Method for realizing digital fingerprint encrypted video multicast transmission
A digital fingerprint and multicast transmission technology, applied in the field of information security, can solve the problems of high system implementation cost, increased transmission bandwidth usage requirements, and inability to detect fingerprints by detectors.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
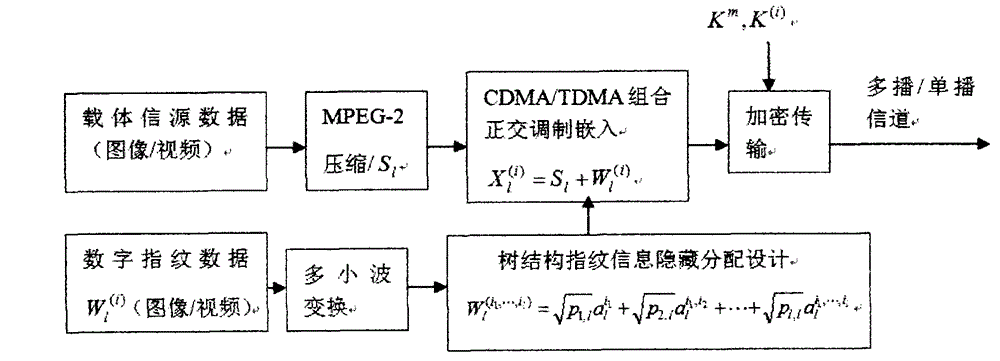
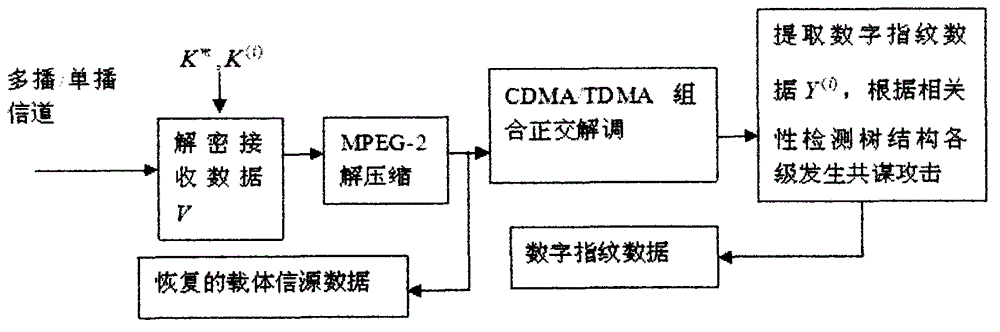
[0092] The method for implementing digital fingerprint encrypted video multicast transmission of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0093] The invention realizes the video multicast transmission method of digital fingerprint encryption, including digital fingerprint encryption transmission and digital fingerprint encryption reception.
[0094] The encrypted transmission of the digital fingerprint comprises the following steps:
[0095] 1) The carrier source data of image and video is compressed by MPEG-2 standard to form MPEG-2 basic data S l ;
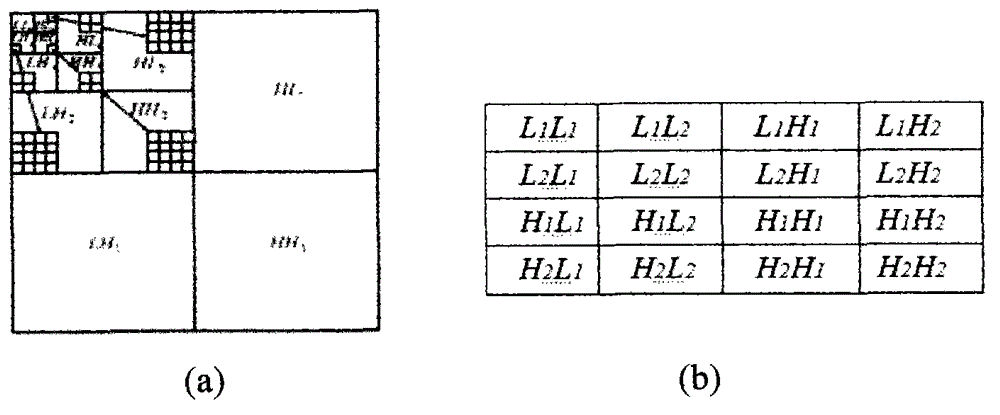
[0096] 2) Digital fingerprint data of images or videos Use the DGHM multi-wavelet transform tree for processing to form a multi-wavelet tree;
[0097] 3) According to the importance of digital fingerprints, different data of digital fingerprint image feature points are decomposed into different energy fingerprint vector bases And form digital fingerpri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com