Character compression encrypting method
An encryption method and character technology, applied in the field of information security protection, can solve the problems of difficulty in lossless restoration of ciphertext, garbled or wrong information, lossy restoration of ciphertext, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
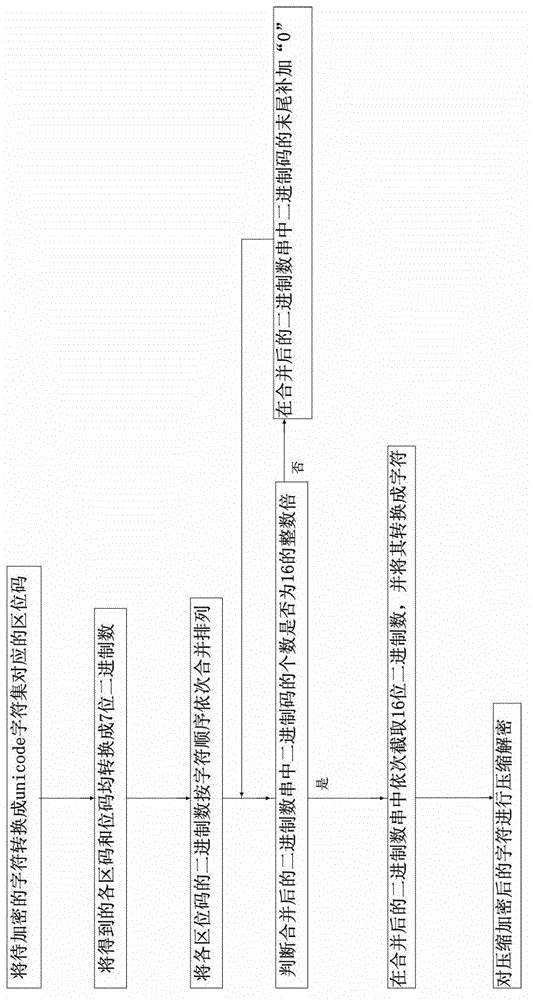
[0035] Embodiment one: if figure 1 Shown, a kind of character compression encryption method comprises the following steps:
[0036] Step 1, convert the character to be encrypted into the location code corresponding to the unicode UTF-16 character set;
[0037] Step 2. Convert each area code and bit code obtained in step 1 into a 7-digit binary number. When the area code or bit code is converted into a binary number with less than 7 digits, add "0" before the high bit until the The binary numbers converted from the above area codes or bit codes are all 7 digits;
[0038] Step 3, merging and arranging the binary numbers of each location code sequentially according to the character order;
[0039] Step 4, judge whether the number of binary codes in the binary number string after merging is an integral multiple of 16; Add "0" to the end of the binary code, until the binary code in the combined binary string is a multiple of 16;
[0040] Step 5, sequentially intercept 16-bit bi...
Embodiment 2
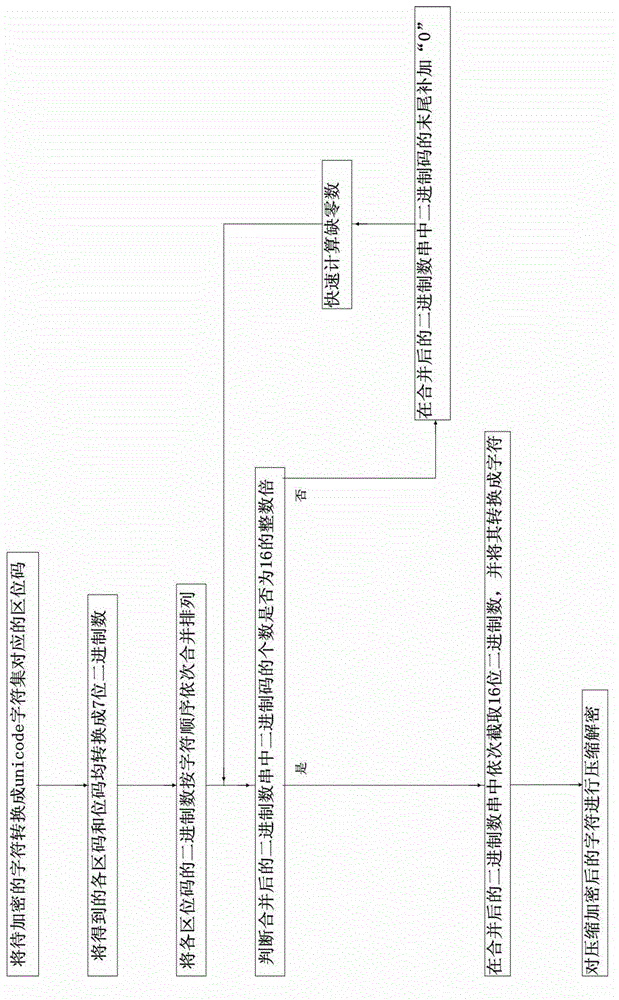
[0046] Embodiment two: if figure 2 As shown, the flow process of this embodiment is basically the same as that of Embodiment 1, the difference is: it also includes the step of quickly calculating the number of missing zeros; The sum of the numbers is an integer multiple of 16;
[0047] A1. Calculate T=16-(2×7×N) mod16, T is the number of missing zeros, N is the number of characters, T≥0, N is a positive integer;
[0048] A2. Add T "0"s at the end of the binary code in the combined binary number string.
Embodiment 3
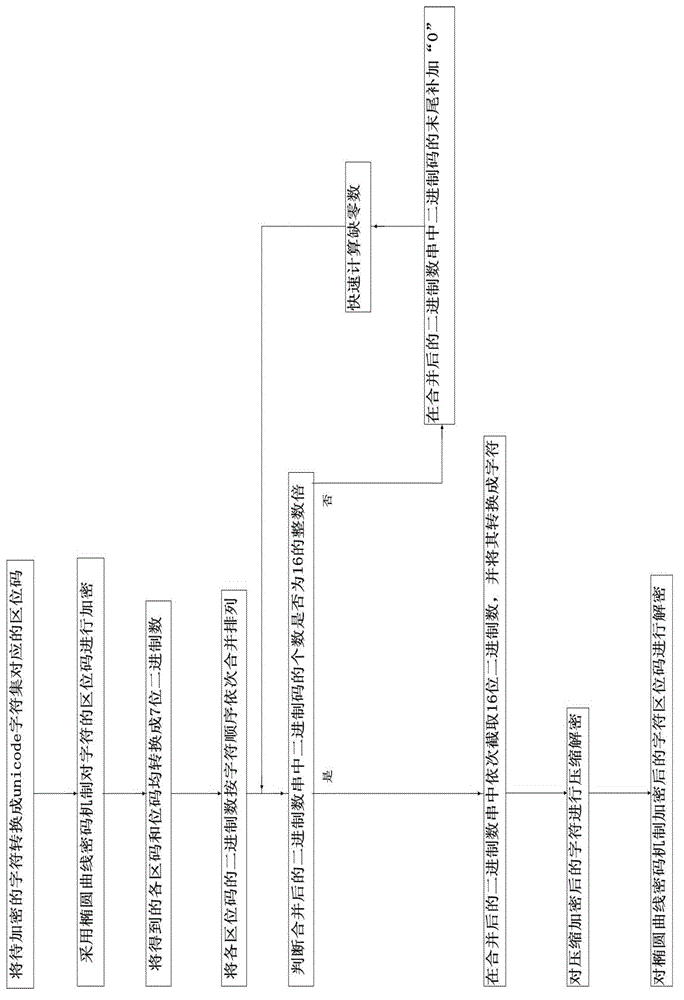
[0049] Embodiment three: as image 3 As shown, the flow process of this embodiment is basically the same as that of Embodiment 2, the difference is: after the character to be encrypted is converted into the location code corresponding to the unicode UTF-16 character set, it also includes the location code of the character using the elliptic curve cryptography mechanism The step of encrypting, correspondingly, also includes the step of decrypting the character location code encrypted by the elliptic curve cryptographic mechanism.
[0050] First construct the Weierstrass equation Y 2 =X 3 +aX+b(modP), where P is a prime number, a and b are non-negative integers less than P, 4a 3 +27b 2 ≠0, define the elliptic curve E on the rational number field P (a,b), on the elliptic curve E P Take a point G with prime number order n on (a, b), choose a private key k in the interval [1, n-1] to calculate the public key Q, Q=k×G, k is a positive integer , where G, P, and Q are all public...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com