Method and device for dynamically detecting malicious webpage scripts
A technology for dynamic detection and malicious web pages, applied in computer security devices, special data processing applications, instruments, etc., can solve problems such as browser crashes, and achieve the effect of avoiding crashes, improving reliability and detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
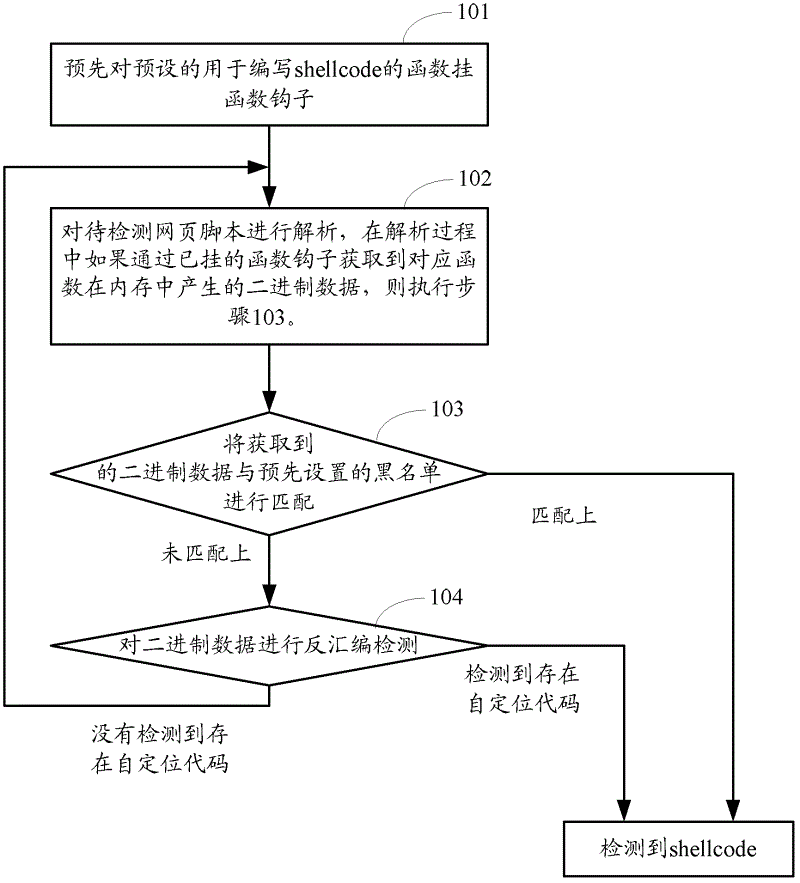
[0067] figure 1 The flow chart of the method provided by Embodiment 1 of the present invention, such as figure 1 As shown, the method may include the following steps:
[0068] Step 101: Preliminary hooking a function to a preset function for writing shellcode.
[0069] Usually, webpage scripts write shellcode through a series of script functions, so that controllable malicious data can be generated in memory for attack, that is, these functions used to write shellcode can generate binary data in a specified format in memory. These preset functions for writing shellcode may include, but are not limited to: the \u function for escaping in javascript-type scripts, the unescape function for string decoding, or string for returning a string represented by an ASCII value. at least one of the fromcharcode function, the unescape function of the vbscript type script, the string.fromcharcode function, or the chrw function for returning the character associated with the specified chara...
Embodiment 2
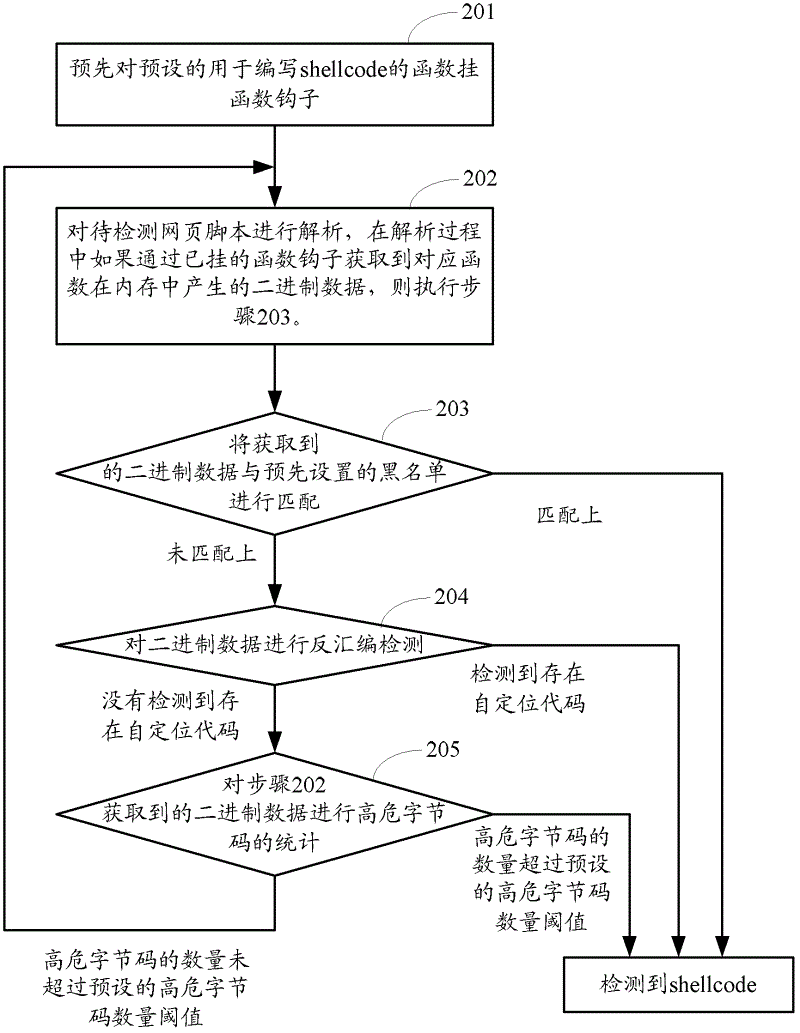
[0082] figure 2 Another method flow chart provided for Embodiment 2 of the present invention, such as figure 2 As shown, the method may include the following steps:
[0083] Step 201 is the same as step 101 in the first embodiment.
[0084] Step 202 is the same as step 102 in the first embodiment.
[0085] Step 203 is the same as step 103 in the first embodiment.
[0086] Similarly, step 203 is also an optional step in this embodiment.
[0087] Step 204 is the same as step 104 in Embodiment 1, but if no self-locating code is detected during the disassembly process, then step 205 is executed.
[0088] Step 205: Perform high-risk bytecode statistics on the binary data obtained in step 202. If the number of high-risk bytecodes exceeds the preset high-risk bytecode threshold, the shellcode is detected; otherwise, go to step 202 to detect the webpage The script continues parsing until parsing ends.
[0089] High-risk bytecode is a feature extracted from a large number of sh...
Embodiment 3
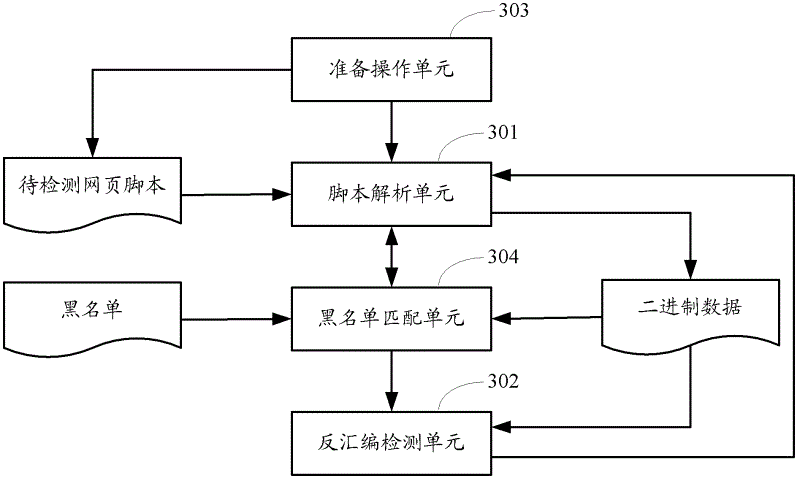
[0105] image 3 The structure diagram of the device provided for Embodiment 3 of the present invention, such as image 3 As shown, the device may include: a script analysis unit 301 and a disassembly detection unit 302 .
[0106] The script parsing unit 301 parses the script of the webpage to be detected. During the parsing process, if the binary data generated by the corresponding function in the memory is obtained through the pre-set function hook for writing the shellcode, the disassembly detection is triggered. Unit 302.
[0107] After being triggered, the disassembly detection unit 302 performs disassembly detection on the binary data, and if a self-locating code is detected during the disassembly process, it is determined that shellcode is detected.
[0108] Since a preparation operation needs to be performed before parsing the webpage script, the device may further include: the preparation operation unit 303 creates a new IE control process, and hooks a preset functio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com