Terminal equipment and method for encrypting user information
A technology of terminal equipment and encryption algorithm, applied in the field of communication, can solve problems such as hidden dangers, stealing property and personal privacy, forgetting passwords, etc., to avoid information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
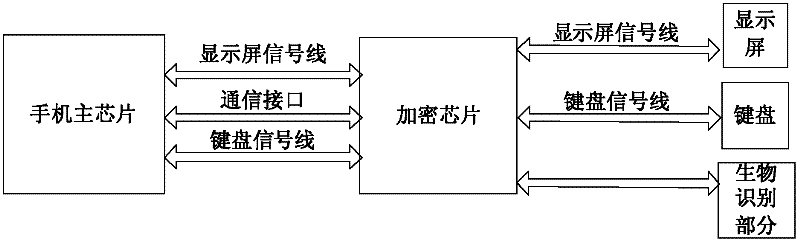
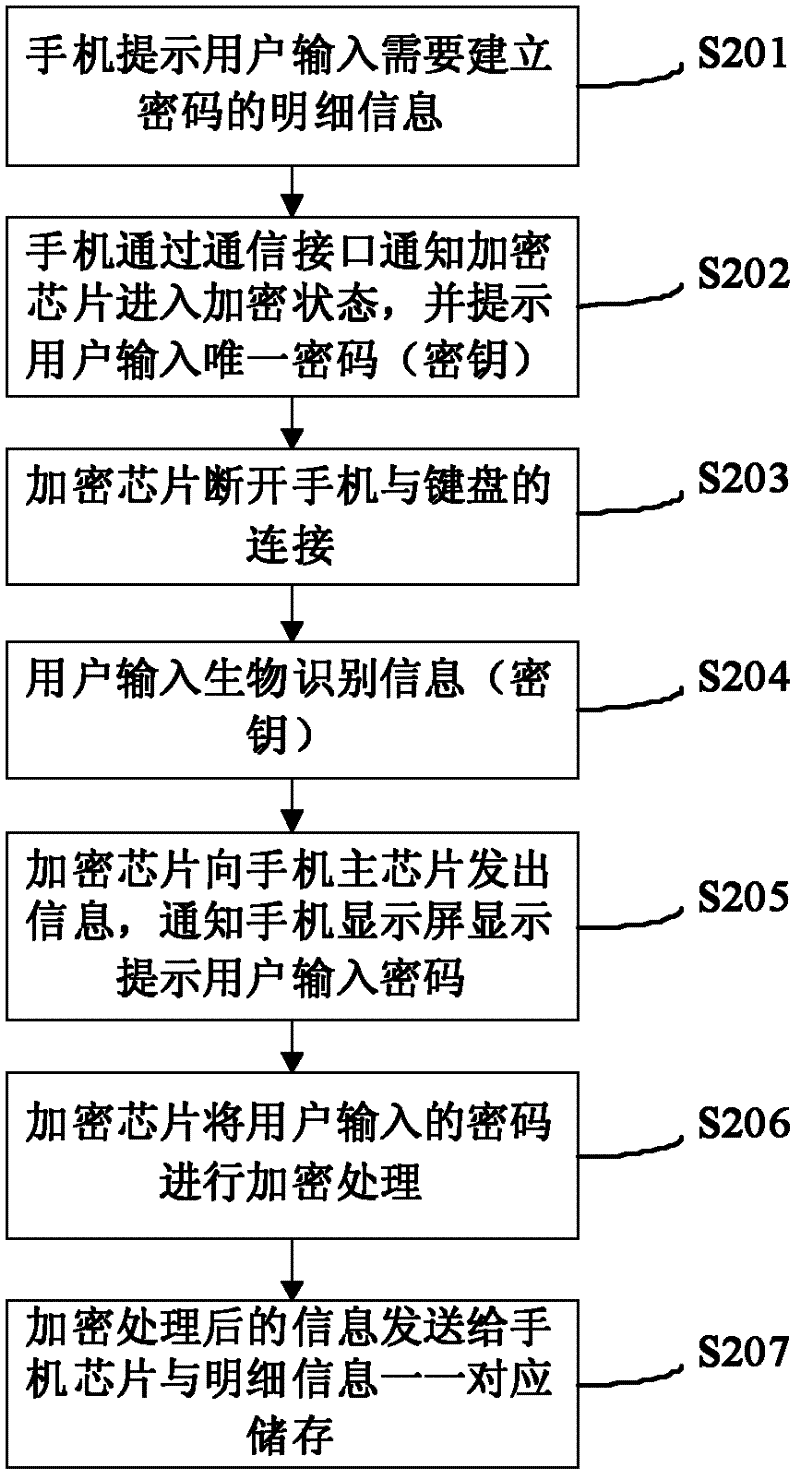
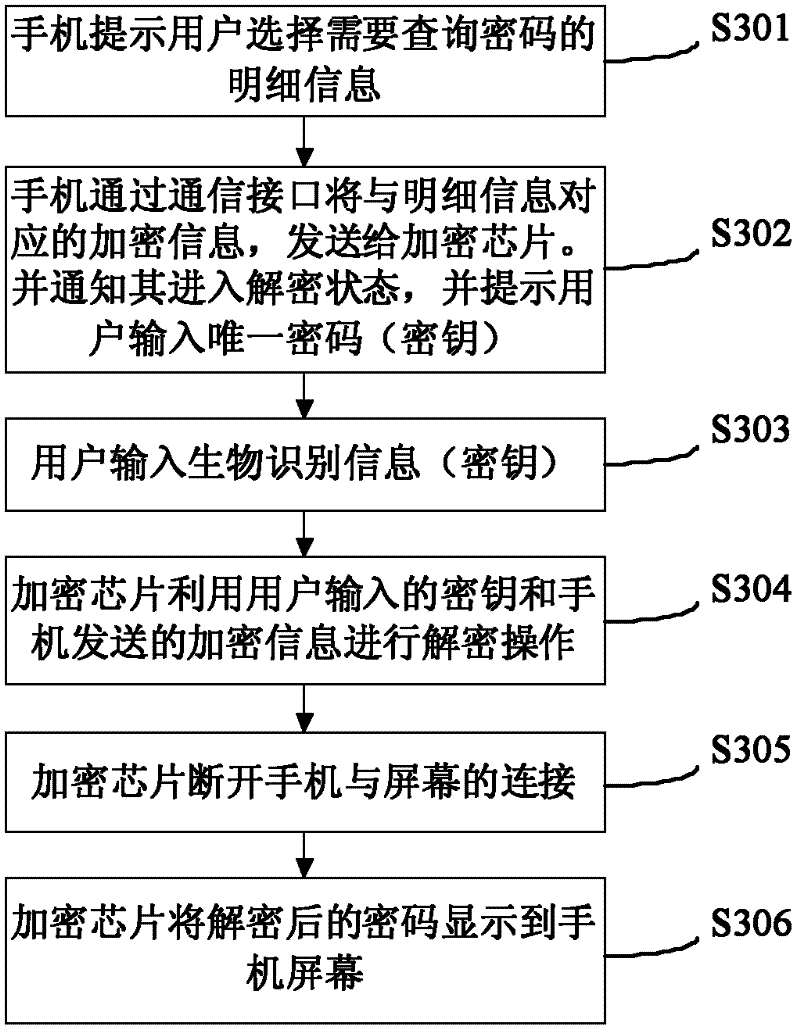
[0031] The present invention overcomes that the encryption and decryption processes existing in the prior art all depend on the software operation in the mobile phone. If the user's mobile phone is implanted with viruses and Trojan horse programs, it can monitor the information in the user's mobile phone memory and steal the password input by the user ( key) or the password output after decryption, causing significant property and economic losses to the user.
[0032] The invention includes two parts, an encryption chip and a terminal body. The encryption algorithm built into the encryption chip can be one or a combination of multiple encryption methods such as AES (Advanced Encryption Standard), DES (Data Encryption Standard), RSA (Rivest Shamir and Adleman), and MD5 (Message Digest Algorithm). The AES128 algorithm is used as an example for illustration.
[0033] The key of the AES encryption algorithm is extracted by the biometric information identification module, and cons...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com