Crypto chip system and secret key extraction method
A cryptographic chip and key technology, applied in encryption devices with shift registers/memory, etc., can solve the problems of difficulty in cloning by adversaries, difficulty in meeting the requirements of high security level keys with reliability and efficiency, and inability to produce PUF, etc. achieve good randomness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
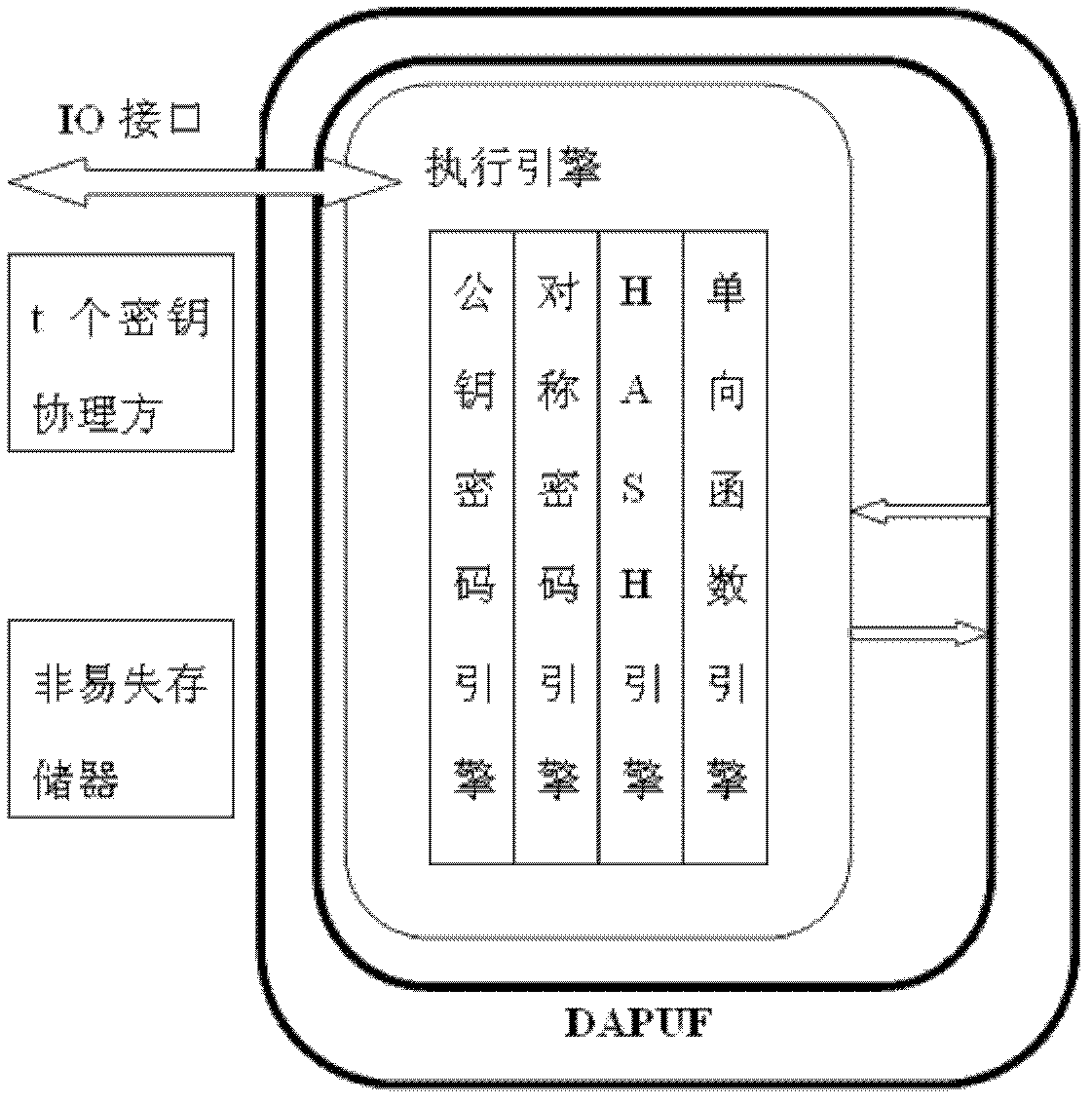
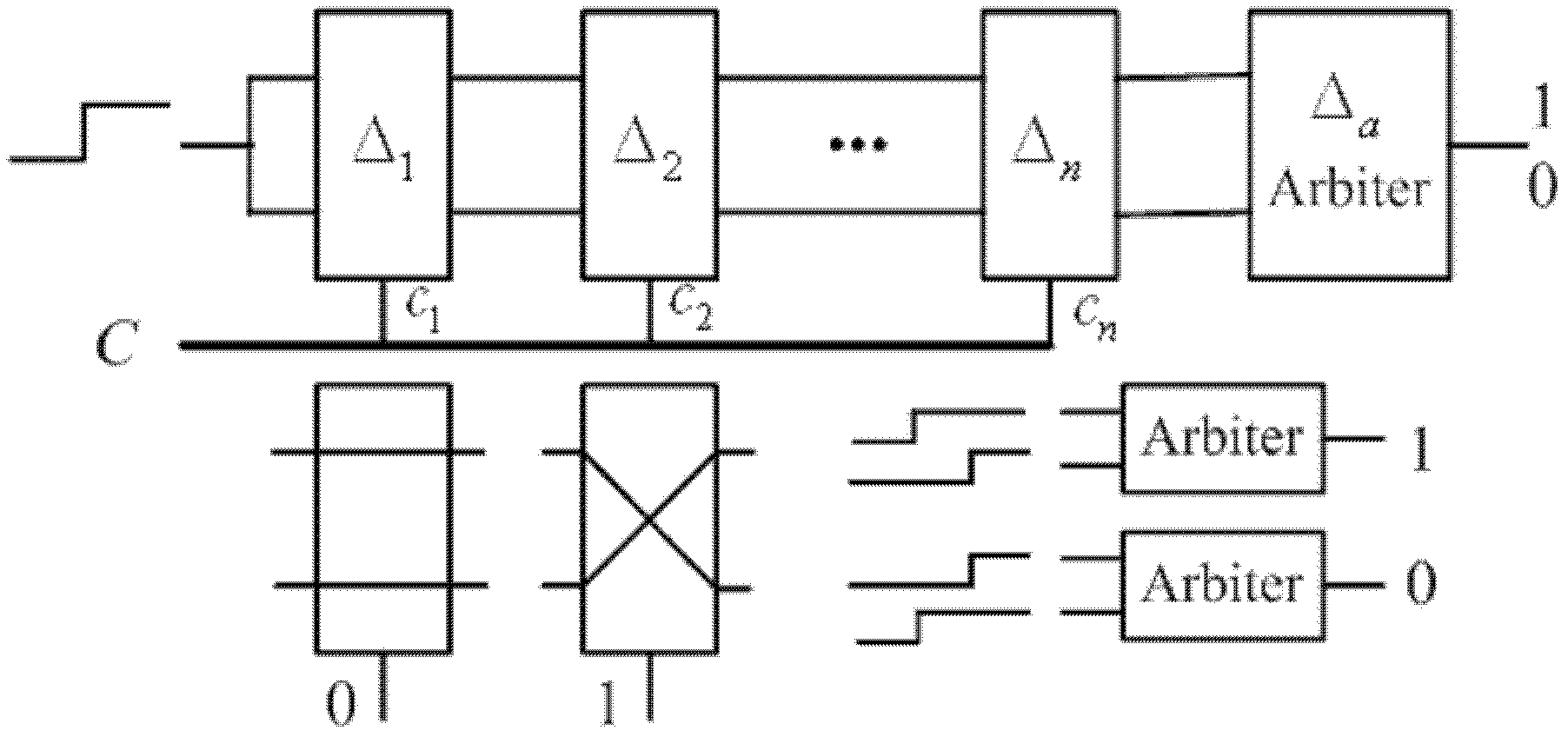
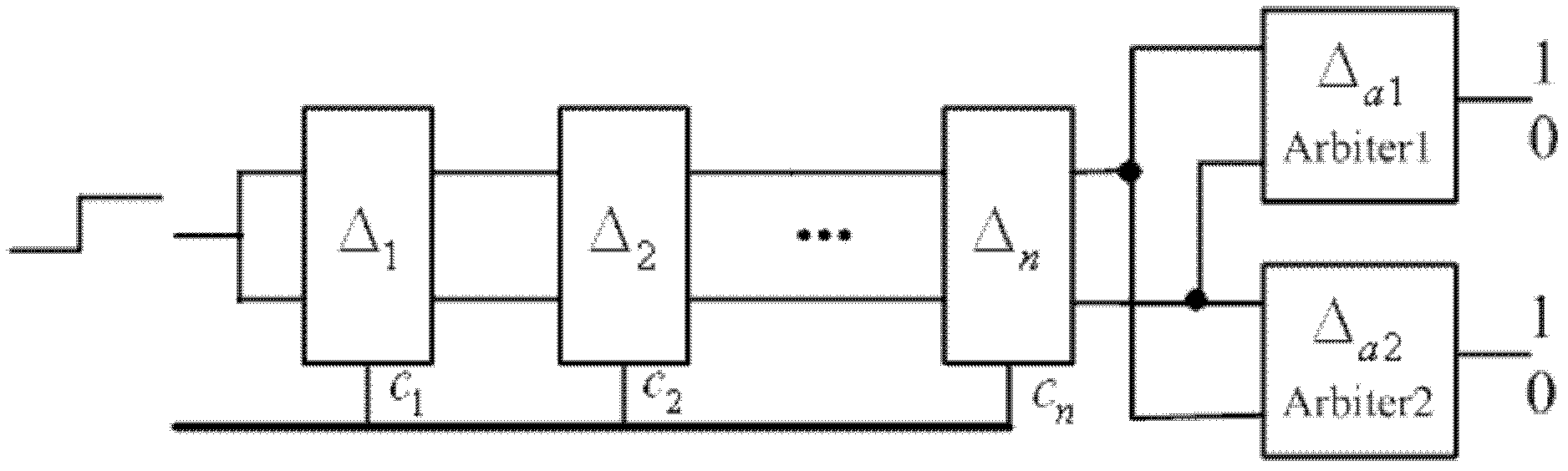
[0068] Such as figure 1 The cryptographic chip shown includes a public key cryptographic engine, a symmetric cryptographic engine, a HASH engine, a one-way function engine, a non-volatile memory, an execution engine, t key coordinators and a dual arbiter physical unclonable module DAPUF, and the DAPUF Sensitive circuits are arranged on the periphery of the encryption chip, forming a cage structure to surround all execution engines. The t cryptographic coordinators are connected through the IO bus, and the non-volatile memory is integrated in the chip.
[0069] The public key cryptographic engine is used to perform encryption and verification of messages, extract keys from DAPUF for decryption and signature, and is also used to perform encryption operations on effective response shares in the key generation phase.
[0070] The symmetric cipher engine is used to encrypt and decrypt information, and the key used may be a key exchanged temporarily or extracted from DAPUF.
[007...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com