System and method for controlling service arrearages
A control method and business technology, applied in transmission systems, digital transmission systems, accounting/billing services, etc., can solve problems such as arrears control, and achieve the effects of protecting interests, simple system transformation, and strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
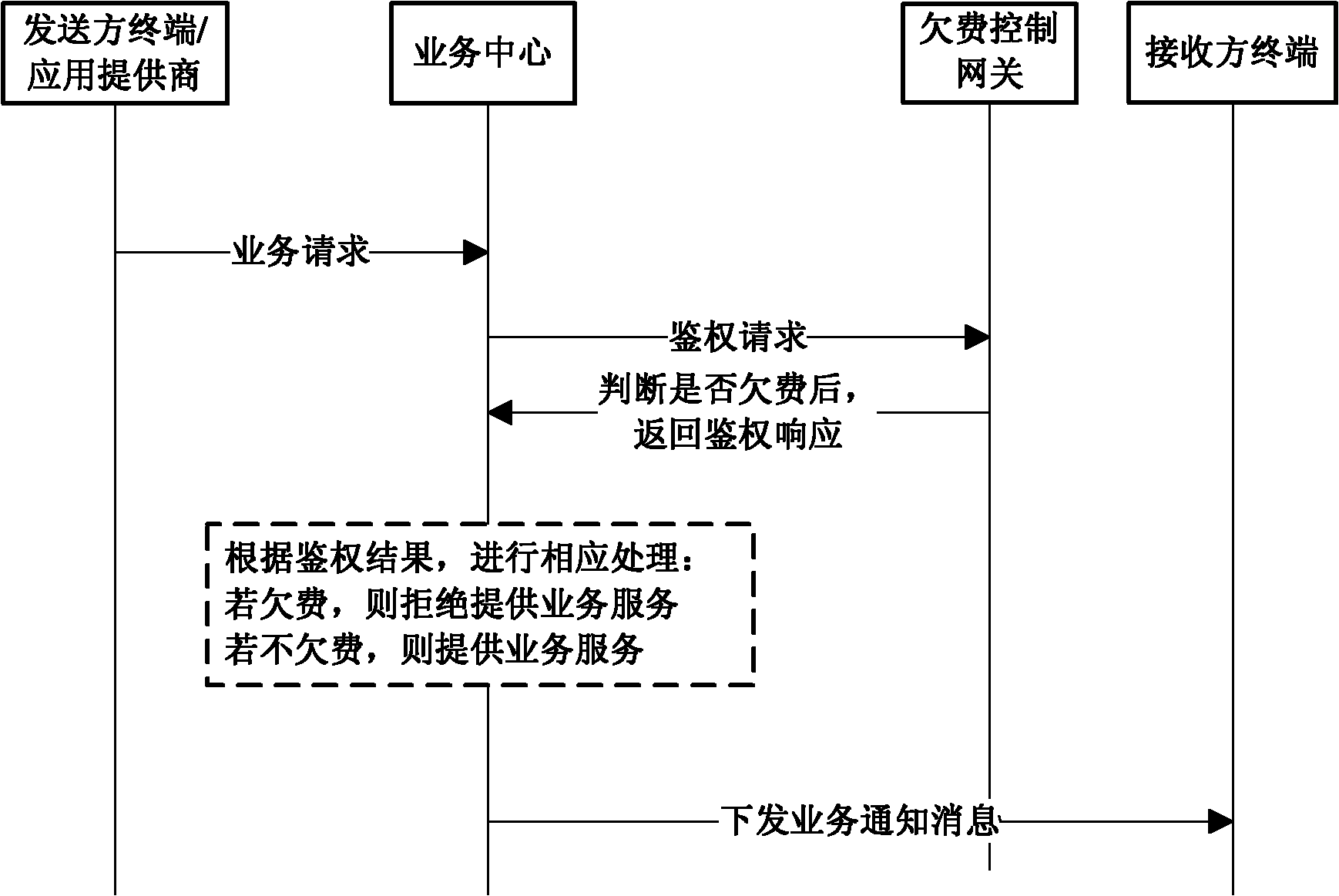
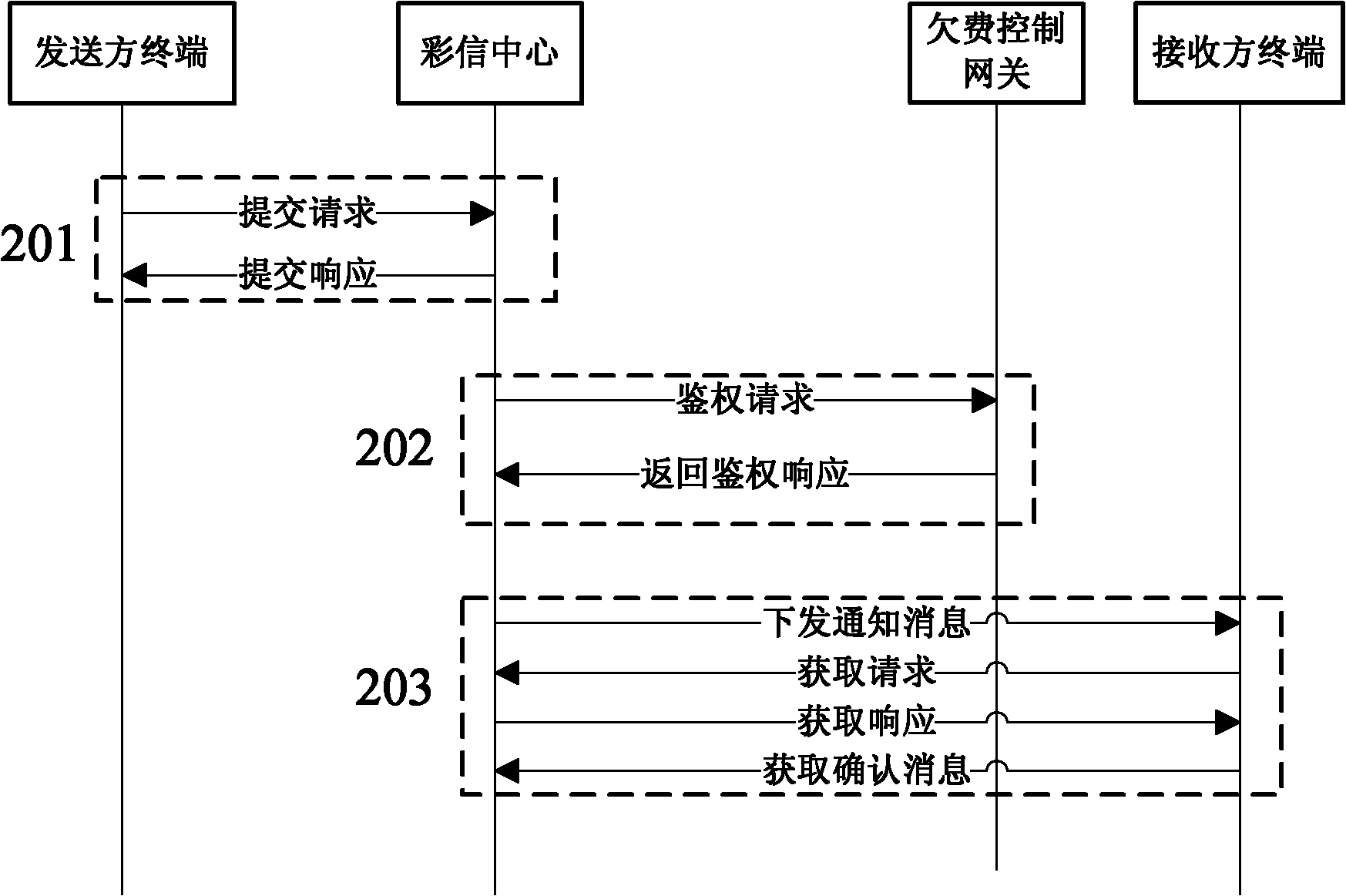
[0047] Such as figure 2 As shown in FIG. 2 , a flow chart of realizing arrears control for the point-to-point (non-forwarding) MMS service is given. The methods of arrears control include:
[0048] Step 201, the sender terminal submits the MMS to the MMS center to which the sender user belongs, and the MMS center immediately returns a submit response message to the sender terminal after receiving the submission request message;
[0049] In step 202, the MMS center conducts normal process authentication (including but not limited to number correctness check, number attribution information verification, etc.) for the submission request message, and enters the authentication process if no problem is found in the authentication.
[0050] First, check if the sending user exists in the greylisted local cache:
[0051] If it does not exist, the verification process ends and directly enters the next step 203;
[0052] If the sender user belongs to the user in the gray list, procee...
Embodiment 2
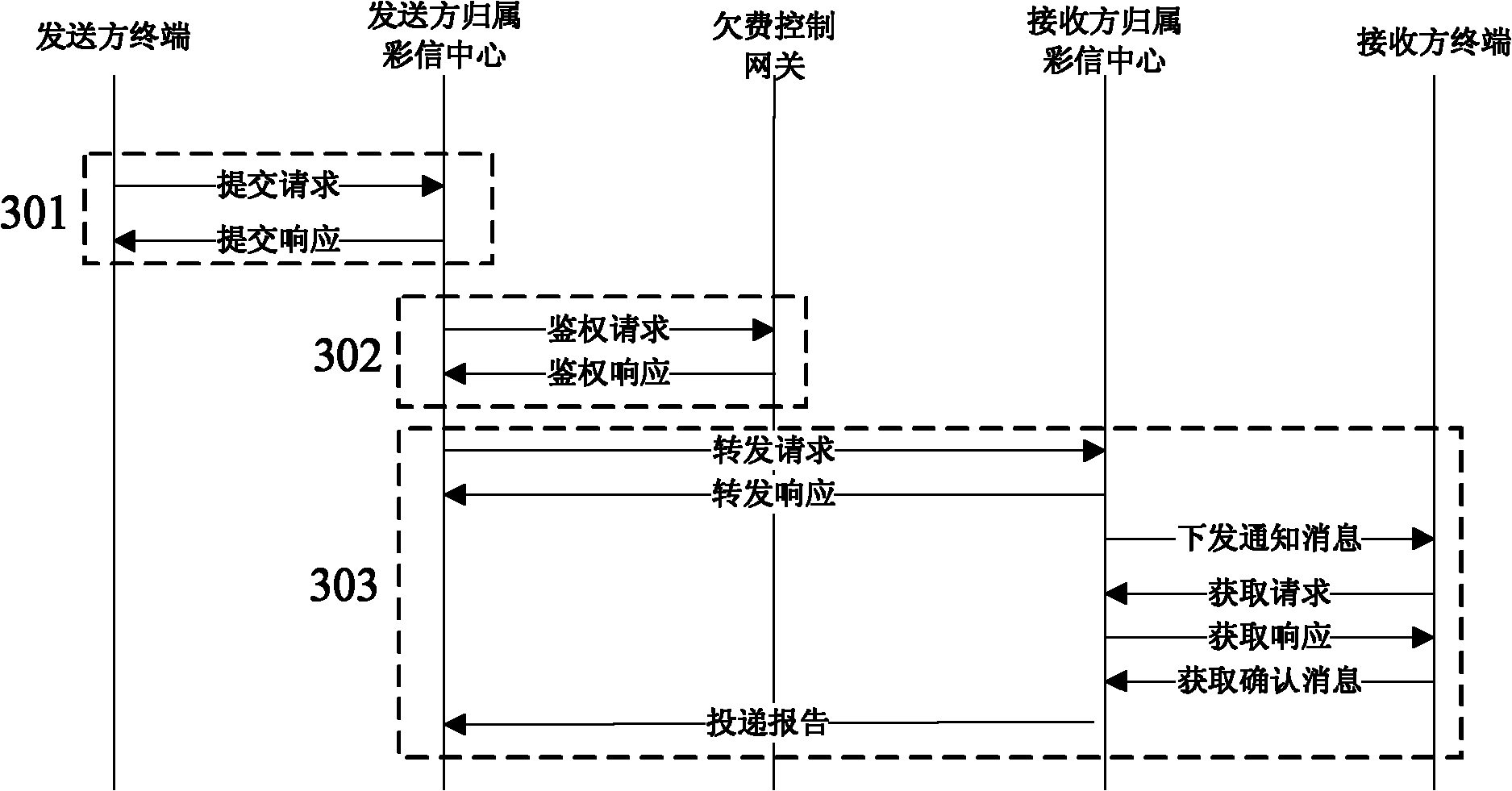
[0060] Such as image 3 As shown, the flow chart of the method for realizing the arrears control of the point-to-point (forwarding) MMS service is provided, and the method for the arrears control includes:
[0061] Step 301, the sender terminal submits the MMS message to the MMS center to which the sender user belongs, and after receiving the submission message, the MMS center to which the sender user belongs immediately returns a submission response message to the sender terminal;
[0062] Step 302, the MMS center to which the sender user belongs carries out normal process authentication (including but not limited to number correctness check, number attribution information check, etc.) for the received submission request message, if there is no problem, then enter this The authentication process of the embodiment.
[0063] First, check if the sending user exists in the greylisted local cache:
[0064] If it does not exist, the verification process ends and directly enters s...
Embodiment 3
[0073] Such as Figure 4 As shown, a flow chart of a method for realizing arrears control of the MMS service sent by an application provider to a terminal is given, and the arrears control method includes:
[0074] Step 401, the application provider submits the MMS to the MMS center to which the application belongs, and the MMS center immediately returns a submission response message to the application provider after receiving the submission message;
[0075] In step 402, the MMS center conducts normal process authentication (including but not limited to number correctness check, number attribution information verification, etc.) for the submitted message. If there is no problem, enter the authentication process of this embodiment.
[0076] First, check if the receiving user exists in the greylisted local cache:
[0077] If it does not exist, the verification process ends and directly enters step 403;
[0078] If the recipient user belongs to the greylist user, perform the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com