Host machine intrusion detection method based on biological immune mechanism
A technology of biological immunity and intrusion detection, applied in the direction of biological models, instruments, platform integrity maintenance, etc., can solve the problems of low efficiency and long algorithm running time, and achieve the effect of high operating efficiency and reduced running time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
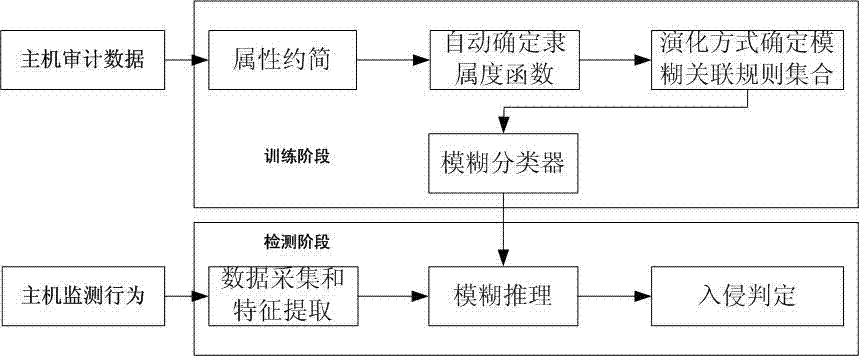
[0038] The present invention will be further described in conjunction with the accompanying drawings and specific embodiments. The present invention mainly relates to the core part of a host intrusion detection system, that is, the algorithm for determining the fuzzy association rule base based on the biological immune mechanism and the fuzzy classification part based on the fuzzy association rule base, and the data source of the host audit data and host monitoring behavior Acquisition and specific responses for different attack types are not described in detail.
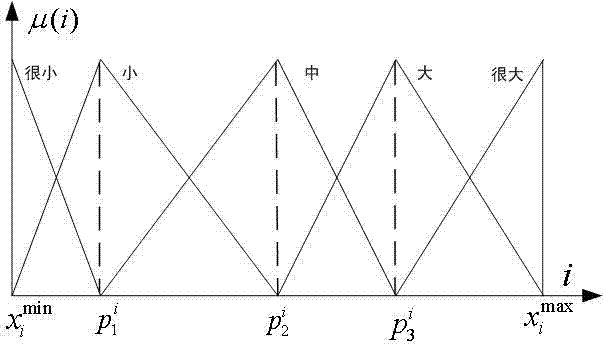
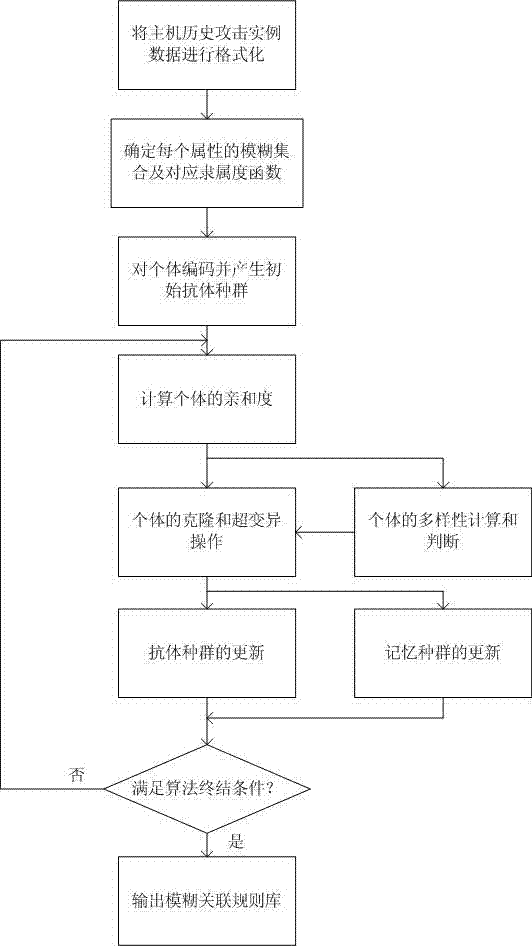
[0039] The present invention first performs attribute reduction and unified coding on the historical intrusion instances in the existing host audit data, and then determines the fuzzy association rule base through population evolution according to the known data sets of these characteristics and categories, which is called the training stage ;Finally, use the obtained fuzzy association rule base to perform intrusion d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com