components, transmission systems, etc., can solve problems such as research on trusted network trust requirements, and achieve the effects of improving time-sensitive characteristics, facilitating resources, and making independent trust decisions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
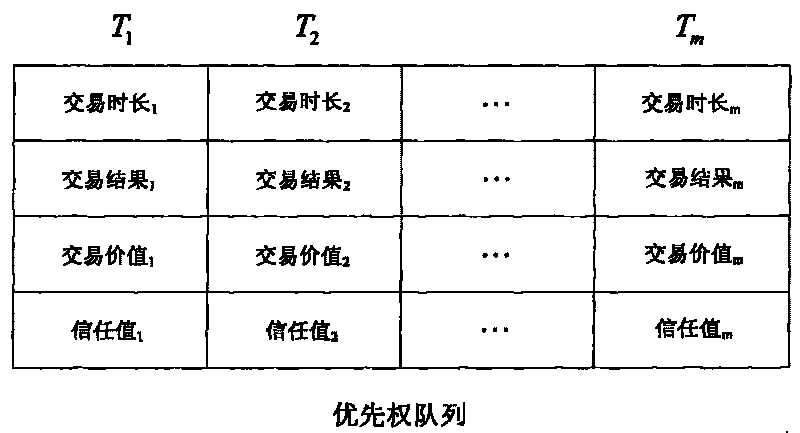
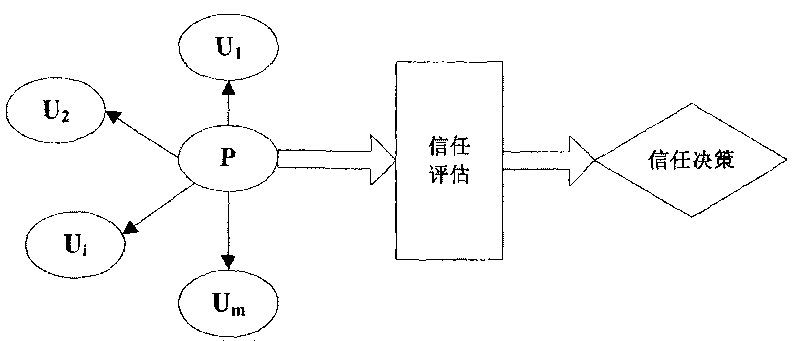
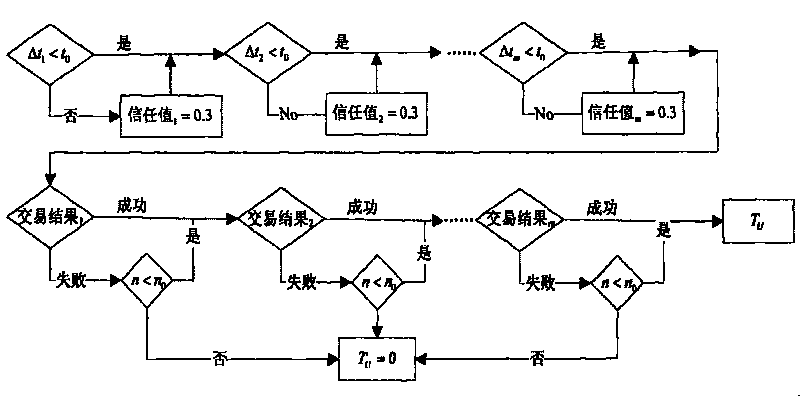
[0039] The implementation method of user behavior trust evaluation adopted in the present invention is: the user (User, referred to as U) and the resource provider (Provider, referred to as P) in the trusted network interact, and the user U sends a request to the resource provider P, requesting Use this resource. At this time, remember that there are m other users who have transaction history with the user U in the trusted network, and the set formed is S U , the resource provider P will be based on S U All users in the system make a trust decision based on the user's behavioral trust evaluation to decide whether to accept their request. In order to realize trust evaluation, the basic trust value in the initial state is defined as 0.3, indicating that the relationship between users and resources in a trusted network is a basic trust relationship; the untrusted value is defined as 0, indicating that the relationship between users and resources The relationship is a completely...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com