Information asset protection method based on intrusion tolerance
An intrusion tolerance and asset technology, applied in the field of information security, can solve problems such as the difficulty of identifying legitimate users, the impossibility of controlling and reviewing the system, and the system being attacked and invaded, and achieves sensitive state switching, high reliability, and low space-time overhead. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
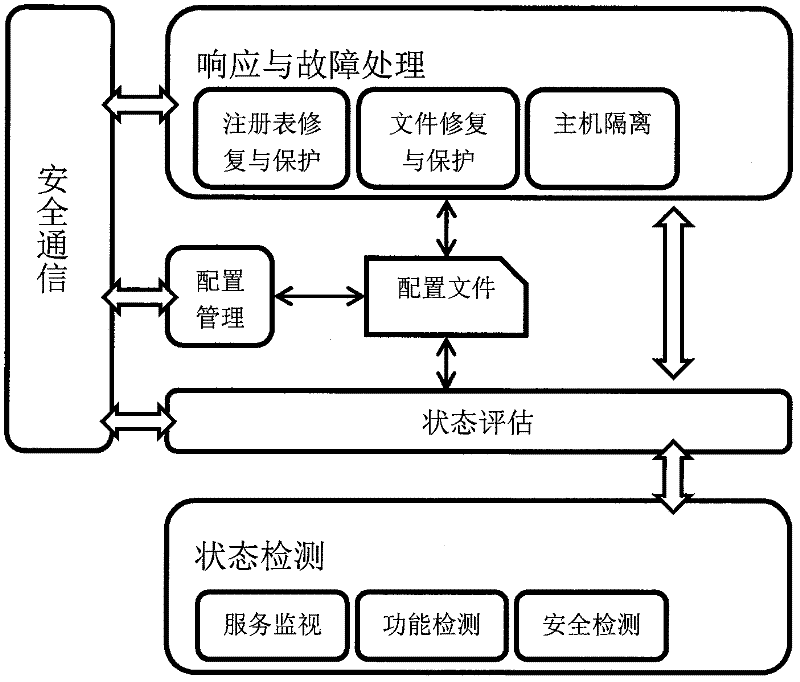
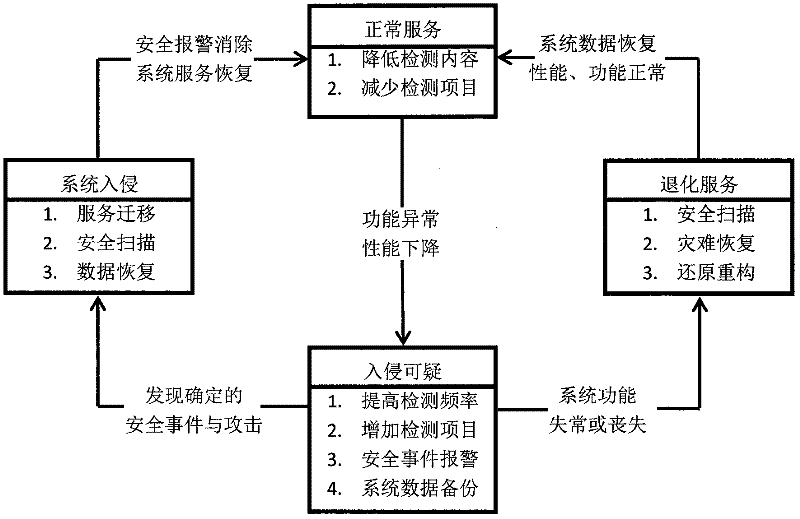
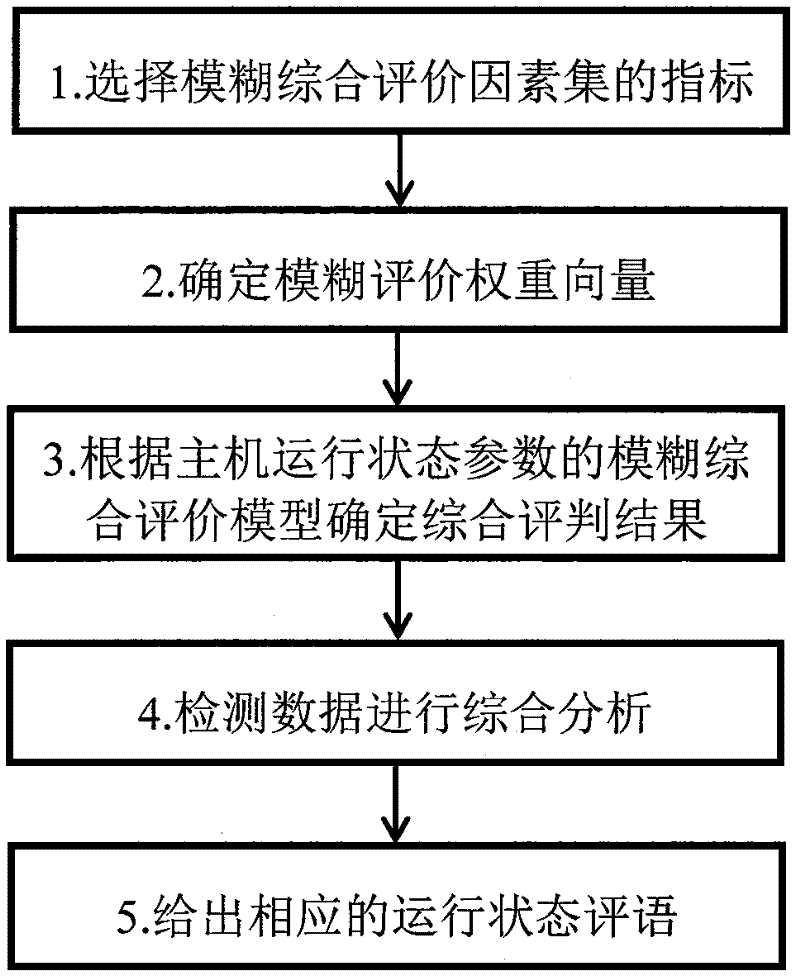
[0014] combine Figure 4 , the present invention discloses an information asset protection method based on intrusion tolerance. Firstly, the core data and service status are detected and monitored. Make an objective evaluation of the status and upload it to the response and fault handling module of the system in the form of an event, and then start the local fault isolation and system restoration and reconstruction mechanism according to the result of the system status evaluation to ensure the confidentiality of core information assets. The invention introduces intrusion tolerance into the design of a single host, and provides basic self-diagnosis, fault isolation, restoration and reconstruction, and secure communication capabilities for a single system in an environment with limited resources.
[0015] like figure 1 , an information asset protection method based on intrusion tolerance, the specific process is as follows:
[0016] (1) The status detection module adopts a dyn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com