Method and device for detecting Trojan in non-executable file
A technology for executing files and detection methods, applied in computer security devices, instruments, electrical and digital data processing, etc., can solve the problems of illegal function call difficulty, inability to fundamentally distinguish between normal program behavior and suspicious program behavior, etc., to ensure reliable sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
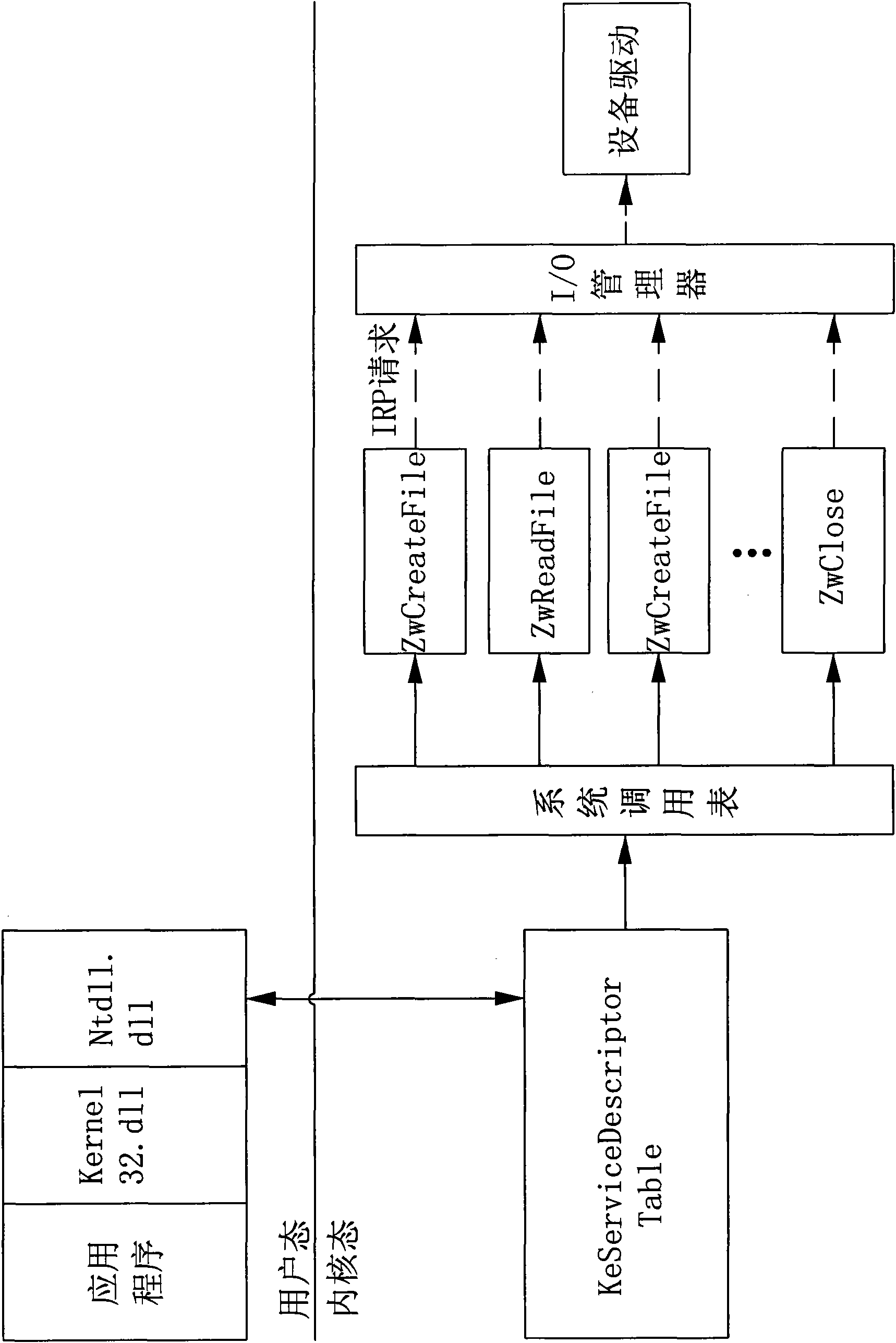
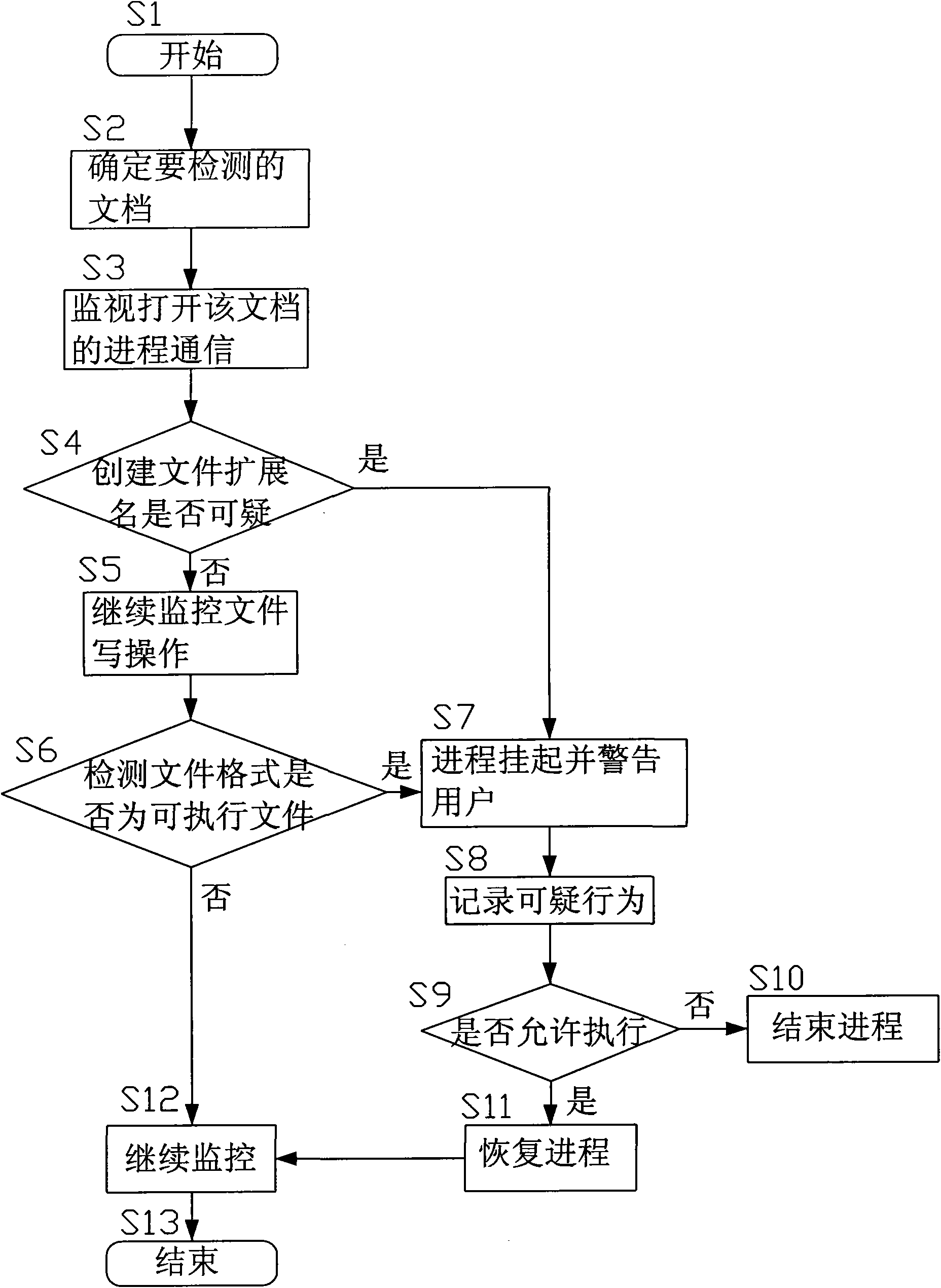
[0029] Referring to the accompanying drawings, a non-executable file hanging horse detection method of the present invention comprises the following steps:
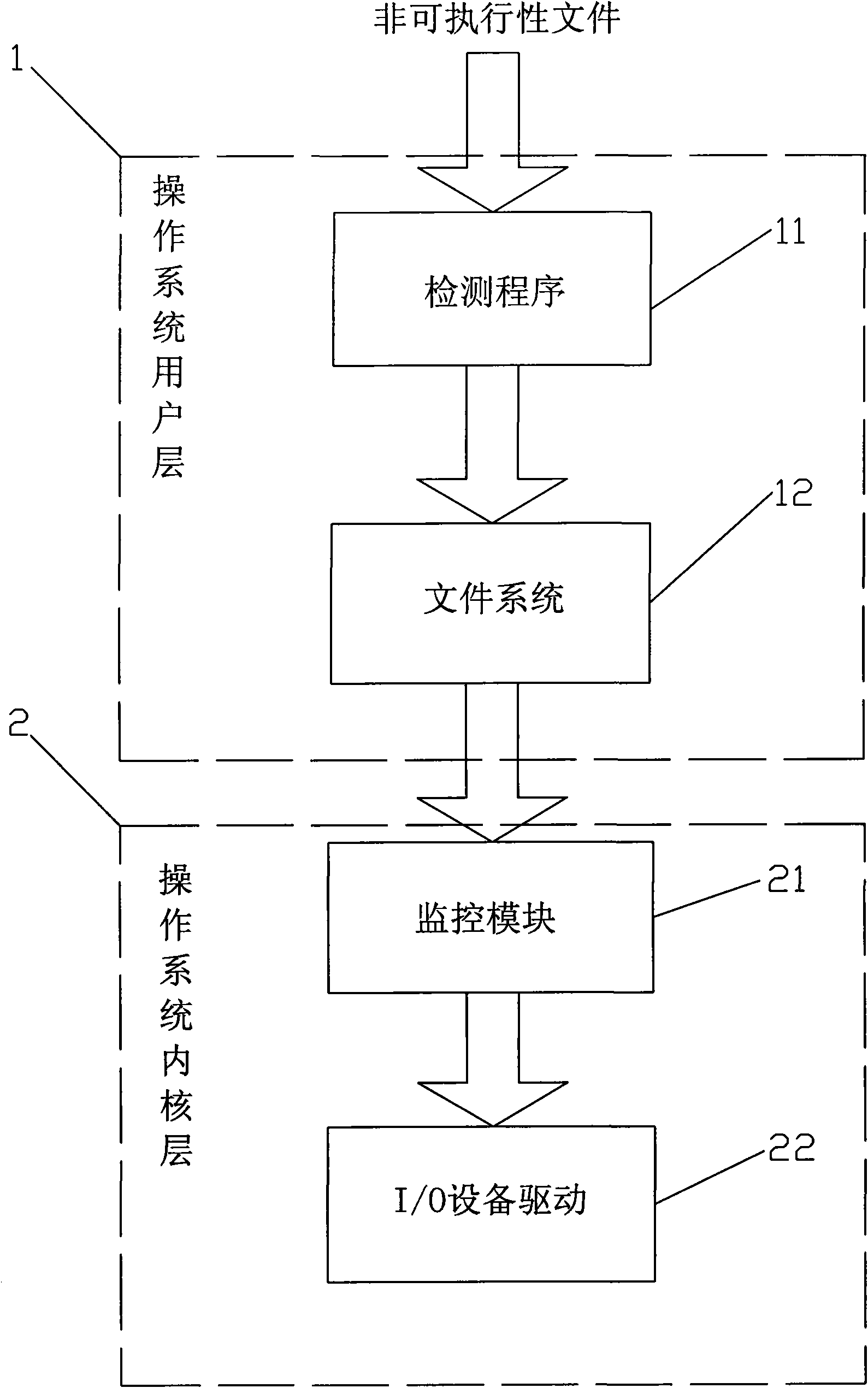
[0030] Determine the non-executable document to be detected by the detection program 11 arranged in the user layer 1 of the operating system, and open the process information of the non-executable document;
[0031] The process communication of opening the non-executable document is monitored by the monitoring module 21 arranged at the operating system kernel layer 2;
[0032] The monitoring module 21 of operating system kernel layer intercepts the creation file operation of monitoring process, judges whether the creation file extension of this non-executable document is suspicious, if then informs the detection program 11 of operating system user layer to suspend process, warn the user, record Suspicious behavior and prohibit execution, if not continue to monitor;
[0033] The monitoring module 21 of the kernel layer of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com