Method for detecting memory leakage of heap operational program
A technology for memory leaks and operating programs, applied in the field of static detection of heap operating program memory leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] specific implementation plan
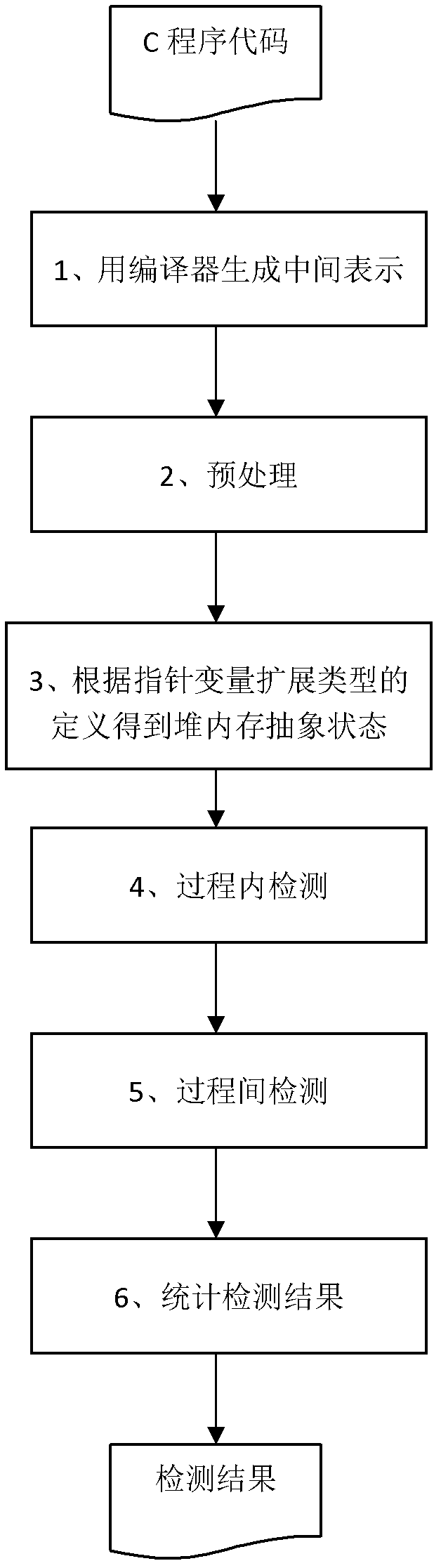
[0068] figure 1 Overall flow diagram of the invention. The input is the source code of the program, and the output is the statements, abstract states, and various statistical information in the program source code that may cause memory leaks.
[0069] The present invention comprises the following steps:
[0070] 1. First, use the compiler platform to analyze the program source code for sentence analysis and lexical analysis, and generate intermediate files, including: abstract syntax tree, control flow graph and procedure call graph.
[0071] 2. Preprocessing, including: slicing and conversion.
[0072] 3. Obtain the abstract state of the heap memory according to the definition of the extended type of the pointer variable in the program.
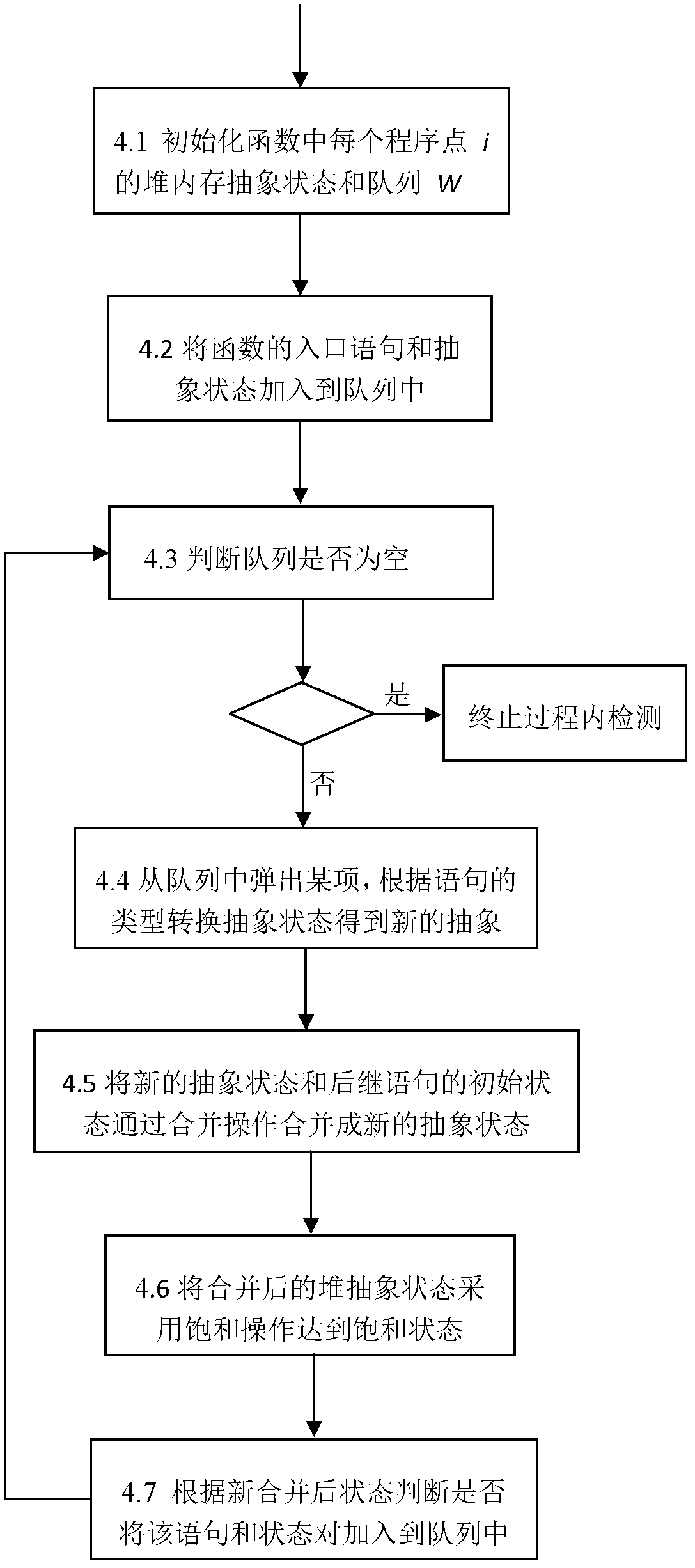
[0073] 4. In-process inspection.
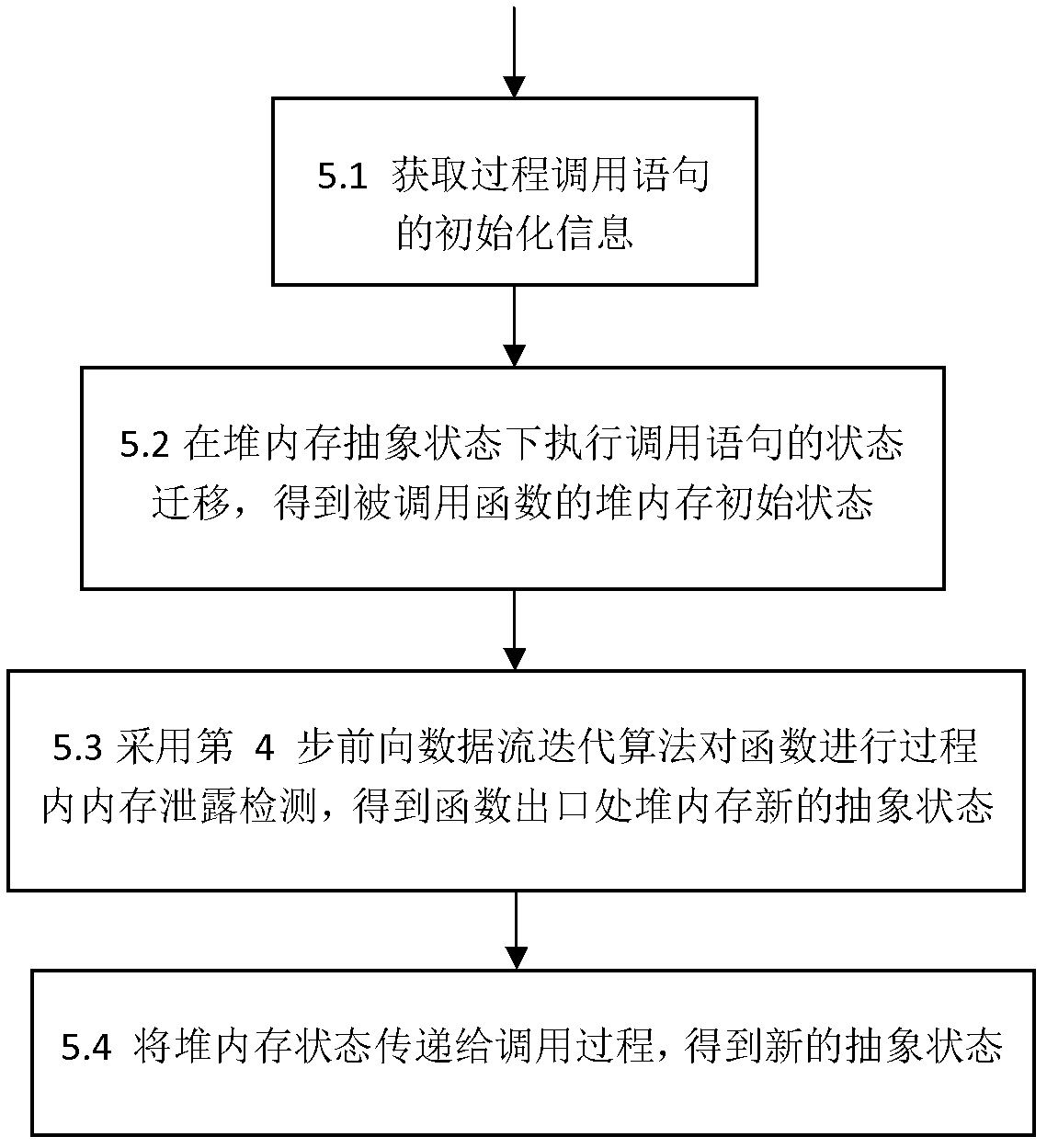
[0074] 5. Inter-process detection.
[0075] 6. Check and count the results of memory leak check detection.
[0076] figure 2 It is a flowchart of detection in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com