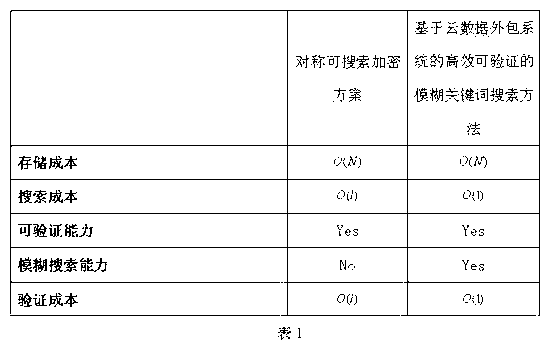
Efficient verified fuzzy key word searching method based on cloud data subcontract system
A technology of keyword search and cloud data, which is applied in the field of cloud computing security, can solve the problem of not considering the verifiability of keyword search, etc., and achieve the effect of high efficiency, completeness and correctness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] Below by embodiment the present invention will be further described:
[0018] Based on the efficient and verifiable fuzzy keyword search method of the cloud data outsourcing system, the cloud data outsourcing system is constructed firstly, the cloud data outsourcing system includes the data owner, the authorized user and the cloud server. by A collection of encrypted data files and exact key set , which is scanned by the data owner to encrypt the document Then create a precise keyword set , the data owner outsources the encrypted files to the server and gets the address of each document , for all sets containing exact keywords The corresponding exact keywords in The file of the document records its address set as: , It is an integer greater than or equal to 1, and the cloud server can provide encrypted document sets for authorized users The fuzzy keyword search service on the cloud, and the data owners and authorized users have been assigned their co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com