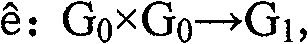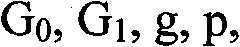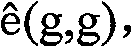Network multicast information encryption method against conspiracy attack
A technology of collusion attack and information encryption, which is applied in wireless communication, secure communication devices, broadcast service distribution, etc., can solve the problems of complex calculation and huge communication volume, and achieve reduction of calculation, calculation energy consumption and communication energy consumption Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] (1) Parameter establishment stage
[0017] Choose an elliptic curve group G 0 , to build a bilinear map ê: G 0 ×G 0 →G 1 , g is G 0 Generator on , p is G 0 any point. We secretly choose a q∈Z as the secret factor, and the key MK is g q . For each attribute i, there are three public keys PK i 、PK i’ and PK i” , where PK i Represents possession of attribute i, PK i’ Represents no attribute i, and PK i” Represents dispensable for attribute i. PK i =(PK i1 =g ti , PK i2 =ê(g,g) qti ), PK i’ =(PK i’1 =g ti ’, PK i’2 =ê(g,g) qti '), PK i” =(PK i”1 =g ti ", PK i”2 =ê(g,g) qti ")(t i is the hash function H(i)) on attribute i. The public key PK of the whole system is (G 0 , G 1 ,g,p,ê(g,g) q , PK i , PK i’ , PK i” ).
[0018] (2) Key extraction stage
[0019]For each node u, its public key PK u for g u , which is a public value. If encryption is required, it can be broadcast across the network for use by other nodes. The private key of no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com