User registration and logon method by combining speaker speech identity authentication and account code protection in network games
A technology of identity verification and login methods, which is applied in the field of user registration and login, and can solve problems such as increasing user expenses and loss of account passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
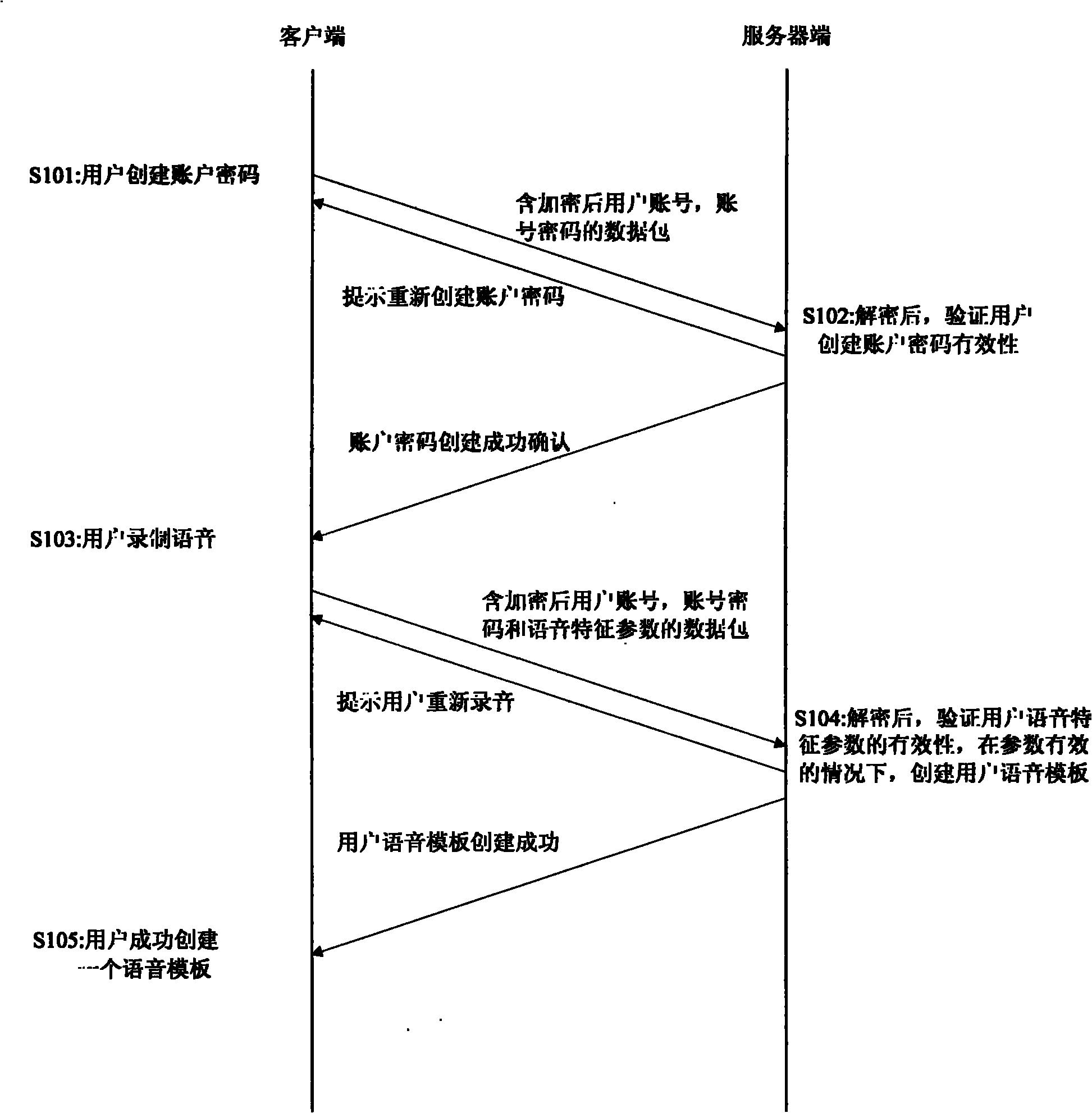
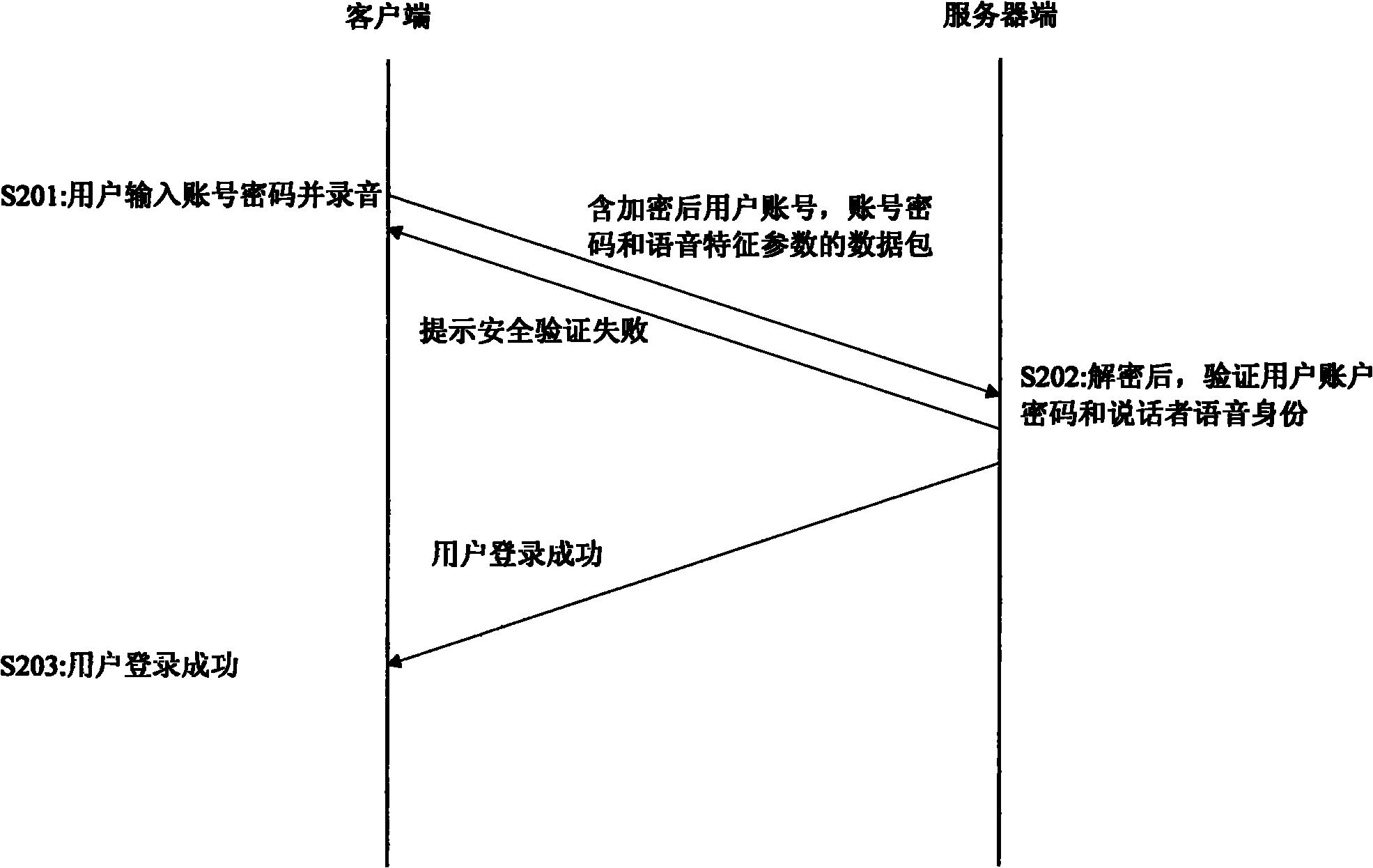
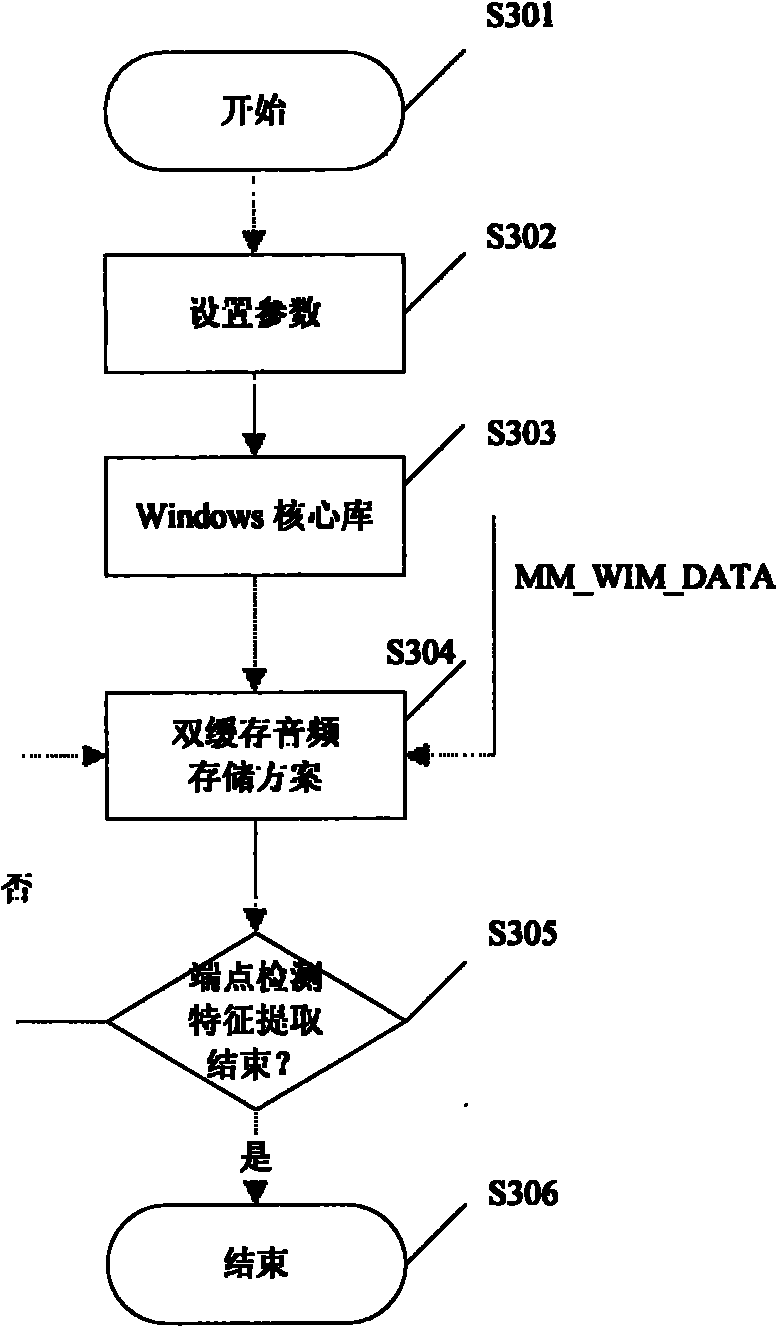
[0020] figure 1 It is a schematic flowchart for users to create account passwords and voice templates according to the embodiment of the present invention. figure 1 The processing shown on the left side of , is executed on the client side, and the processing shown on the right side is executed on the server side. The process starts at step 101, that is, the user creates an account password, and the sending function of the client forms a data packet with the length of the user name, the length of the account password, a random key, the user name and the account password in sequence, and then performs encryption on the data packet according to a certain encryption algorithm. Encrypted and sent to the server. The encryption algorithm here has nothing to do with the essence of the present invention and is well known to those of ordinary skill in the art. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com