Method for realizing instruction buffer lock
An implementation method and instruction caching technology, which is applied in concurrent instruction execution, memory system, memory address/allocation/relocation, etc., can solve the problems of data cache locks not evaluating the cost-effectiveness, performance improvement, and large performance loss. Achieve the effect of reducing memory access delay, improving performance and energy saving, and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
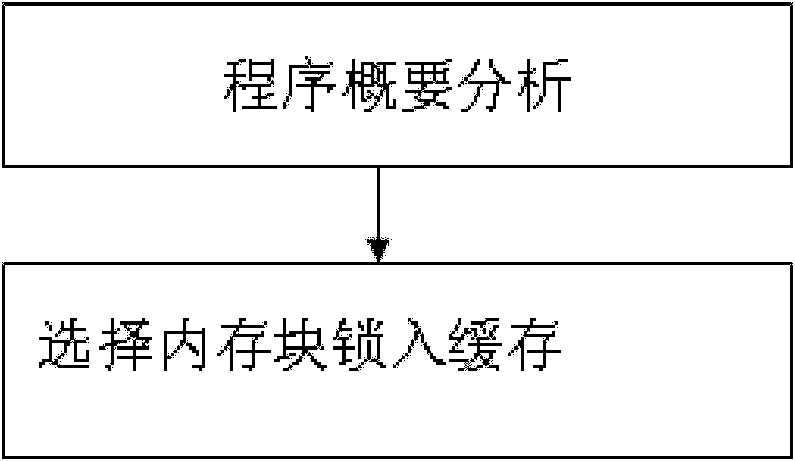
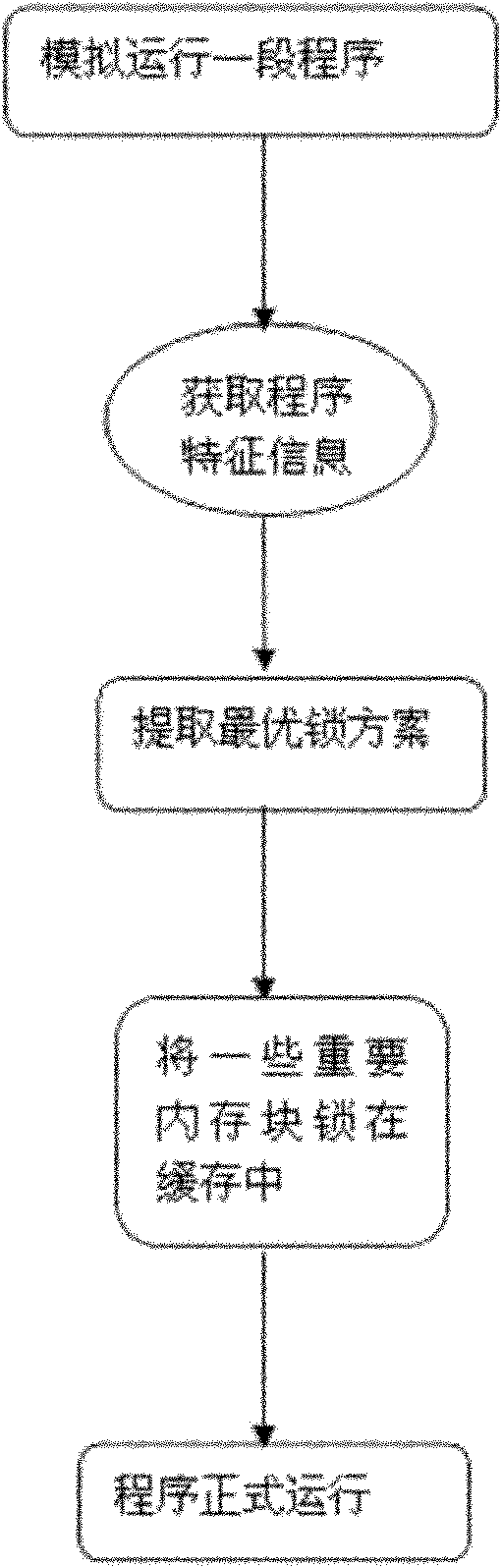
[0046] There is a program A. The memory block access sequence during the running of the program is (m0m1m2m3m4m5m6m7)10. This sequence is accessed 10 times. Each block is mapped to the same cache group, and the cache is 4-way associative. In the case of no lock, all of this access sequence will miss, that is, all 80 accesses will be lost. According to the instruction cache lock technology, if any 4 of these 8 memory blocks, such as m0, m1, m2, and m3, are locked In the instruction cache, the misses are reduced by half. This process is very simple. The most important thing is to store the program memory block access information and the lock status strategy of each block on the peripheral.
[0047] In this example, after the access of m0-m7, the access counter value of each block is 0, it is difficult to distinguish which block is better to lock, but the LRU count value is different, the value of m4m5m6m7 is relatively low, which is 3, respectively. 2, 1, 0, then you can consid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com