Safety chip, wireless control module and terminal
A wireless control module and security chip technology, applied in the field of communications, can solve problems such as inconvenience in business development, economic losses, inability to provide the best solution for users and applications, and achieve the effect of improving business security and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
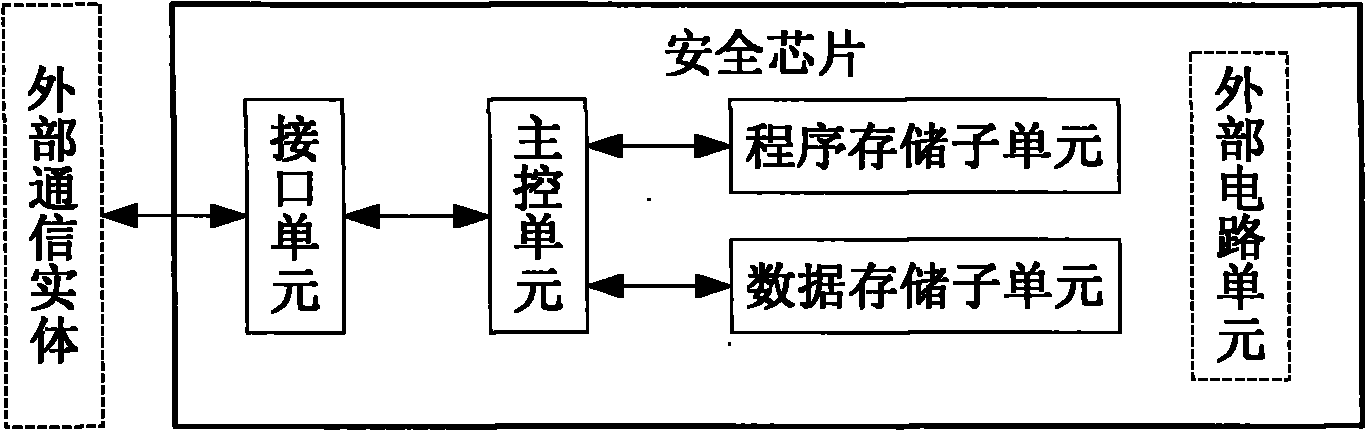
[0064] Embodiment 1. A security chip, such as figure 2 As shown, including: interface unit, main control unit, storage unit;
[0065] The storage unit is used to save the program and one or more keys; the program includes the following two or any one of them: one or more security algorithms, one or more protocols;
[0066] The interface unit is used to transmit data interacted between the main control unit and an external communication entity;
[0067] The main control unit is used to save the configured currently used program and key; receive a request from an external communication entity, and the request includes one or more of the following: encryption / decryption request, parsing request, authentication request; When the above request is an encryption / decryption request or an authentication request, find the currently used security algorithm and key from the storage unit, perform encryption / decryption or authentication on the data carried in the request, and obtain the e...
Embodiment 2
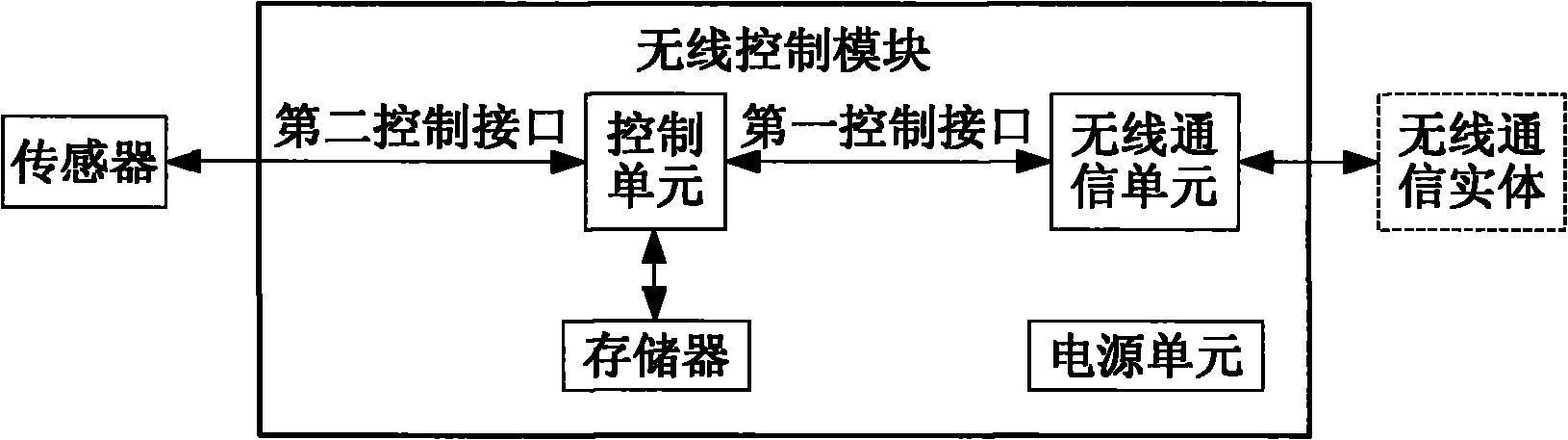
[0085] Embodiment 2. A wireless control module, including: the security chip in Embodiment 1;
[0086] a control unit, configured to configure currently used security algorithms, protocols, and keys in the main control unit of the security chip;
[0087] Other components can be the same as the prior art.
[0088] In this embodiment, the wireless control module may also include:
[0089] A wireless communication unit connected to an external wireless communication entity is connected to the control unit through a first control interface;
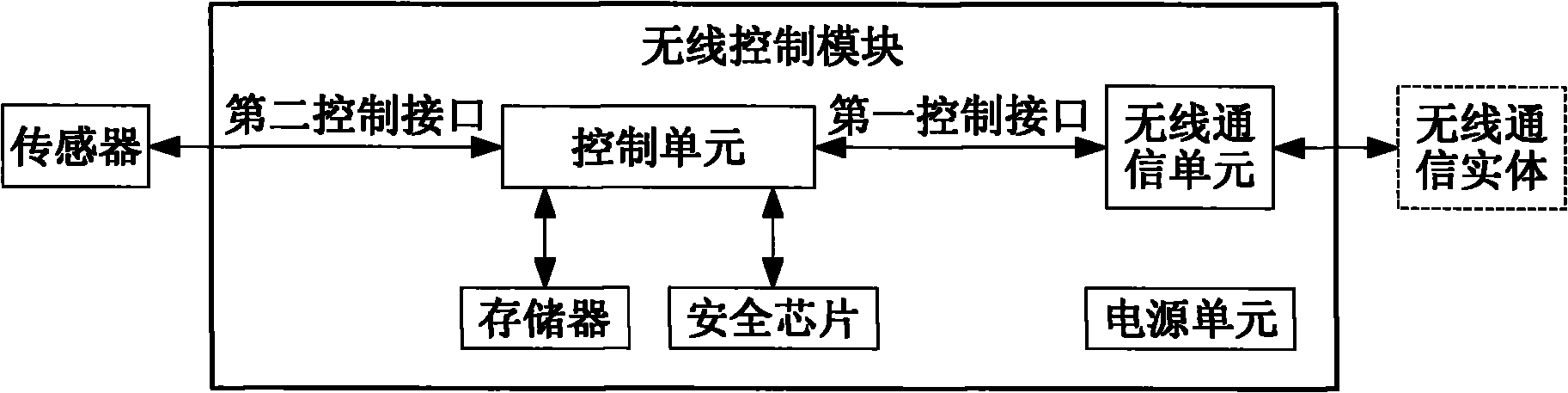
[0090] An implementation of this embodiment is as image 3 As shown, the security chip directly interacts with the control unit, and is connected to the wireless communication unit through the control unit, thereby interacting with an external wireless communication entity.
[0091] In this embodiment, the security chip is integrated on the main board of the wireless control module.
[0092] Another implementation of this embodiment is as...
Embodiment 3
[0101] Embodiment 3. A terminal, including: the security chip in Embodiment 1;
[0102] In this embodiment, the terminal may directly include the security chip in Embodiment 1, or may include the security chip by including the wireless control module 2 in Embodiment 2.
[0103] In this embodiment, if the terminal directly includes the security chip in Embodiment 1, it also includes a control unit for configuring the currently used security algorithm, protocol and key in the main control unit of the security chip .
[0104] The security chip can be directly integrated on the main board of the terminal, or can be integrated in other components of the terminal, or can be connected with other parts of the terminal by using a newly added connecting board.
[0105] In this embodiment, the security chip may be connected to the main board of the terminal or the connecting board by SMD welding and applying anti-tampering glue, but not limited thereto.
[0106] Obviously, those skille...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com