Fault detection technology of server operating system
An operating system and fault detection technology, applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., can solve the problems of lack of key files, malicious modification of configuration files, mistaken deletion, etc., to achieve the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
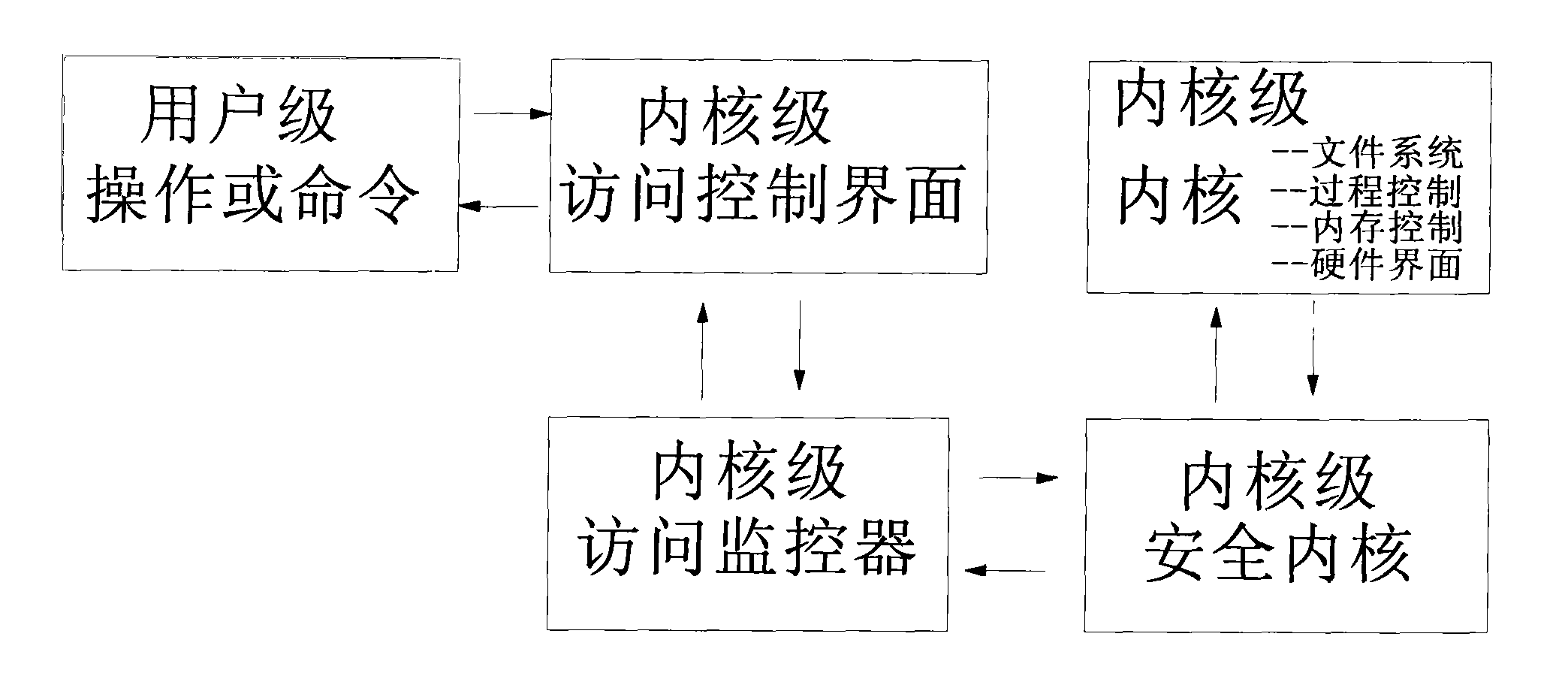
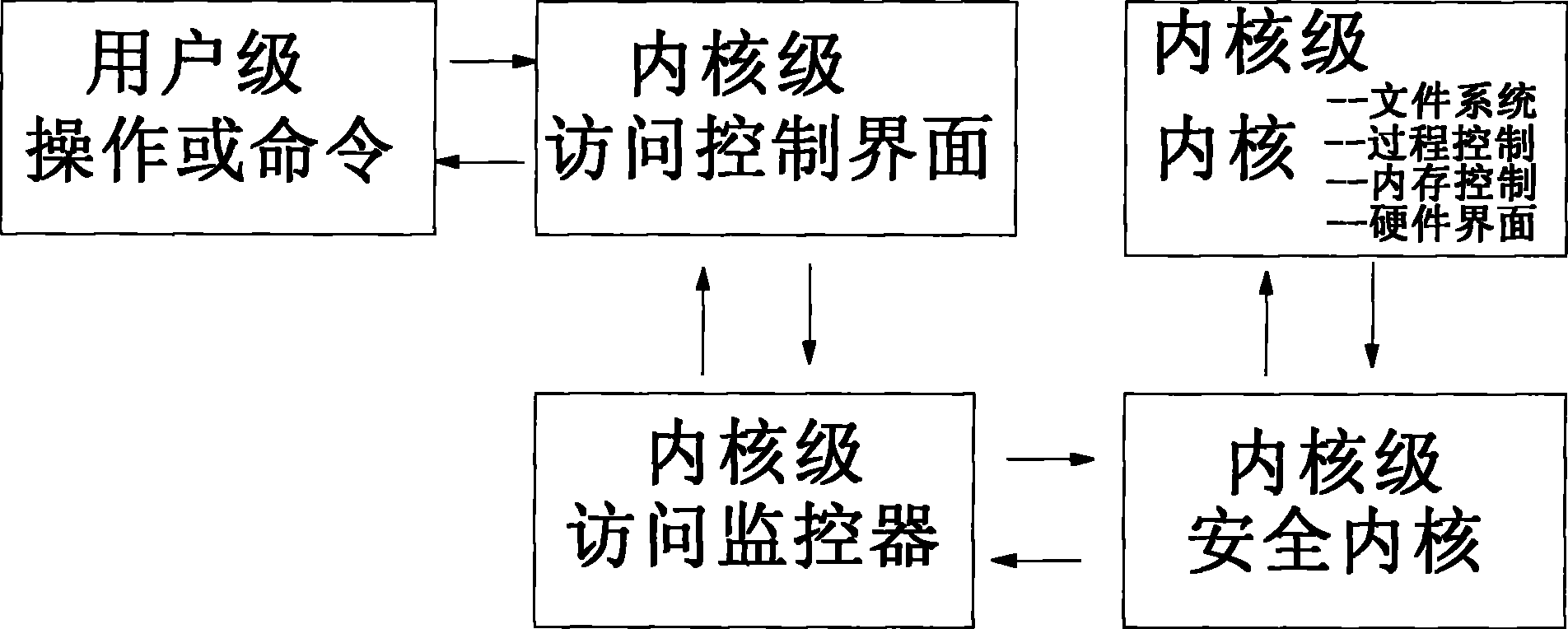
[0043] A secure kernel module is added to the driver layer (layer 0) to intercept and record all kernel access paths, so as to meet the technical requirements for handling server failures. The customer's business continuity does not even require the customer to restart the system. It supports all upper-layer applications and all lower-layer systems and machines, and can ensure the security of upper-layer applications at the granularity of the operating system.
[0044] It mainly consists of the following modules:
[0045] 1. File Mandatory Access Control Module
[0046] Allows users or processes to set access rules for files / directories with different access rights, and can set security levels for files / directories and users, and implement access control through security models by level. Any user (including system administrators) and unauthorized When a process creates, deletes, modifies, reads and other operations on sensitive files or directories, it will filter (allow or d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com