Wireless sensor network switching and pre-authenticating method based on evaluation
A wireless sensor and network switching technology, applied in wireless communication, network topology, electrical components, etc., can solve the problems of multiple forwarding, poor security, and high energy consumption, so as to avoid delay problems, speed up energy consumption, and reduce query times Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
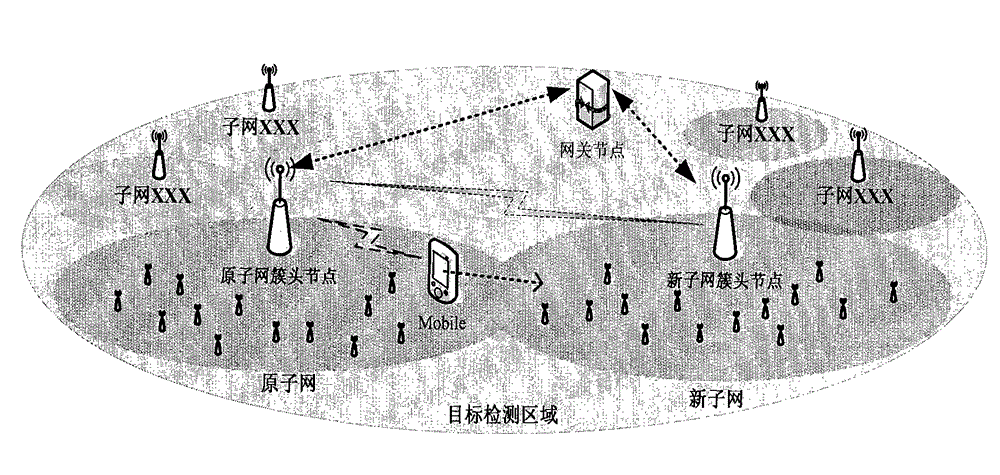
[0031] The network model adopted in the present invention is a wireless sensor network clustering model, which is mainly composed of mobile nodes, common sensor nodes, subnet cluster head nodes and gateway nodes, such as figure 1 As shown, the sensor nodes have limited energy and limited processing capacity, and are mainly used to collect information about the physical environment and send it to the subnet cluster head node; the subnet cluster head node has strong energy and processing capabilities, and is mainly used for subnet resource and security management , distribution, etc., the subnet cluster head nodes are connected in a self-organizing manner, and each subnet is integrated into a flexible and scalable wireless sensor network; the gateway node manages the entire sensor network as a whole; the mobile node in the subnet and the subnet Mobile between networks, dynamic query and collection of information.
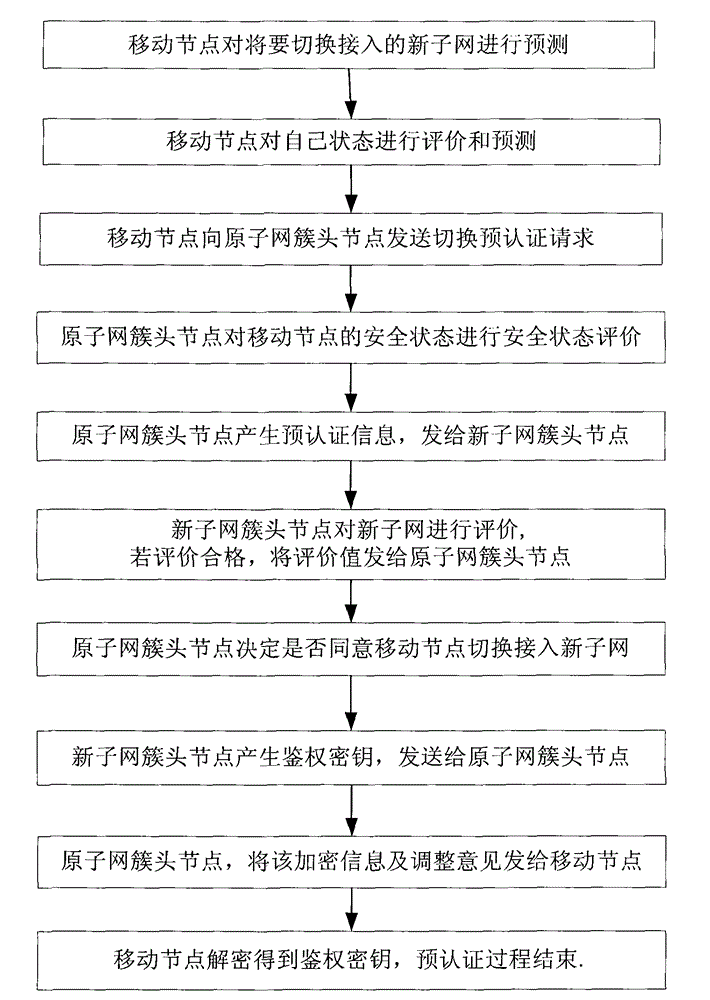
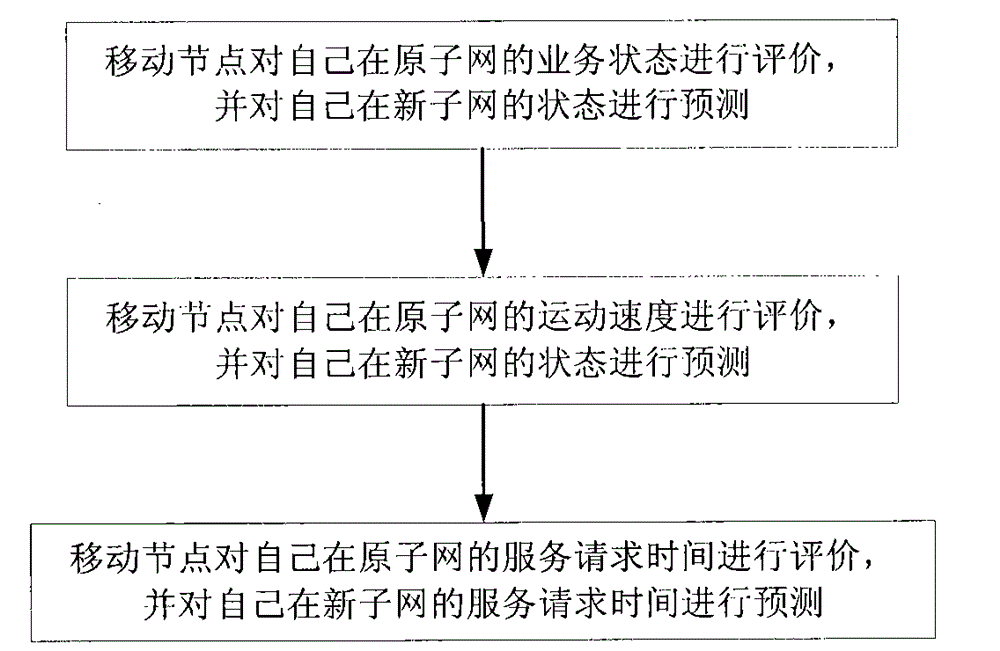
[0032] refer to figure 2 , the present invention considers mob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com