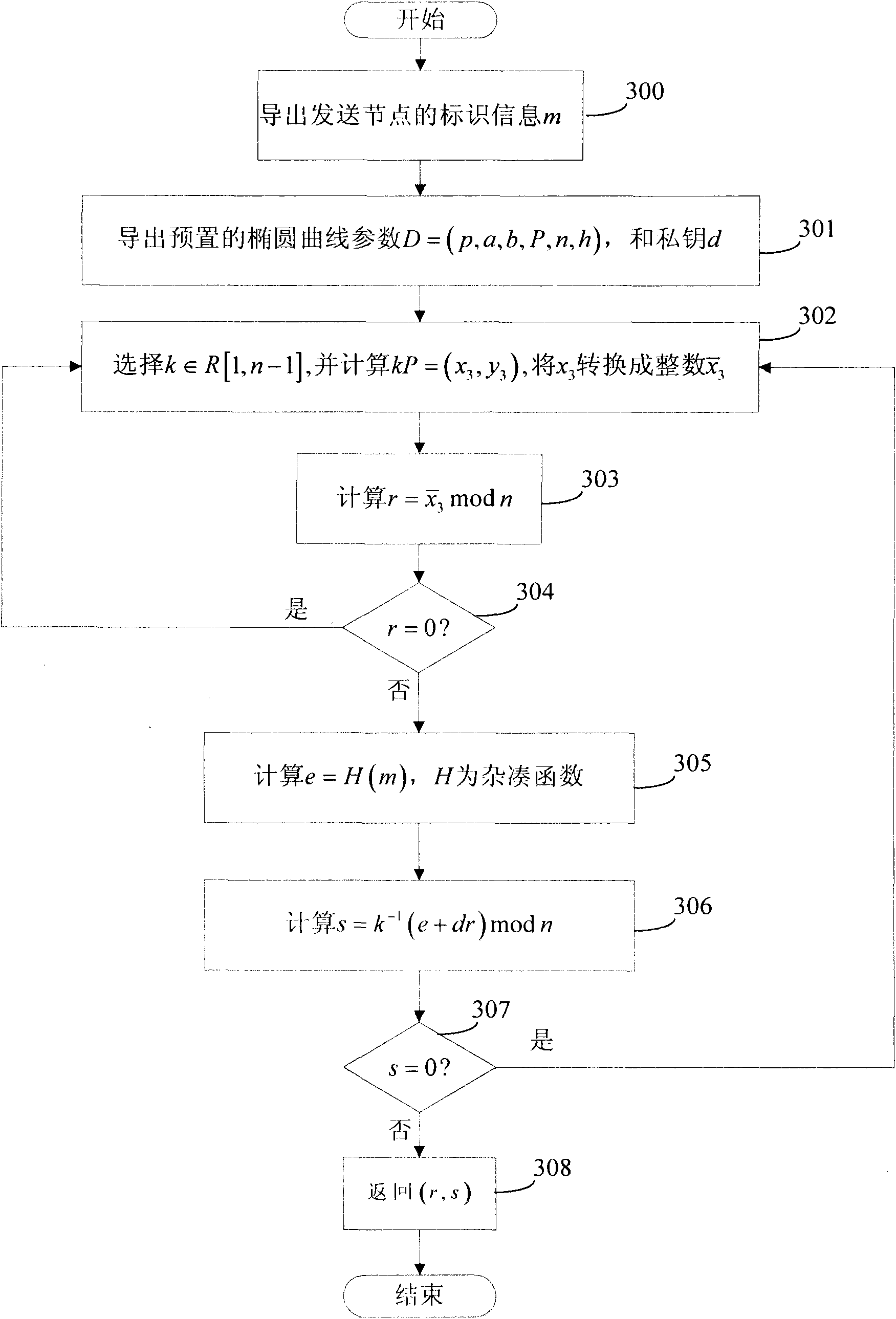Data encryption method, data decryption method and nodes
A data encryption and data decryption technology, which is applied in the field of elliptic curve cryptography, can solve problems such as large amount of calculation and large consumption of computing resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
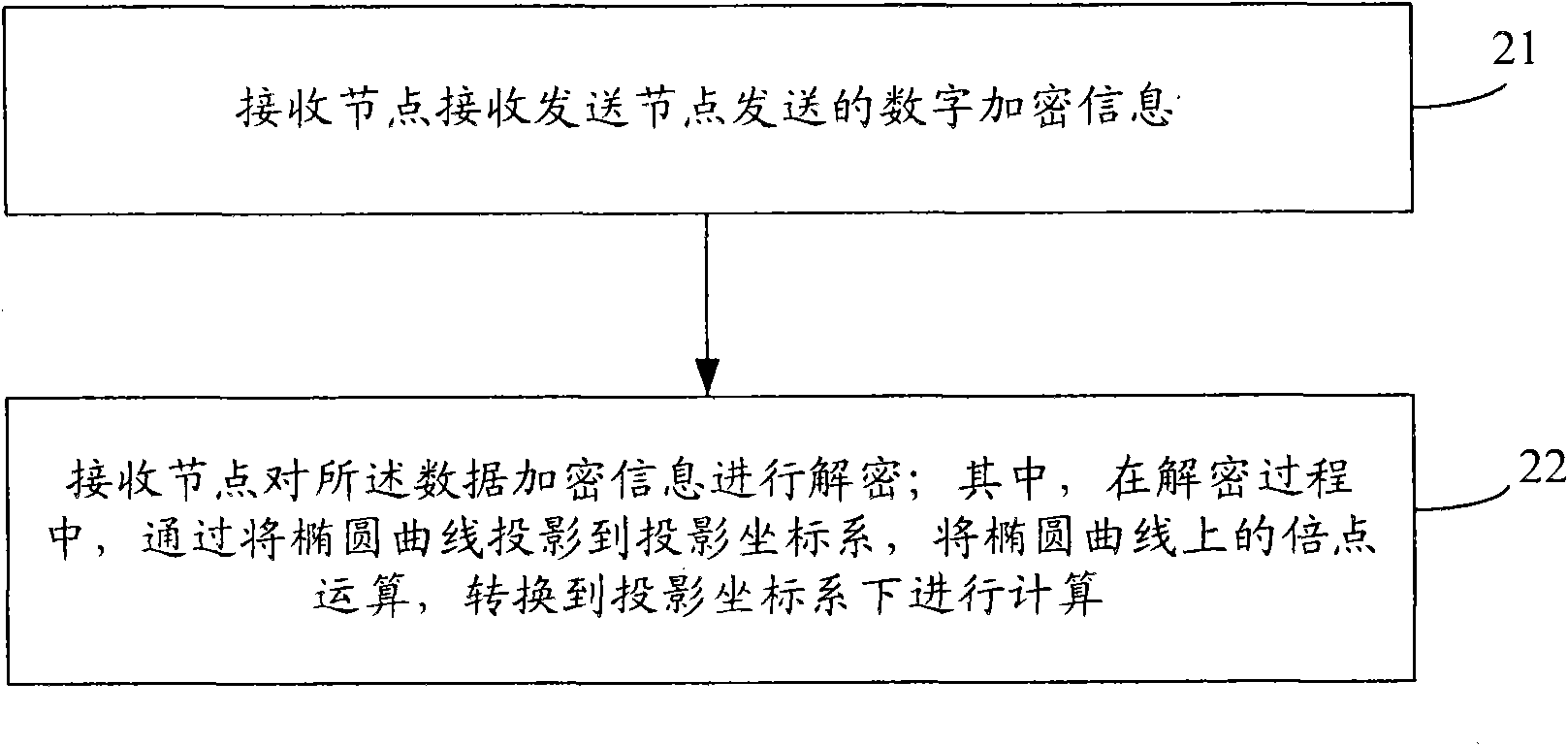
[0114] The present invention aims at the shortage of large amount of encryption and decryption calculations in the existing elliptic curve public key cryptosystem, by converting the coordinate system of the elliptic curve, the doubling operation of the elliptic curve is converted to the projected coordinate system, which reduces the signature authentication. The computational complexity of the algorithm expands the scope of application of the elliptic curve public key cryptosystem. The present invention will be further described through specific embodiments below in conjunction with the accompanying drawings.
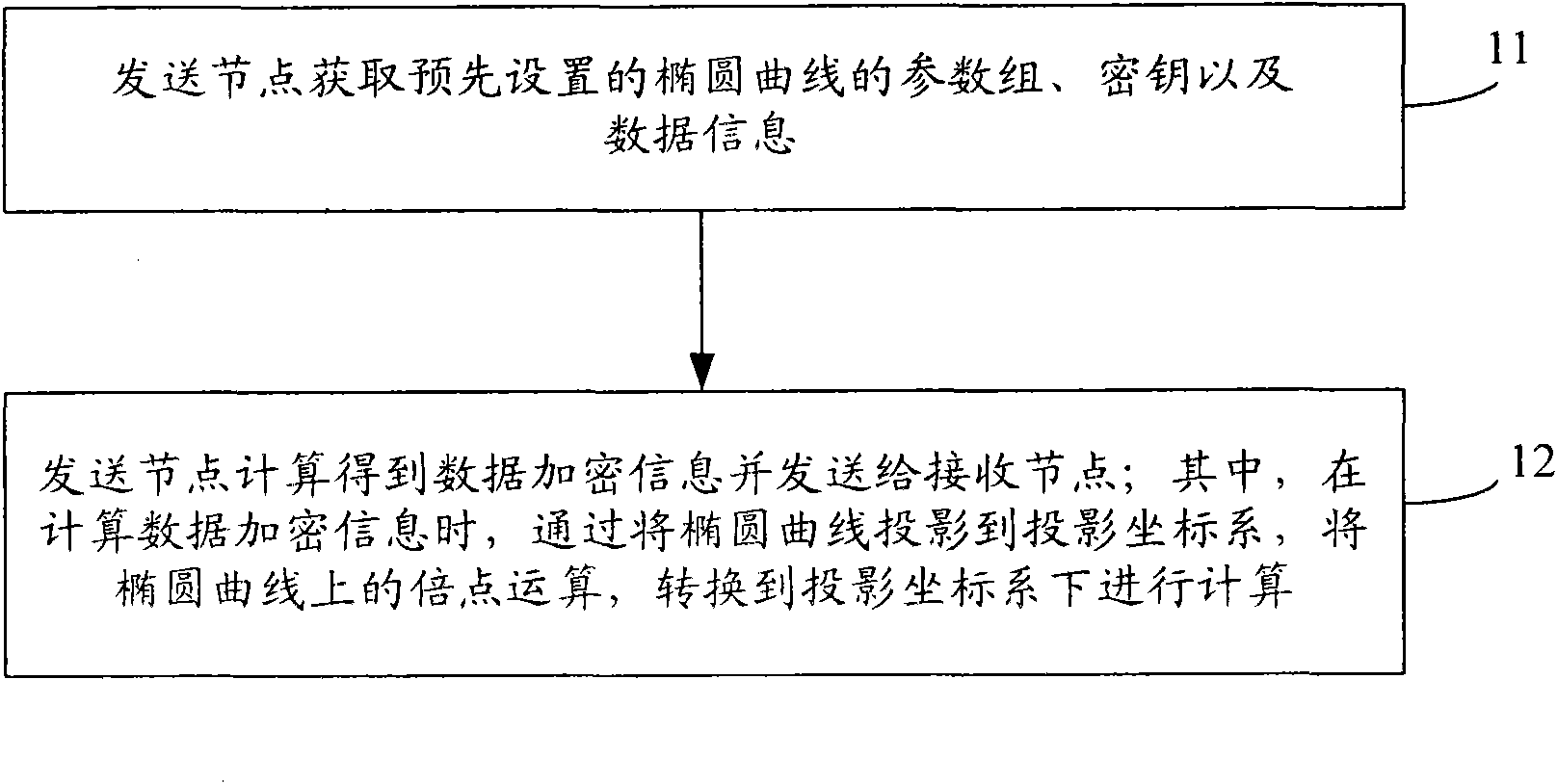
[0115] An embodiment of the present invention provides a data encryption method based on an elliptic curve public key cryptosystem. Please refer to figure 1 The data encryption method described in the embodiment of the present invention specifically includes the following steps:
[0116] In step 11, the sending node obtains a preset parameter group of the elliptic cur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com