Wireless sensor network (WSN) protocol security test system
A technology of security testing and wireless sensors, applied in the field of network information security, can solve the problem of lack of a unified test system in the field of sensor network protocol security testing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
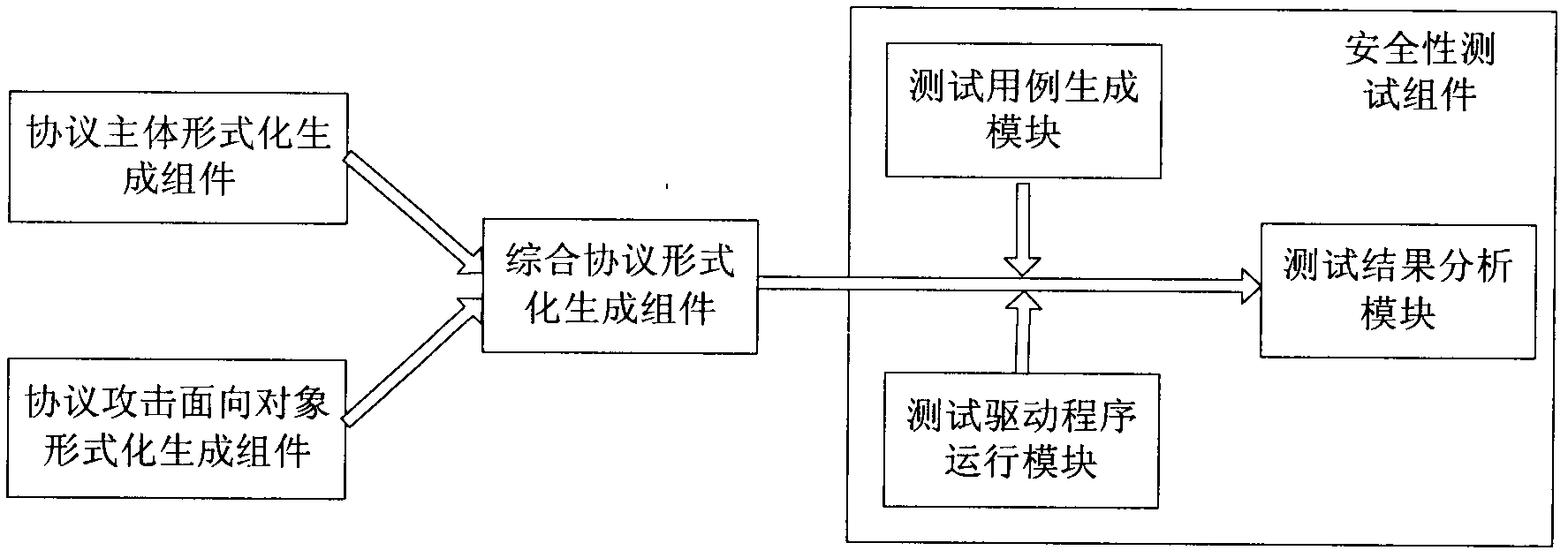
[0057] Based on the wireless sensor network protocol security testing system proposed by the present invention, the wireless sensor network identity authentication protocol TinyPK based on the RSA public key algorithm, the anti-Sybil attack capability is tested for security, and the specific implementation process is as follows:
[0058] 1. Formalized generation components of the protocol body
[0059] The TinyPK protocol adopts a request-response mechanism and requires a CA with a public-private key pair as a trusted third party. Any two entities (external user EP and network node Mote) to establish a trust relationship must have the public-private key pair obtained from the CA and the CA's public key. The entity's public key is signed with the CA's private key as its digital certificate to demonstrate its legal identity. The main body of the TinyPK protocol includes two parties, namely, the external user EP and the network node Mote, and the formalized results Party (1) and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com