Information safety coprocessor for performing relevant operation by using specific instruction set
A coprocessor and information security technology, applied in computer security devices, electrical digital data processing, instruments, etc., can solve the problems of complex application, poor performance, cost and ease of use, and the inability of a single-function coprocessor to meet requirements. , to achieve the effect of flexible function and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings. However, these embodiments do not limit the present invention, and any structural, method, or functional changes made by those skilled in the art according to these embodiments are included in the protection scope of the present invention.
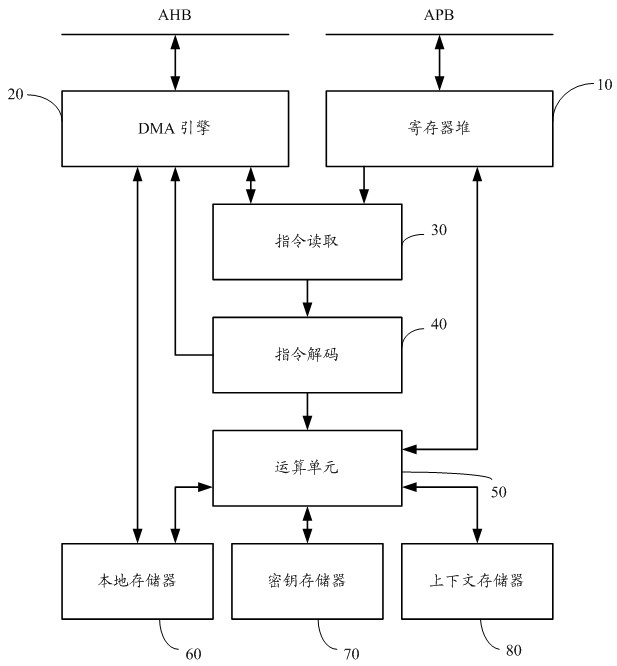
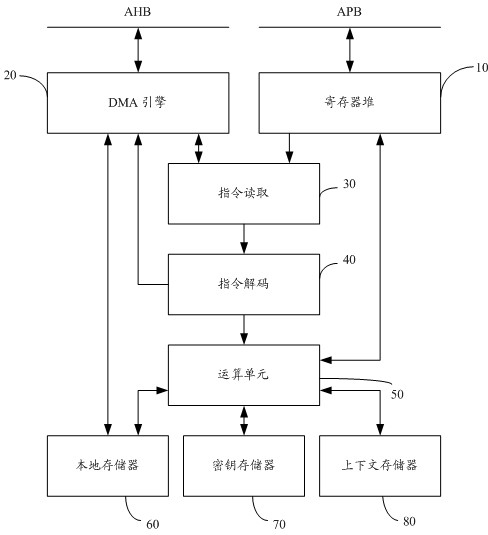
[0036] Please refer to figure 1 As shown, in a specific embodiment of the present invention, an information security coprocessor that performs related operations through a specific instruction set includes the following units:
[0037] Several register files 10: they are configurable registers; wherein, the processor can be controlled externally by reading and writing to the register files through the APB bus. Wherein, the present invention adopts two kinds of buses to carry out data transmission: AHB (Advanced High performance Bus) system bus and APB (Advanced Peripheral Bus) peripheral bus, AHB is m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com