Intrusion detection method based on improved OBS-NMF algorithm
An intrusion detection and algorithm technology, applied in computing, computer security devices, instruments, etc., can solve problems affecting detection results, difficult selection of thresholds, and low algorithm stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
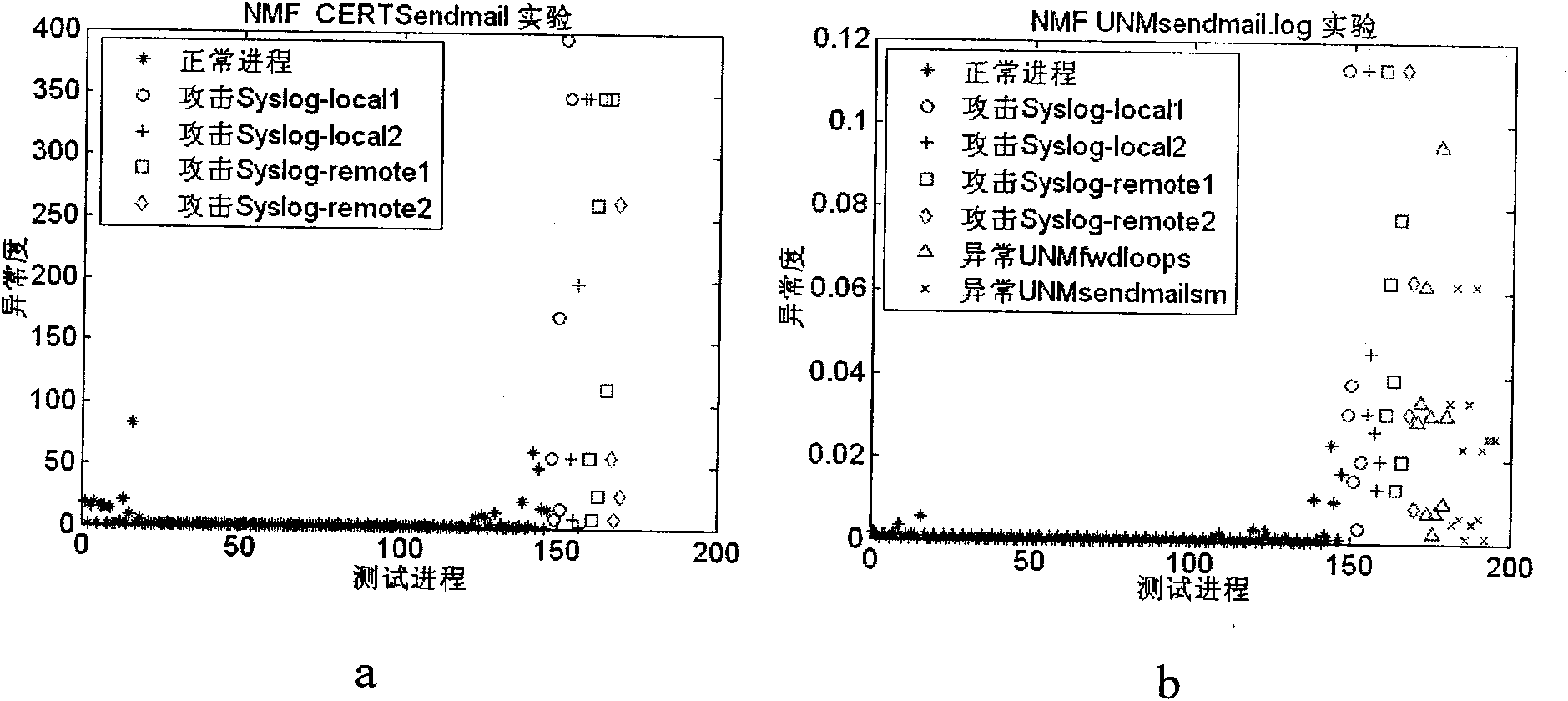
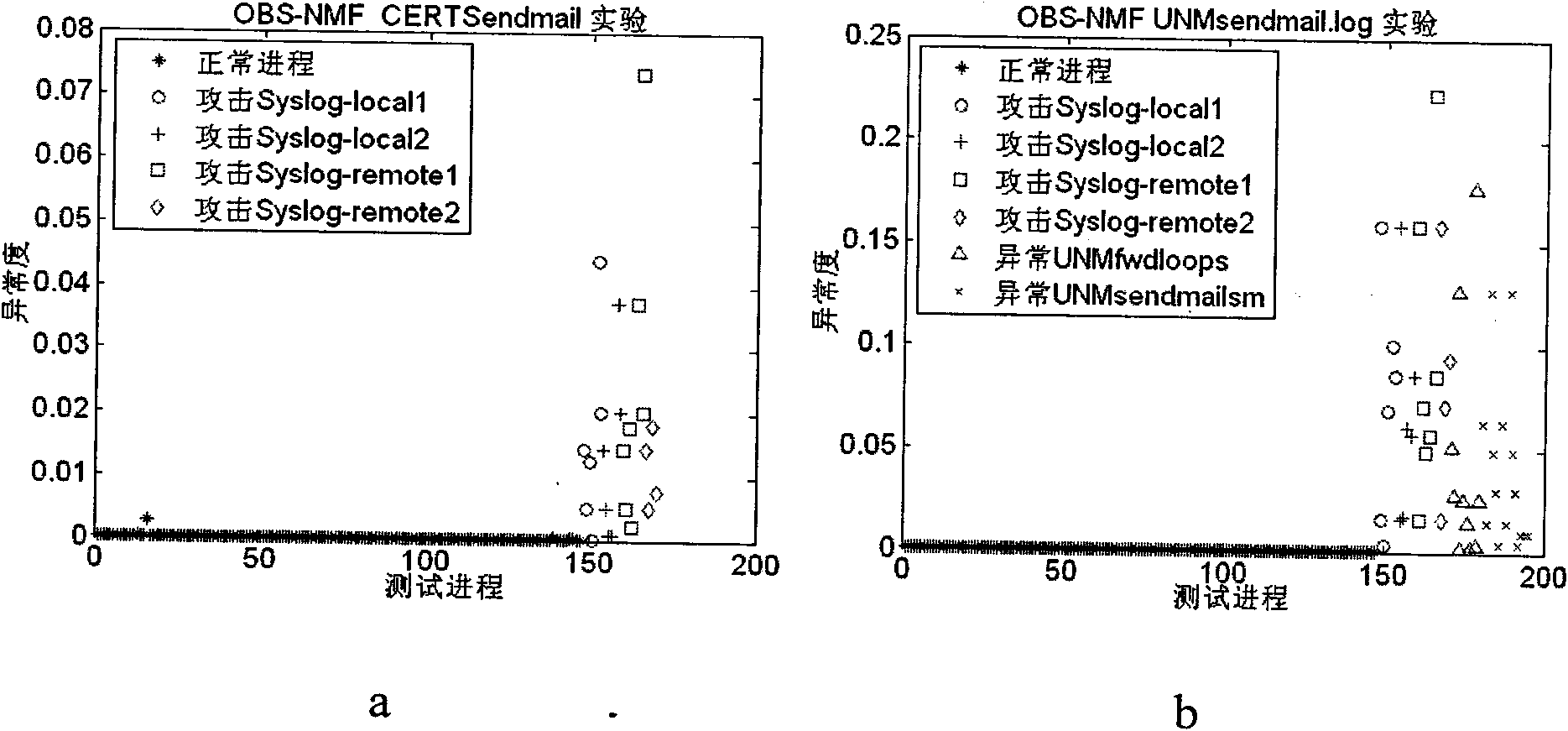
Image
Examples
Embodiment Construction
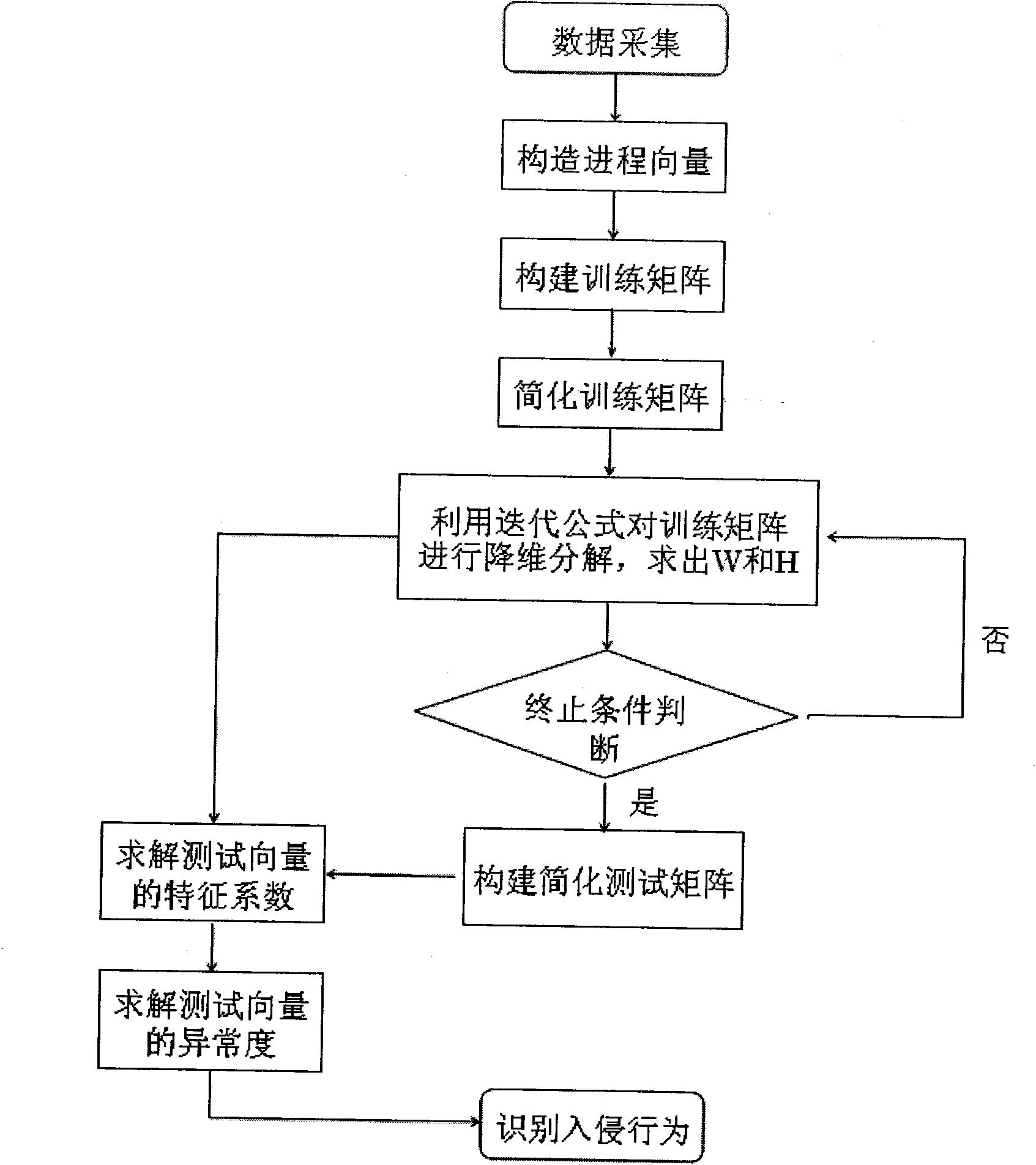
[0046] refer to figure 1 , refer to figure 1 Concrete implementation steps of the present invention are as follows;
[0047] Step 1, data collection.
[0048] When the client computer is running, when the system is running normally, a single program will generate multiple processes during the execution process. The process jumps to the kernel location called system_call through the interrupt command 0x80, enters the system call processing program, and calls related The kernel function returns to the user space after the execution is completed, and the system call sequence generated by the process is obtained by patching the kernel or intercepting the application program in the system, such as the Strace method.
[0049] Step 2, construct process vector.
[0050] For the collected raw data, first of all, it needs to be grouped, the system call data is grouped according to the process, and the system calls under the same process are grouped into one group; secondly, a process...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com