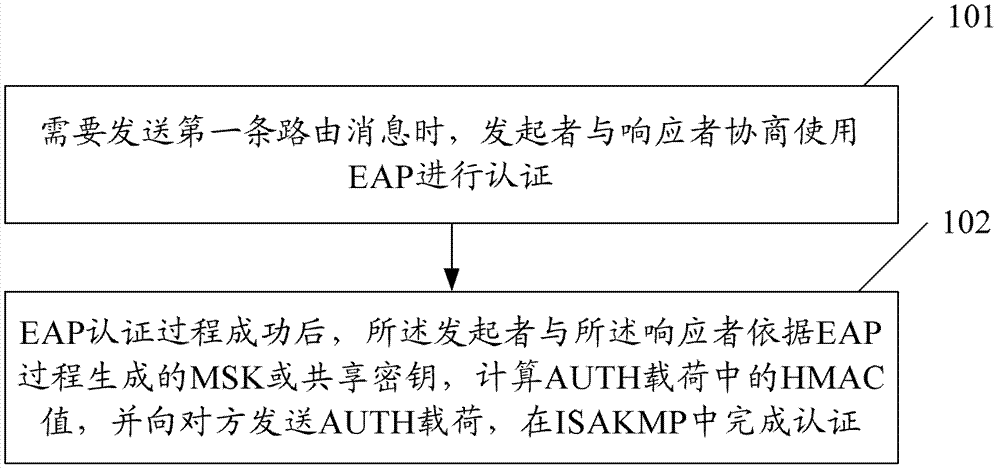
Extensible authentication method and system based on ISAKMP (Internet Security Association and Key Management Protocol)
An extended authentication and responder technology, which is applied in the transmission system and key distribution, can solve the problems that are not conducive to long-term key update, adding and removing routing equipment, configuration trust relationship is impossible to realize, and the selection range of authentication mechanism is limited.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
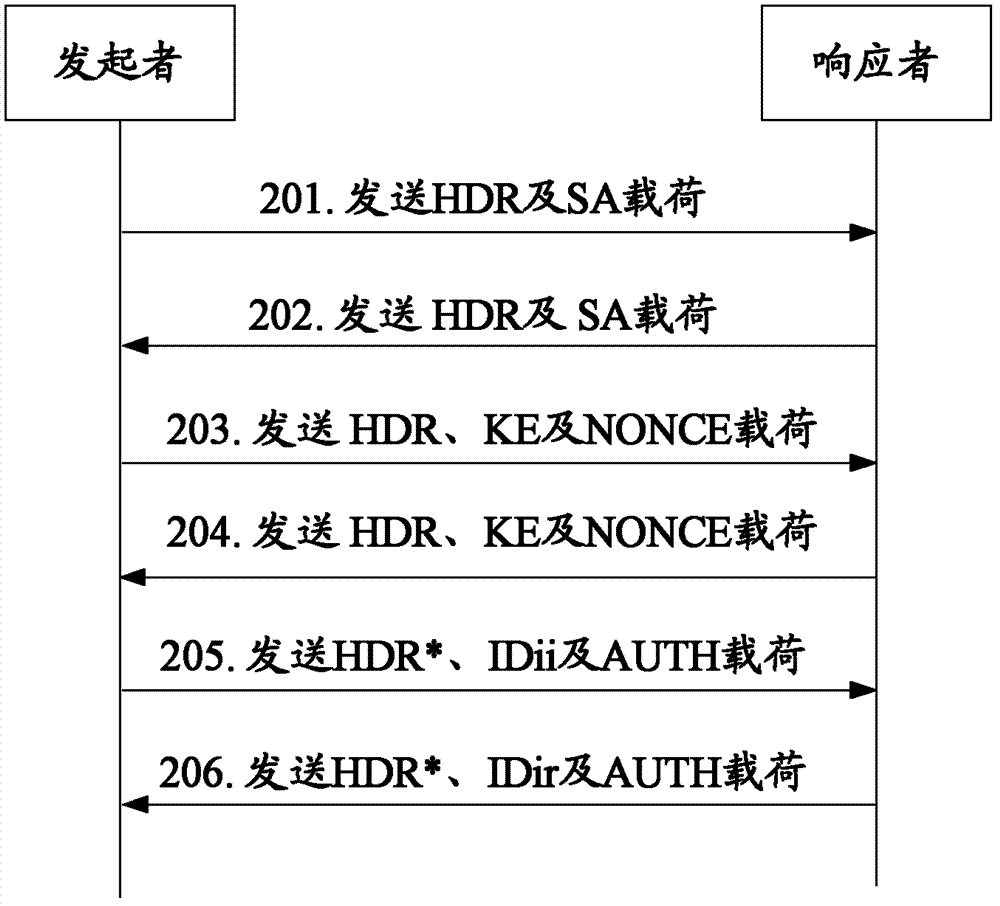
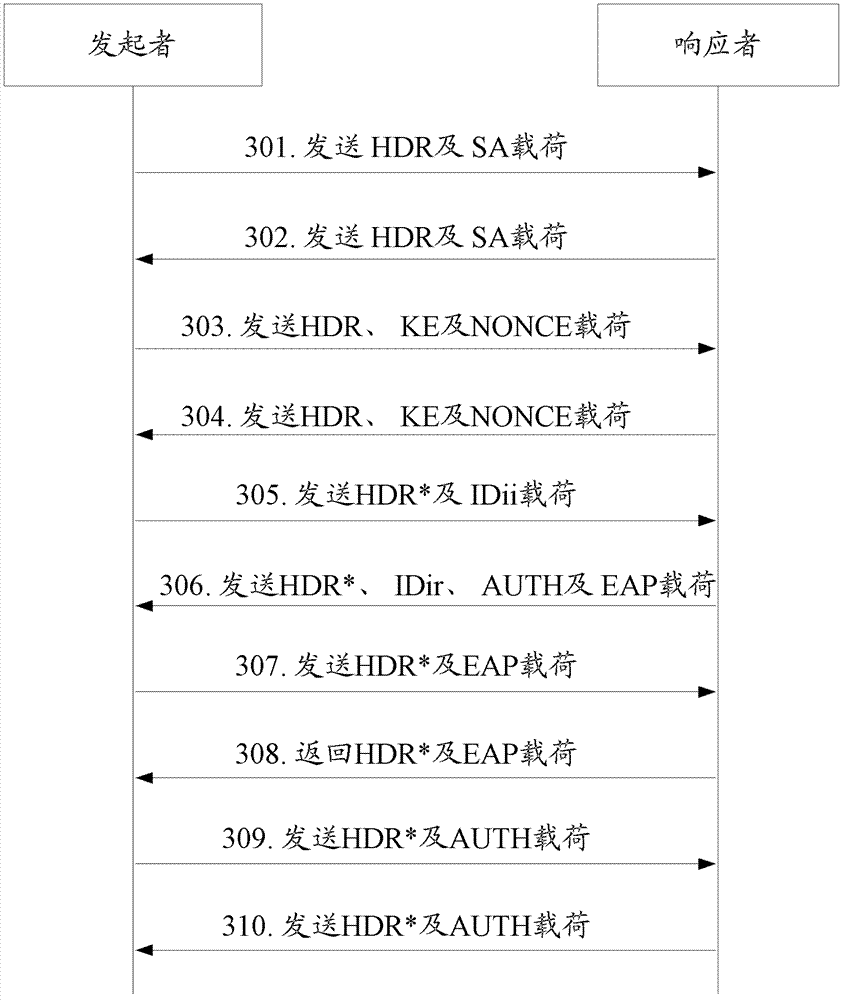
[0125] The application scenario of this embodiment is: the shared key k has been configured in advance between the initiator and the responder ab , the initiator and the responder can be in any position on the network, and use the IP protocol to communicate. Wherein, the initiator refers to the router sending the routing message, and the responder refers to the router receiving the routing message. In this embodiment, EAP is extended to ISAKMP, and the identity protection exchange based on ISAKMP uses the EAP method for authentication, such as image 3 shown, including the following steps:
[0126] Step 301: When the first routing message needs to be sent, the initiator sends the SA payload to the responder;
[0127] Step 302: the responder sends the SA payload to the initiator;
[0128] So far, the initiator negotiates with the responder to establish an ISAKMP SA.
[0129] Step 303: The initiator sends the KE payload and the NONCE payload to the responder;
[0130] Step ...
Embodiment 2
[0146] The application scenario of this embodiment is: no trust relationship is configured between the initiator and the responder, and the trust relationship k is configured in advance between the initiator and the Diameter server ac , the trust relationship k has been configured in advance between the responder and the Diameter server bc , the initiator and responder use ISAKMP for interaction, and the responder and Diameter server use Diameter-ISAKMP for interaction. Wherein, the initiator refers to the router sending the routing message, and the responder refers to the router receiving the routing message. This embodiment introduces the Diameter server's extended authentication method based on ISAKMP, such as Figure 4 shown, including the following steps:
[0147] Step 401: When the first routing message needs to be sent, the initiator sends the SA payload to the responder;
[0148] Step 402: the responder sends the SA payload to the initiator;
[0149] So far, the in...
Embodiment 3
[0172] The application scenario of this embodiment is: no trust relationship is configured between the initiator and the responder, and the trust relationship k is configured in advance between the initiator and the Diameter server ac , the trust relationship k has been configured in advance between the responder and the Diameter relay server bd , the trust relationship k has been configured in advance between the Diameter relay server and the Diameter server cd . Because the trust relationship between the Diameter relay server and the initiator is not configured in advance. Wherein, the initiator refers to the router sending the routing message, and the responder refers to the router receiving the routing message. This embodiment introduces the ISAKMP-based extended authentication method of the Diameter relay server, such as Figure 5 shown, including the following steps:
[0173] Step 501: When the first routing message needs to be sent, the initiator sends the SA payloa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com