A secure storage device account input and authentication method
A technology of secure storage and authentication methods, applied in the field of secure mobile storage devices, can solve the problems of counterfeiting, inconvenience, and inability to be used by many people, and achieve the effects of improving security, ensuring security, and facilitating self-management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
[0025] First, the hardware basis of the device of the specific embodiment of the present invention is described:
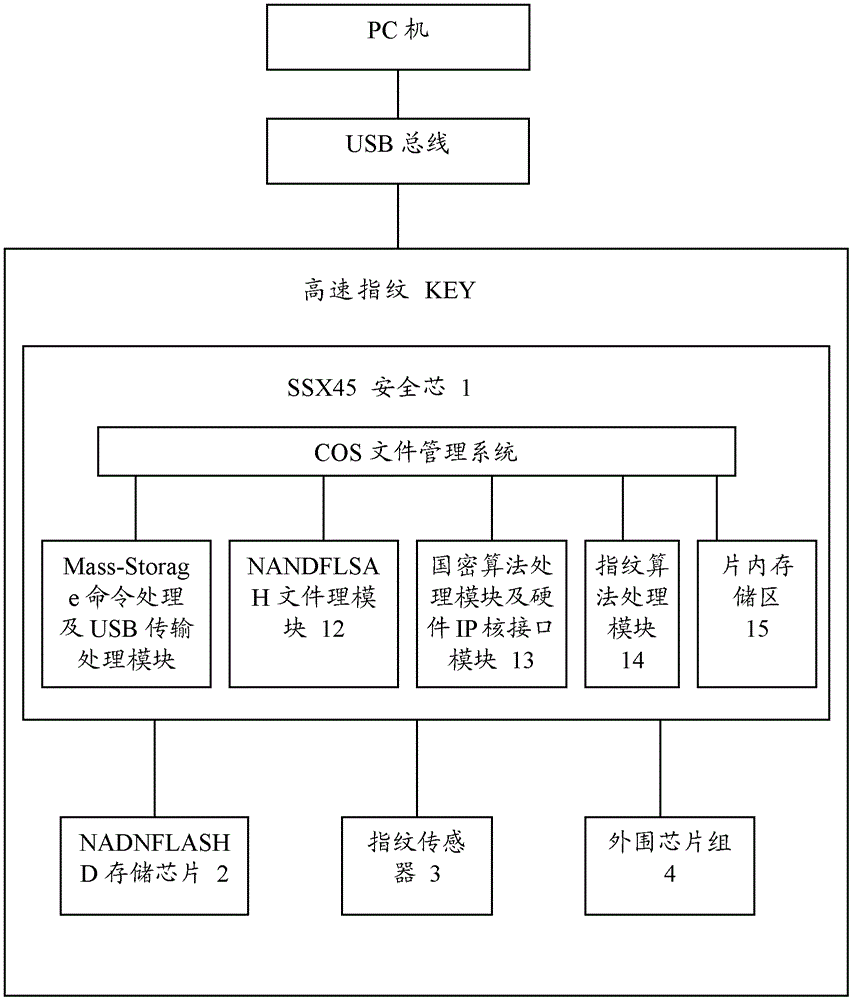
[0026] figure 1 It is a schematic diagram of the logical structure of the high-speed fingerprint KEY disk based on the national secret algorithm of the present invention. Such as figure 1 As shown, the fingerprint KEY disk includes: security chip 1 of model "SSX45" (SSX45 security chip), flash memory (NANDFLASH) storage chip 2, fingerprint sensor 3 and peripheral chipset 4. SSX45 security chip 1, as the main control chip, is connected with NANDFLASH memory chip 2, fingerprint sensor 3 and peripheral chipset 4 respectively to control the work of the entire Key disk. SSX45 security chip is connected with PC through USB bus.
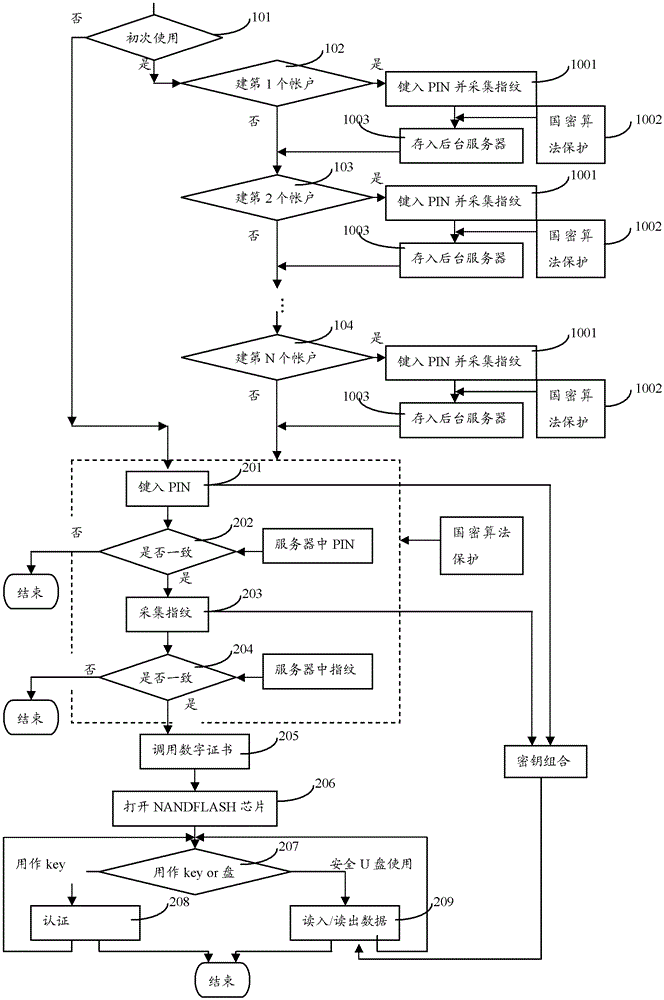
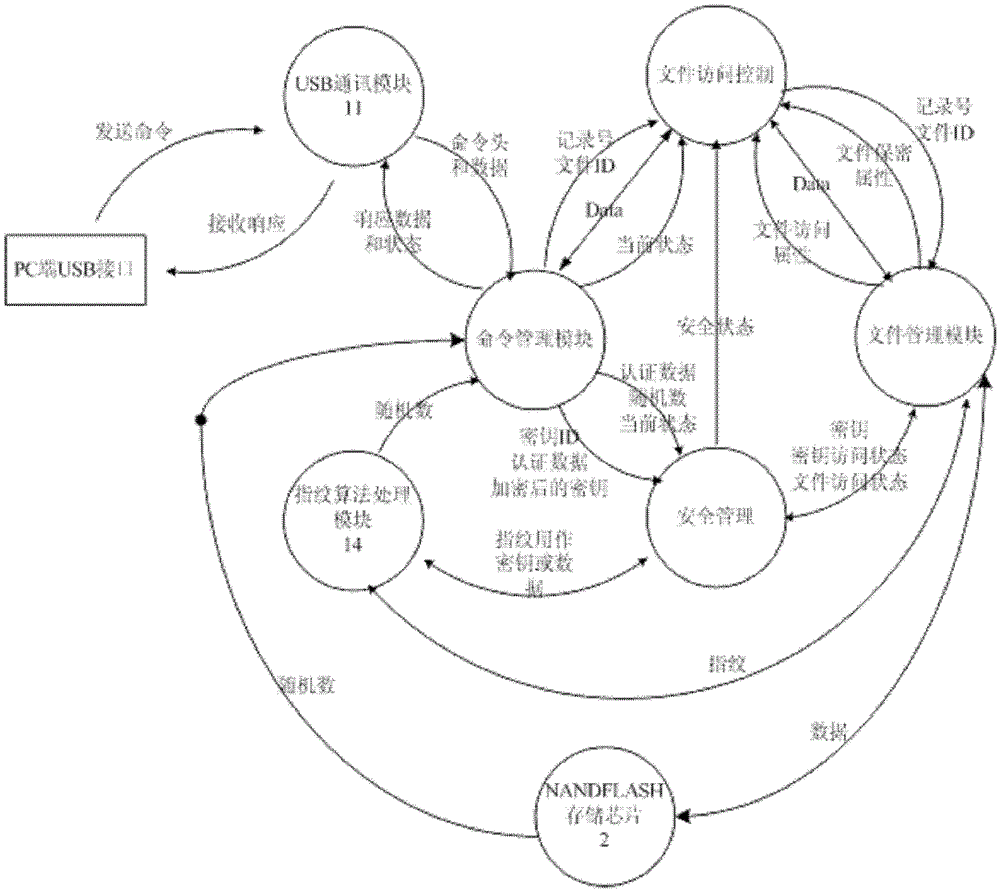
[0027] The core component of the high-speed fingerprint KEY disk based on the domestic cryptographic algo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com