Anomaly detection method for various kinds of intrusion
A technology of anomaly detection and service type, applied in the field of anomaly detection, to achieve the effect of fast classification performance, less training samples, and short training time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
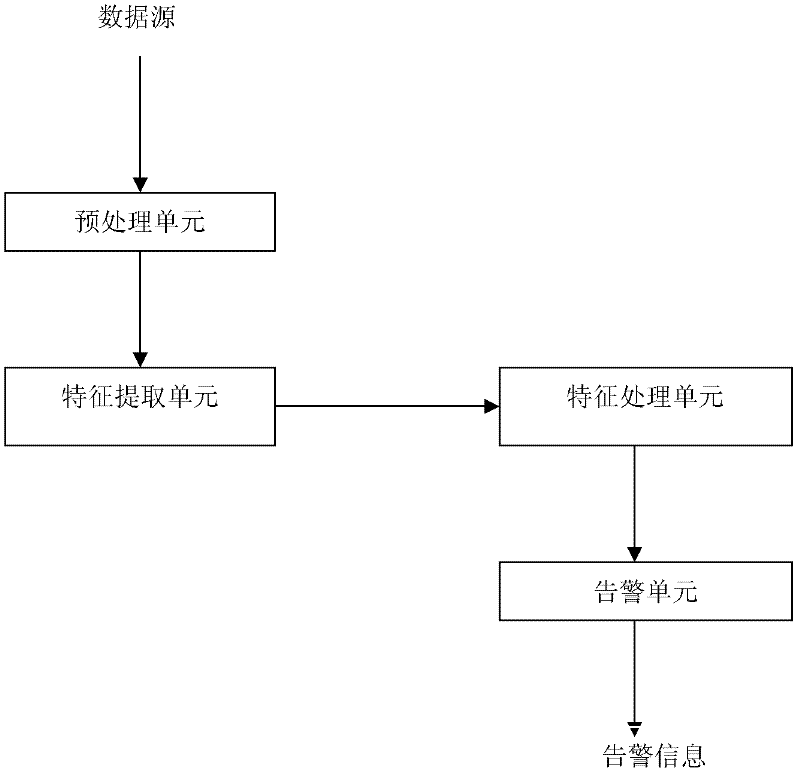
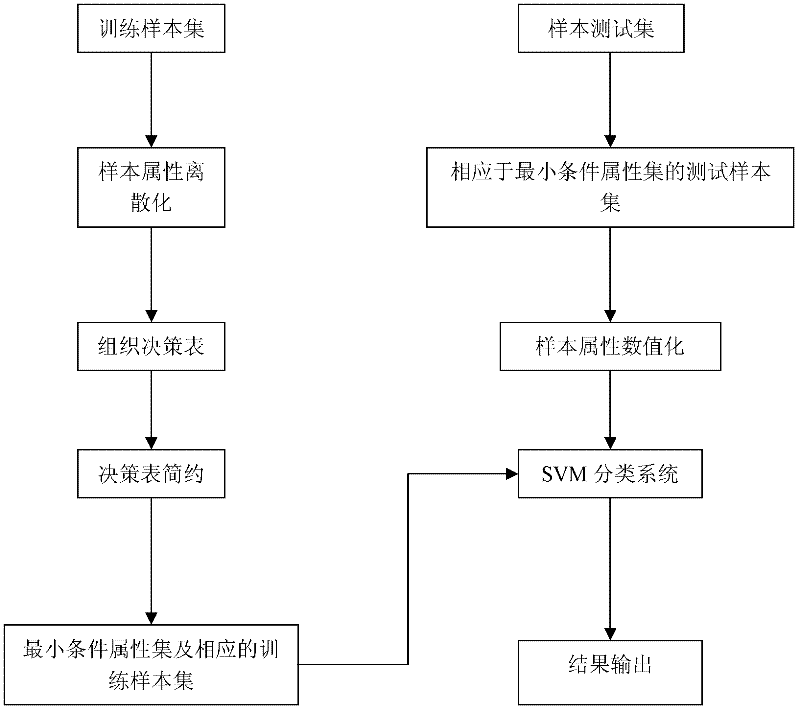
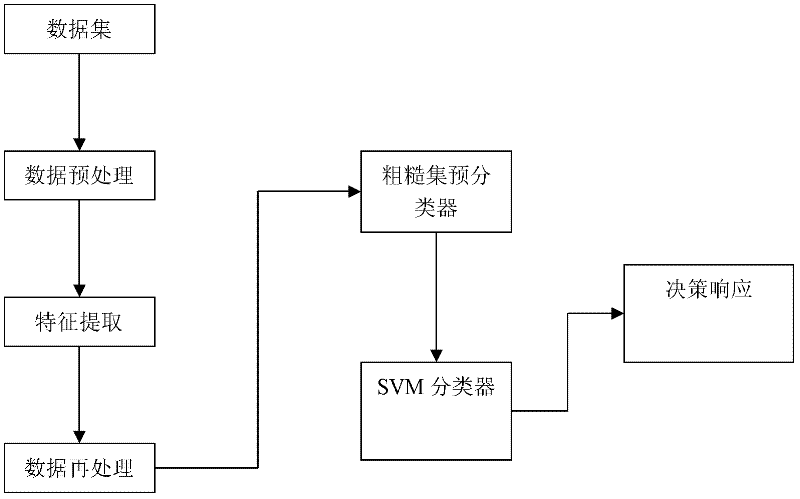
[0037] figure 1 Shown is a general flowchart of network anomaly detection, embedding the feature extraction and feature processing modules proposed by the present invention into figure 1 In, the general framework of the present invention is obtained, such as image 3 shown. The implementation of each module component is as follows:
[0038] 1. Pretreatment
[0039] The data source or original data set is preprocessed before the features are extracted to identify the complete request message, and then divide the network connection by service type, so as to extract relevant features from the connection for training and detection. In the training phase, pure data is generally used to obtain a normal model. In the detection phase, a data set with attacks is used to determine whether the data is abnormal by calculating the deviation from the normal model.
[0040] 2. Feature extraction
[0041] Sign extraction must be complete, accurate, and concise in order to improve the det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com