RFID mobile phone and combination key technology-based authenticity identification method
A technology of combining keys and RFID tags, applied in the field of information security, can solve problems such as security risks, and achieve the effect of ensuring non-reuse, saving key update and management, and saving tedious work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
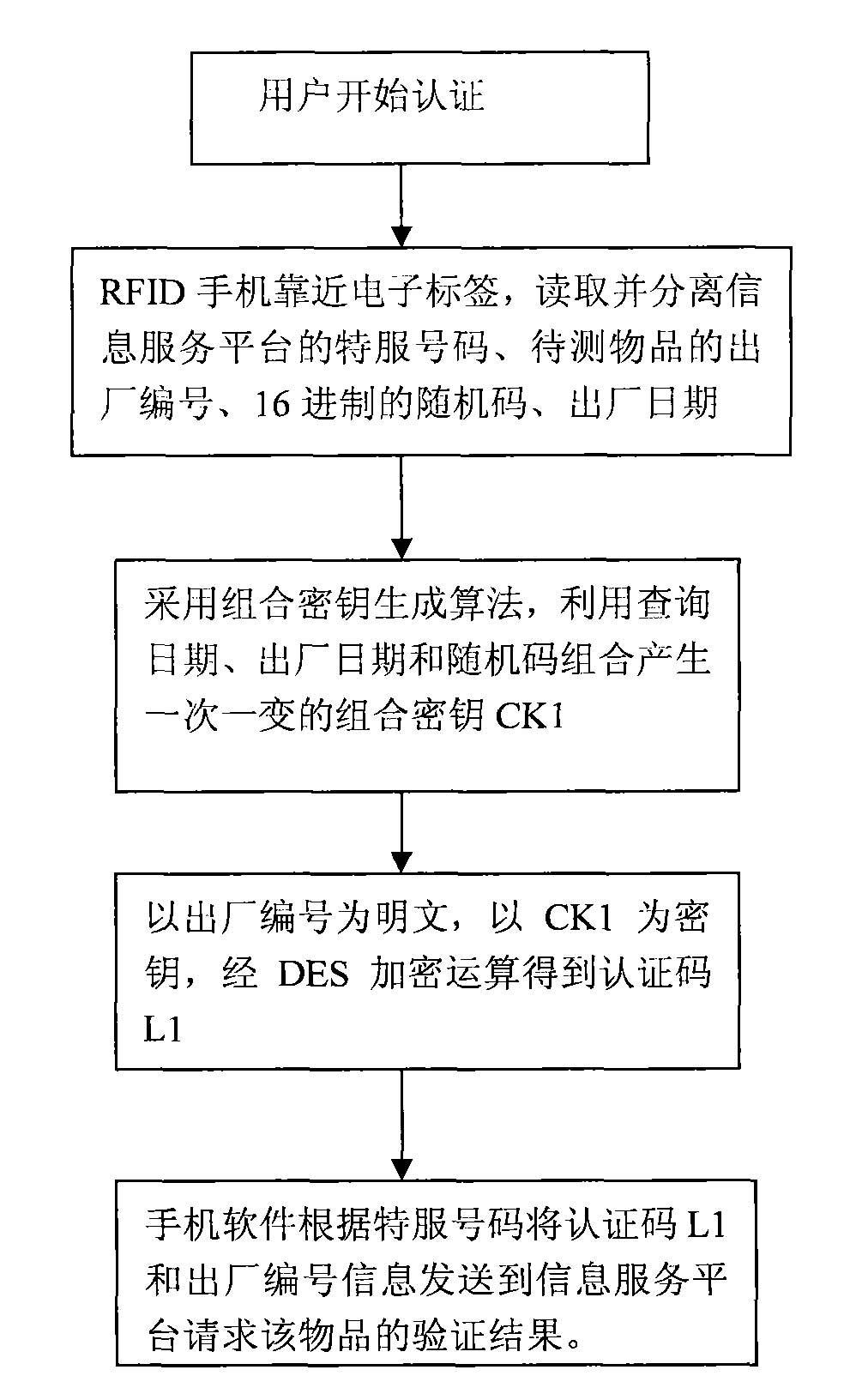
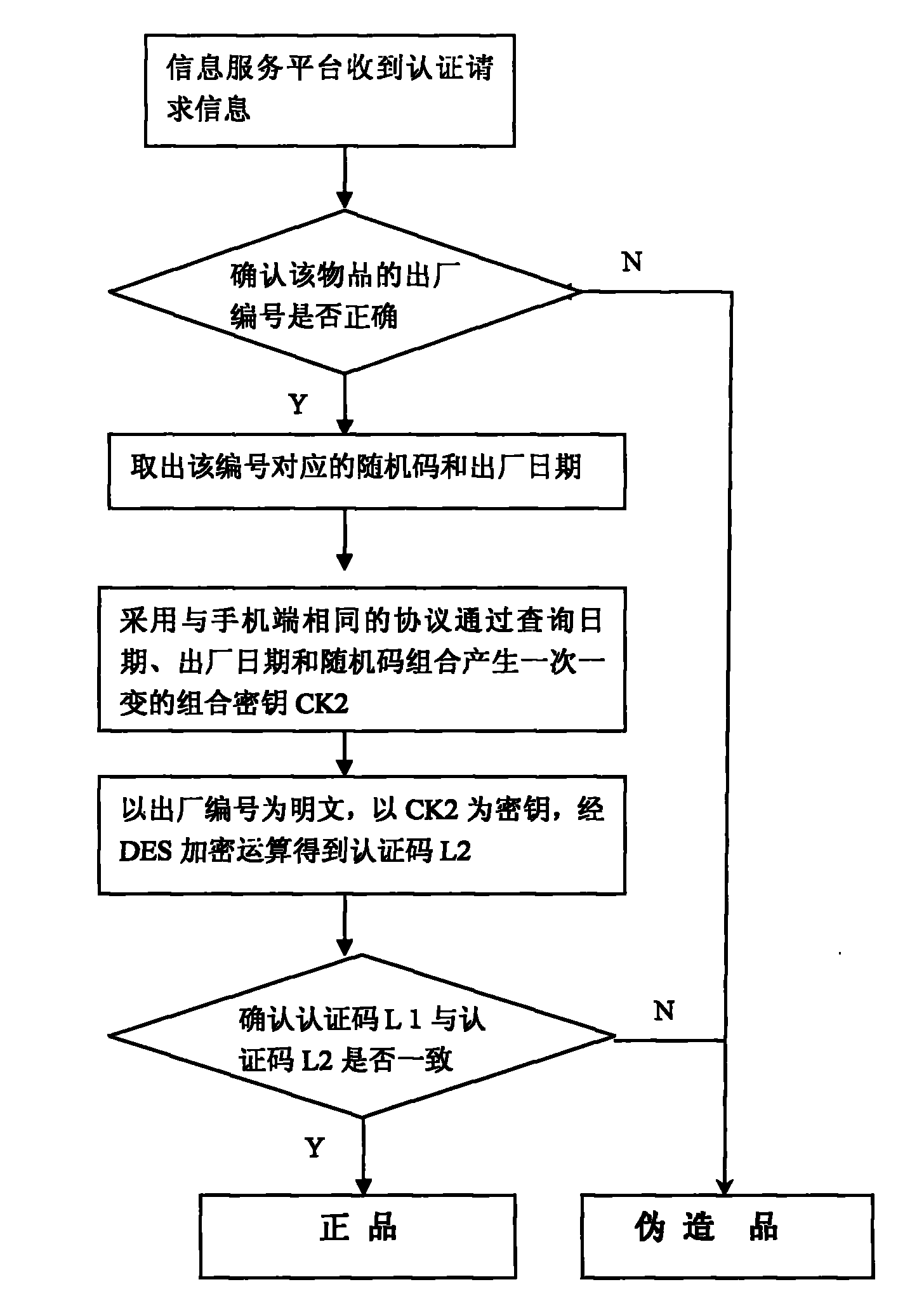
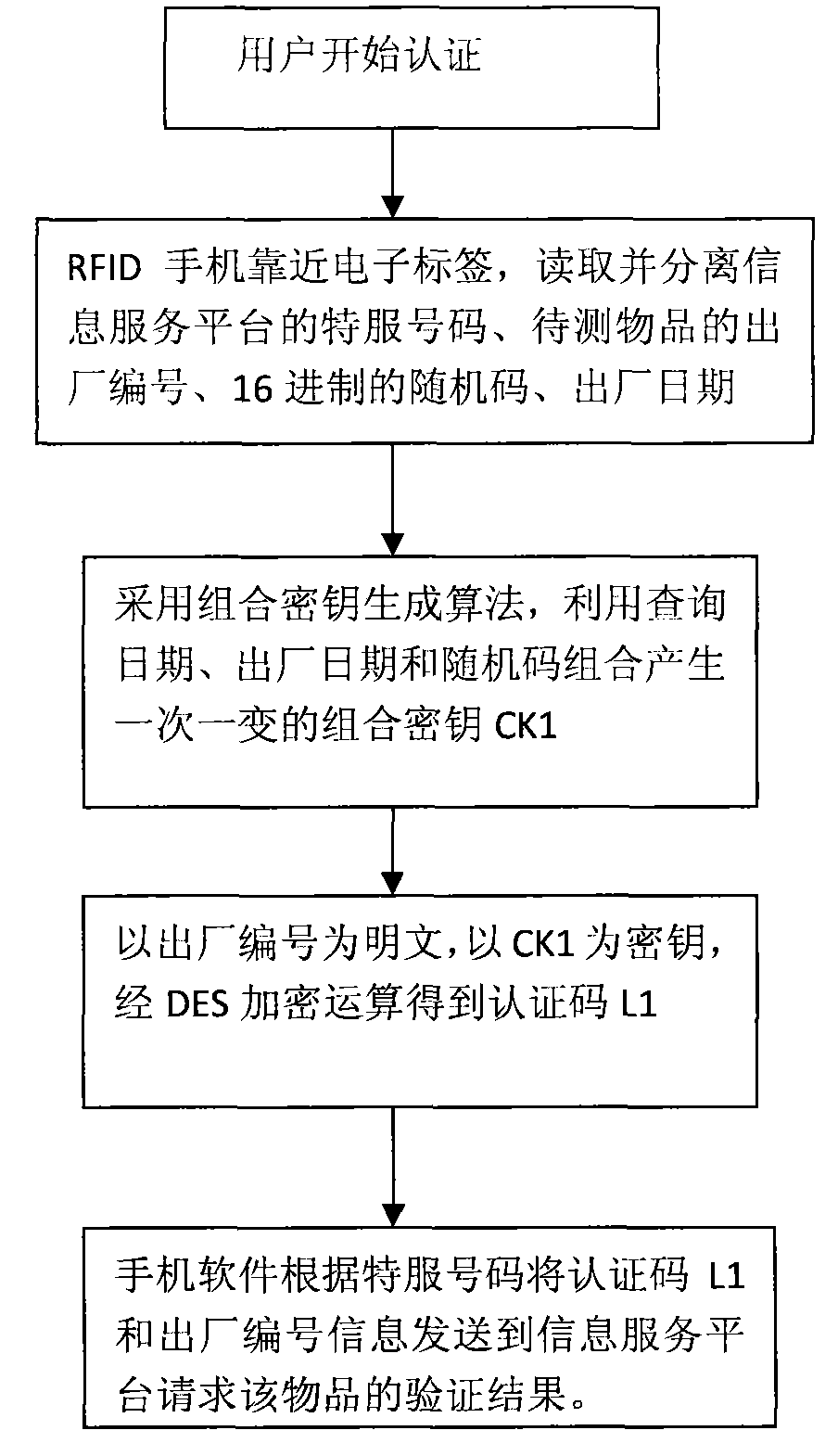
[0019] The following describes the implementation steps of the method for authenticating items based on RFID mobile phone and combined key technology with the accompanying drawings:
[0020] figure 1 : Explain that the user wants to distinguish the authenticity of the item, (1) Use an RFID mobile phone to approach the item and read the authentication information from the tag. The authentication information consists of the following: the special service number of the information service platform (8 bytes), the factory number of the item (8 bytes), the hexadecimal random code (16 bytes), and the date of manufacture (8 words) Section). (2) The mobile phone software extracts and separates each piece of data, and then uses a combined key generation algorithm to generate a combined key CK1 that changes once and after using the combination of the query date, the date of manufacture and the random code. (3) Use the factory serial number as the plaintext, use CK1 as the key, and obtain t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com