Method for pushing remote declaration based on behaviors in trusted network
A behavioral and credible technology, applied in electrical components, transmission systems, etc., can solve the problems of misjudgment of normal behavior, inaccurate and comprehensive behavior measurement, etc., to achieve the effect of complete safety mechanism, improved ease of use and scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with accompanying drawing of description:
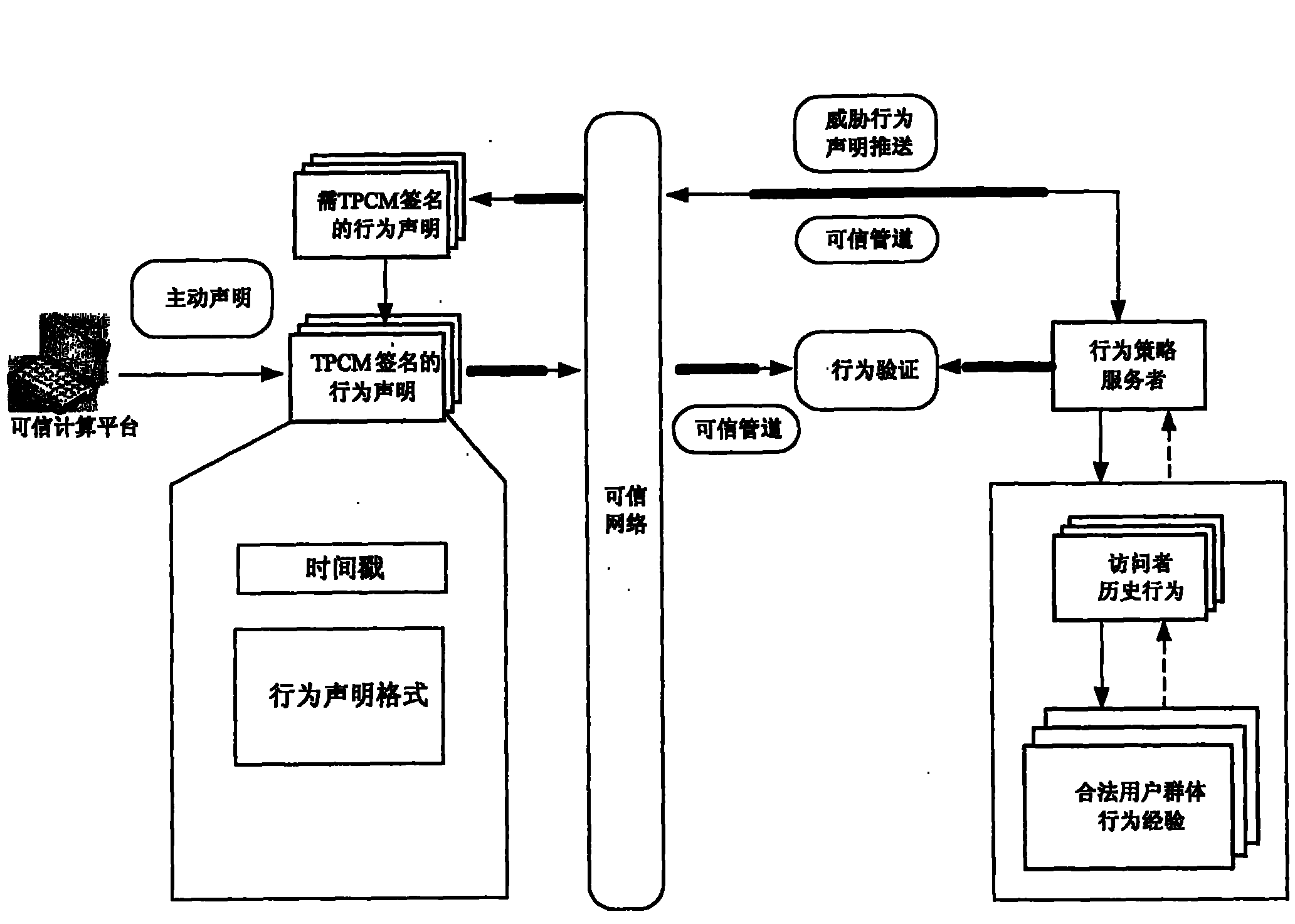
[0029] 1. Definition of trusted channel:
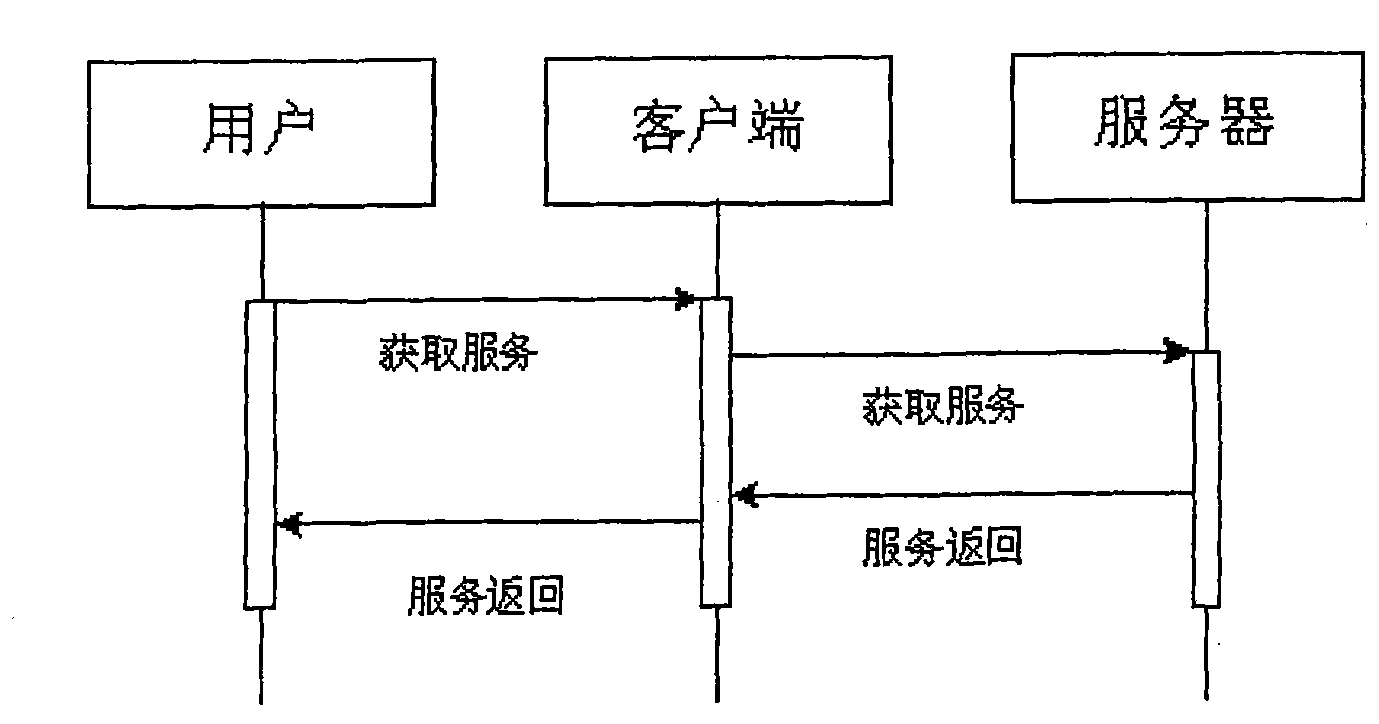
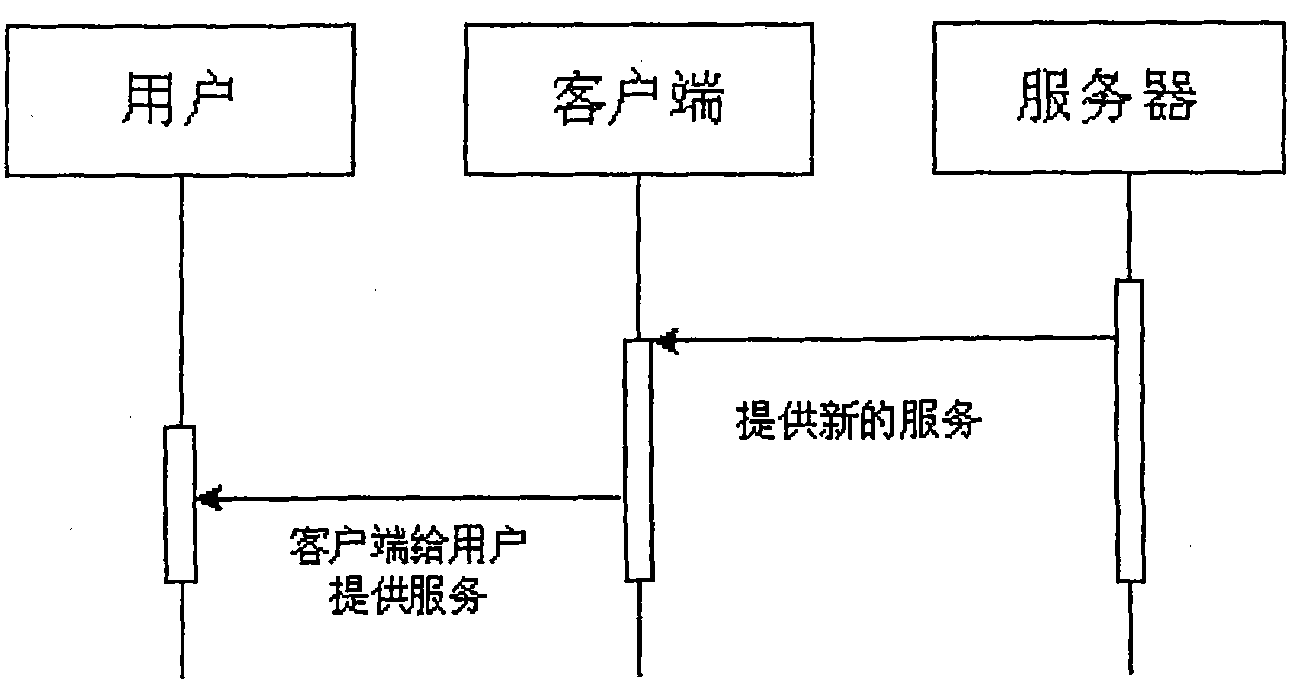
[0030] Based on the cryptographic function provided by the Trusted Platform Control Module (TPCM), the Trusted Pipeline realizes the trusted root of the system Trusted Computing Base (TCB), establishes an interaction channel between the user and the trusted root for users, and protects users Login information, protect sensitive information entered by users through the application, protect sensitive files of the user's master key, and protect the integrity and confidentiality of information protected by the pipeline through the cryptographic mechanism of the pipeline protocol. A trusted channel is a secure link established on demand. The establishment of a trusted channel can be actively requested by a network visitor or pushed by a network server.
[0031] 2. Trusted pipeline security goals:
[0032] A trusted chan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com