D2D terminal access control method, D2D terminal, eNB and MME
A D2D and terminal technology, applied in the field of communication, can solve the problem of not reducing the traffic load of the base station, and achieve the effect of network robustness and processing capacity enhancement, and user experience improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
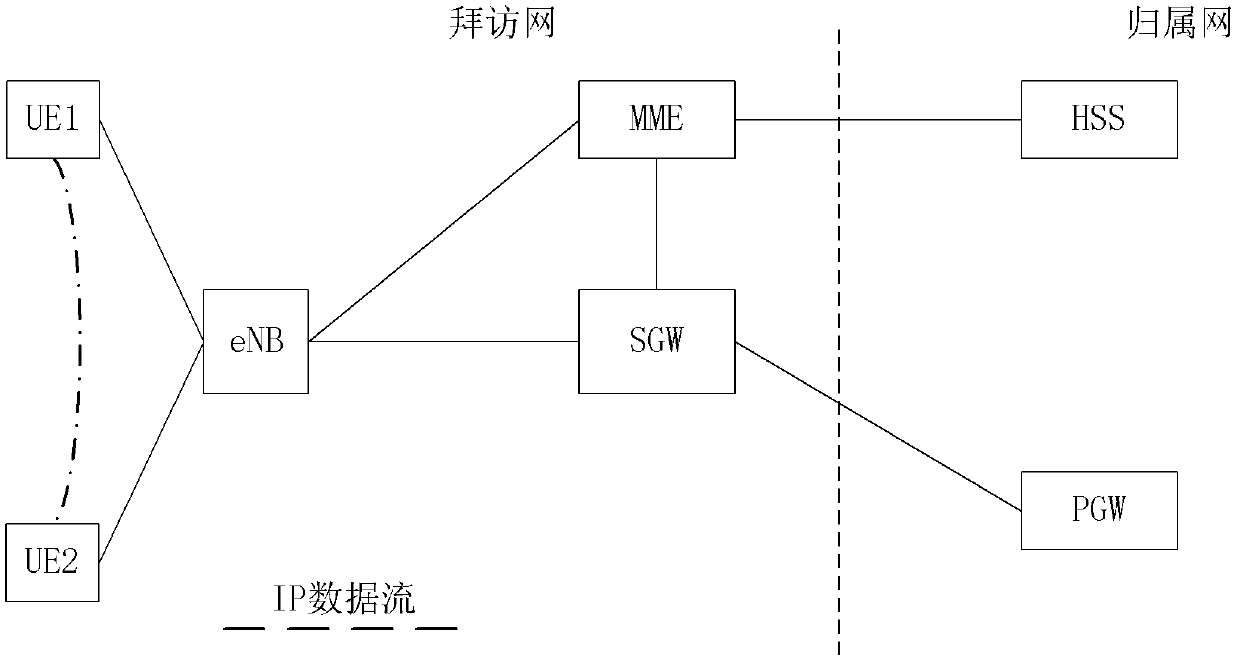
[0072] Figure 7 It is a flowchart of a network sending a D2D supporting capability to a terminal according to an embodiment of the present invention. This embodiment mainly describes how the D2D terminal obtains the eNB address supporting the D2D capability. For example: 1) carry the eNB address supporting D2D capability in the broadcast message; 2) carry the eNB address supporting D2D capability in the access response message; 3) carry the eNB address supporting D2D capability in the initial configuration parameters by OAM.
[0073] The D2D terminal can choose a common eNB for access, or an eNB supporting D2D capability for access. After a D2D terminal selects a common eNB for access, if it wants to initiate a D2D session, it needs to re-select an eNB that supports D2D capabilities for access. Specific steps are as follows:
[0074]Step S702: Statically configure whether to support D2D capability on the eNB. When the eNB broadcasts the system, it carries the indication of...
Embodiment 2
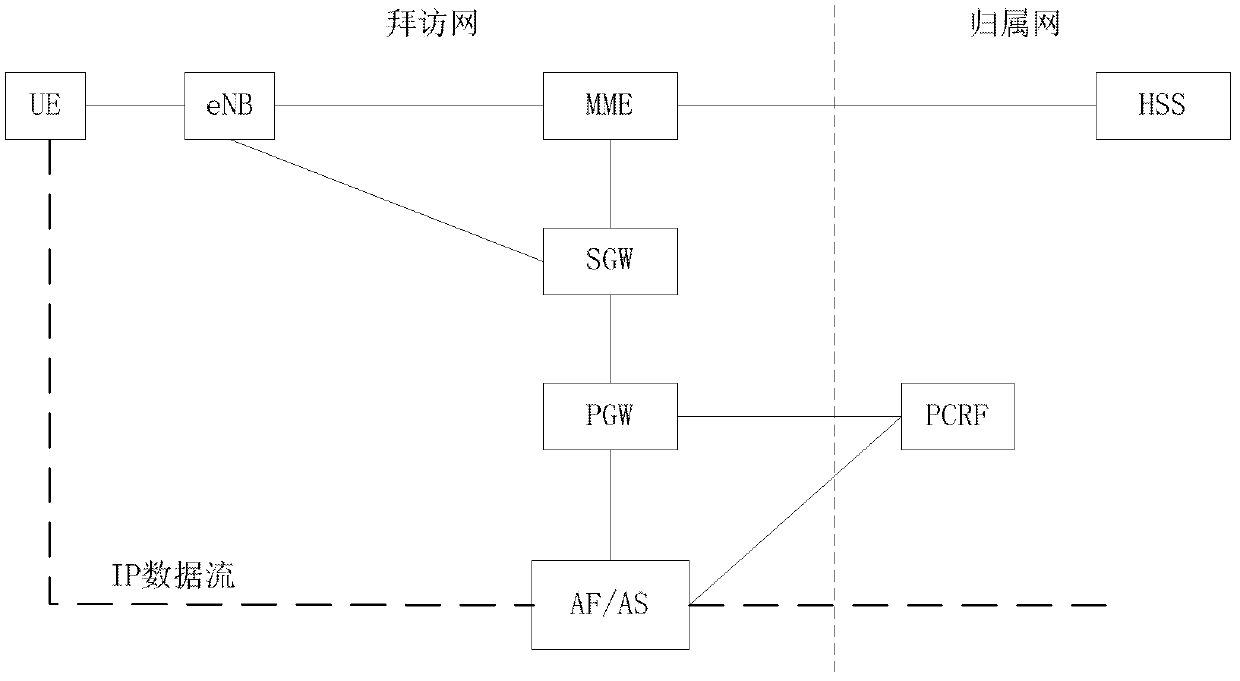
[0082] Figure 8 It is a flow chart of an eNB performing access control on a D2D terminal according to Embodiment 2 of the present invention. This embodiment mainly describes the scheme of eNB performing D2D control. The eNB requests the D2D subscription data from the MME, and decides whether to allow the D2D session according to the D2D subscription data, the network's ability to support D2D, and the operator's policy. Specific steps are as follows:
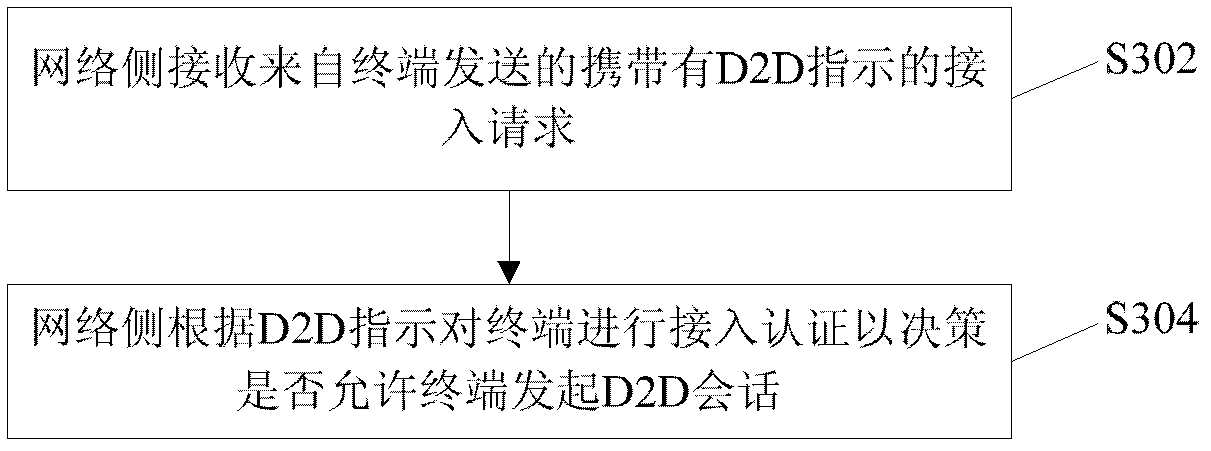
[0083] Step S802: the D2D terminal initiates an access request to the eNB, and carries a D2D indication in the request message. The D2D indication may be one of D2D type or D2D capability.
[0084] Step S804: the eNB sends an access request to the MME, and carries a D2D subscription request indication in the access request. The D2D subscription request indication may be one of D2D type, D2D capability or D2D subscription request.
[0085] Step S806: The MME initiates a location update request to the HSS to request subscript...
Embodiment 3
[0091] Figure 9 It is a flow chart of an eNB performing access control on a D2D terminal in an ATTACH process according to Embodiment 3 of the present invention. This embodiment mainly describes the solution of eNB performing D2D control during the ATTACH process. The eNB requests the D2D subscription data from the MME in the Attach request message, and the MME sends the D2D subscription parameters to the eNB. The eNB decides whether to allow the D2D session according to the D2D subscription data, the network's ability to support D2D, and the operator's policy. Specific steps are as follows:
[0092] Step S902: the D2D terminal initiates an ATTACH request to the eNB, and carries a D2D type or D2D capability indication in the request message.
[0093] Step S904: the eNB sends an ATTACH request to the MME, and carries one of D2D type, D2D capability or D2D subscription request indication in the ATTACH request.
[0094] Step S906: The MME initiates a location update request t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com