Dynamic multi-access business distributing method in isomerism cooperative network
A collaborative network and multi-access technology, applied in network traffic/resource management, network planning, electrical components, etc., can solve problems that affect the performance of business distribution and do not consider the rate of multi-mode terminals for business bursts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
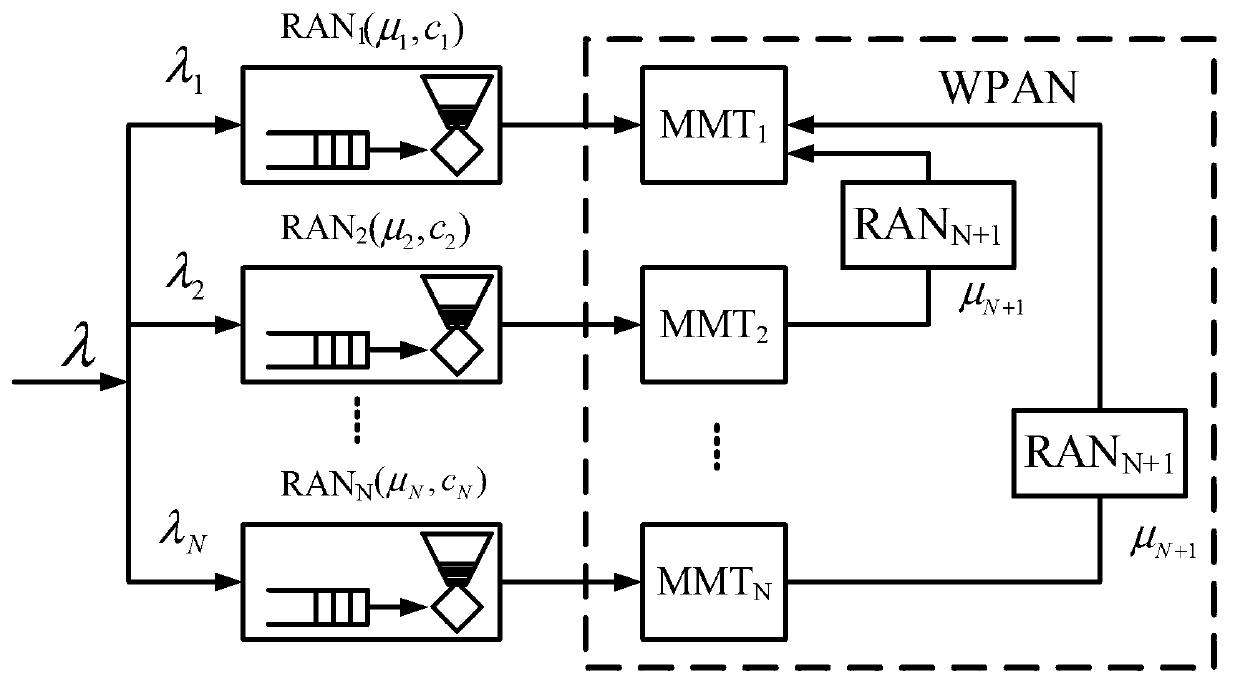
[0061] Please refer to figure 1 , The present invention restricts and smooths the suddenness of the business by adding the token funnel in the wide area network. figure 1 In the heterogeneous network scenario where WWAN and WPAN cooperate, there are N different WWANs and one WPAN composed of multiple MMTs. For the convenience of description, different WWAN is expressed as RAN={RAN1,RAN2,...,RANN}, WPAN is expressed as RANN+1, and different MMT is expressed as MMT={MMT1,MMT2,...,MMTM}. In this heterogeneous network, assuming that there is data to be transmitted from WWAN to MMT1, the input service flow can be divided into multiple service sub-flows, which are respectively transmitted to it through different WWANi,i∈{1,...,N} Associated MMTj,j∈{1,...,M}, and then different MMTs in WPAN coordinated transmission, the divided data stream finally arrives at MMT1, and the sub-stream aggregation recovery is realized at MMT1, thus completing the end-to-end coordinated transmission. Assu...
Embodiment 2
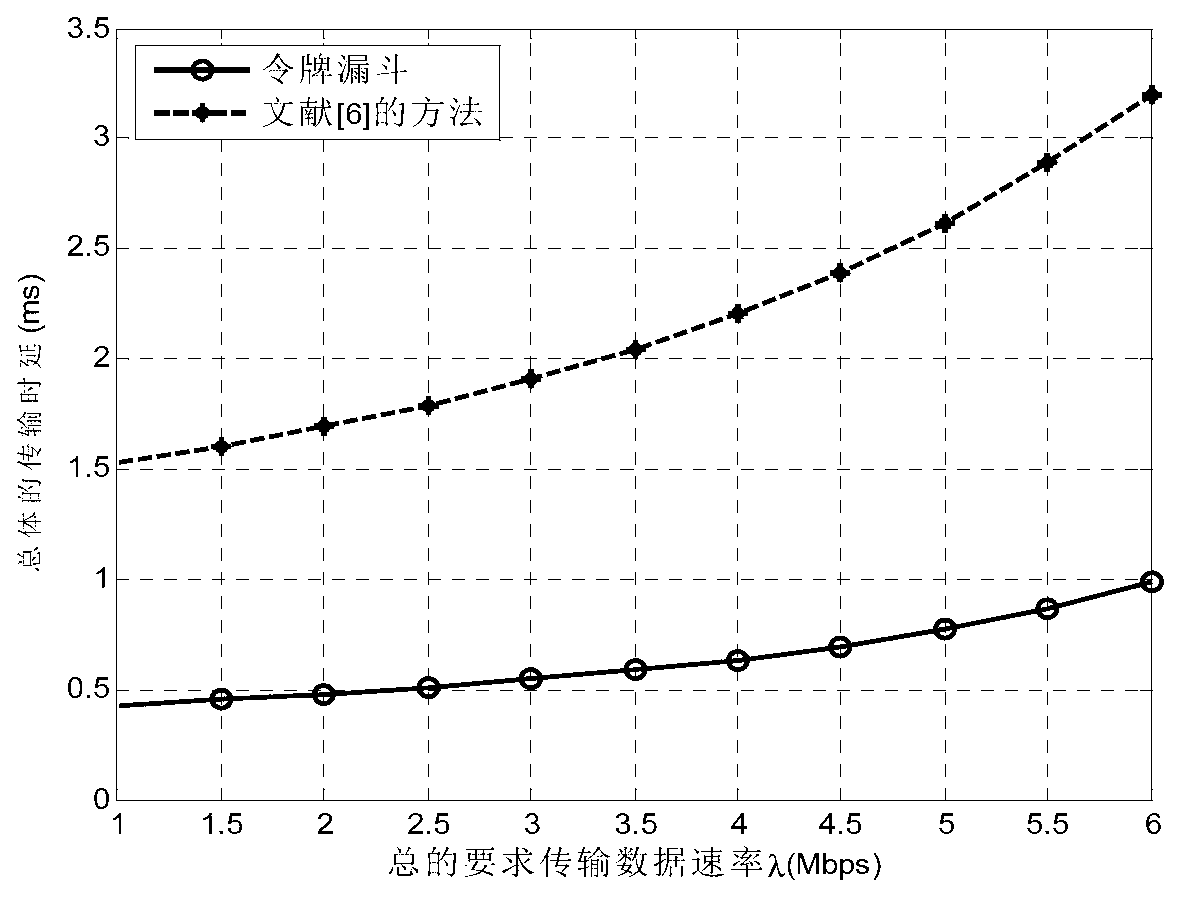
[0064] Please refer to figure 2 , This paper considers the problem of shunt optimization based on token funnel. The speed of token generation is the speed of the bit stream that can be allowed to enter the network is rb / s, and the capacity of the funnel is Wbit. Then the average time for transmitting a packet is μ=r / L. It is the time that the token can accumulate, and the average delay of the packet passing through the token funnel system is [8]:
[0065] T = 1 μ - λ e - c ( μ - λ ) - - - ( 1 )
[0066] The time c that the token can accumulate is related to the transmission rate that the terminal can provide (c≤μ N+1 ).
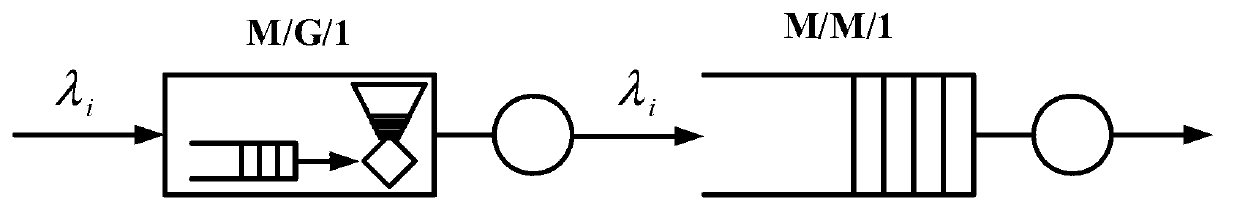
[0067] Due to the rate control strategy of adding the token funnel in WWAN, the business distribution of packets arriving at MMT is uncertain. Below we take i∈{2,...N} as an example for analysis as figure 2 Shown.
[0068] The output of the token funnel is determined by the input business flow and service c...
Embodiment 3
[0079] Distributed solution method based on duality
[0080] For the solution of the optimization problem (P), the Lagrange function is transformed into:
[0081] L ( λ i , v ) = X i = 1 N 1 μ i - λ i e - c i ( μ i - λ i ) + X i = 2 N 1 μ N + 1 - λ i + v ( X i = 1 N λ i - λ )
[0082] s.t 0 ≤ λ i μ i ‾ , ∀ i - - - ( 7 )
[0083] Where v∈R is the Lagrangian multiplier corresponding to constraint (5). The dual function can be expressed as:
[0084] g ( v ) = min 0 ≤ λ i μ i L ( λ i , v ) - - - ( 8 )
[0085] Corresponding to the dual problem of the original problem:
[0086] max v A R g ( v ) - - - ( 9 )
[0087] It can be proved that the original problem is a convex opt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com