Attack positioning and assistant positioning device and method
A technology of positioning device and attacker, applied in the network field, can solve the problems of consumption, occupation of central processing unit processing resources, large network bandwidth, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
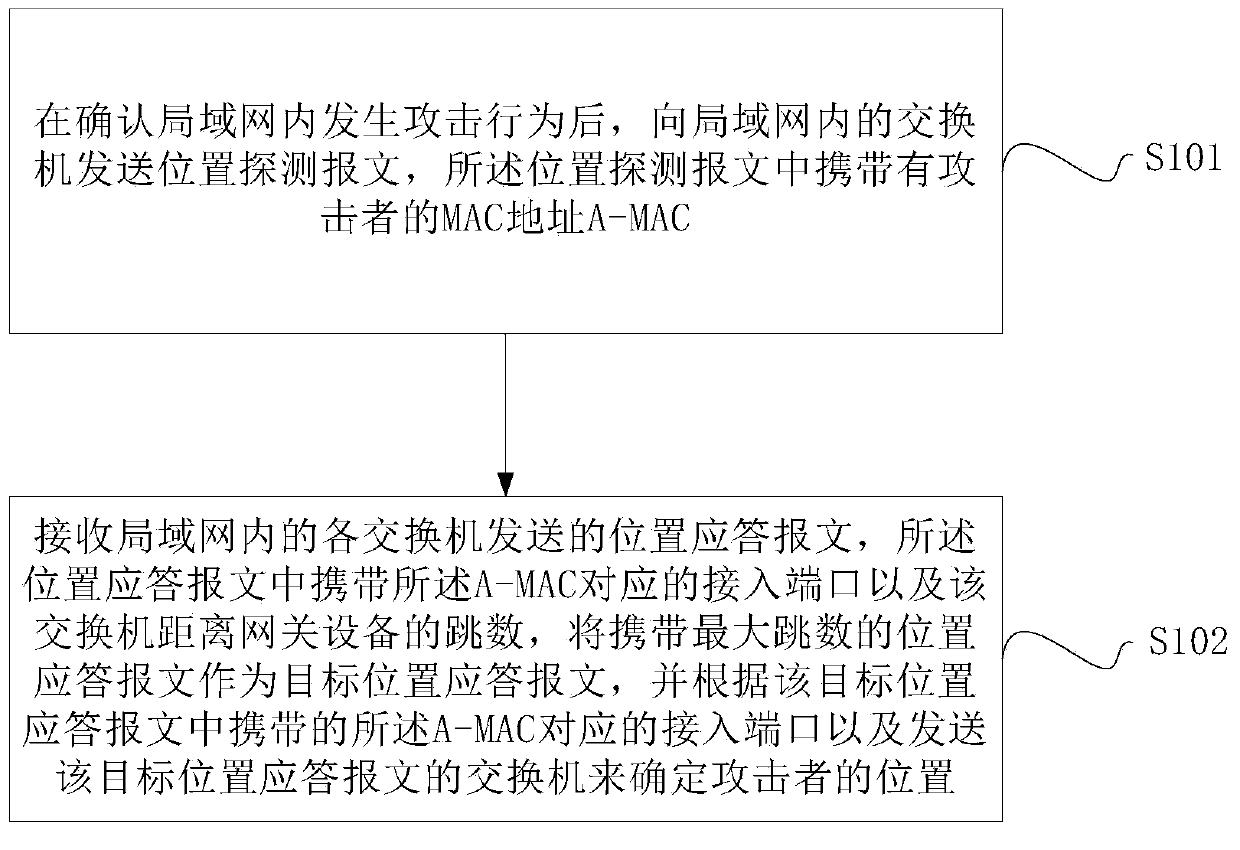
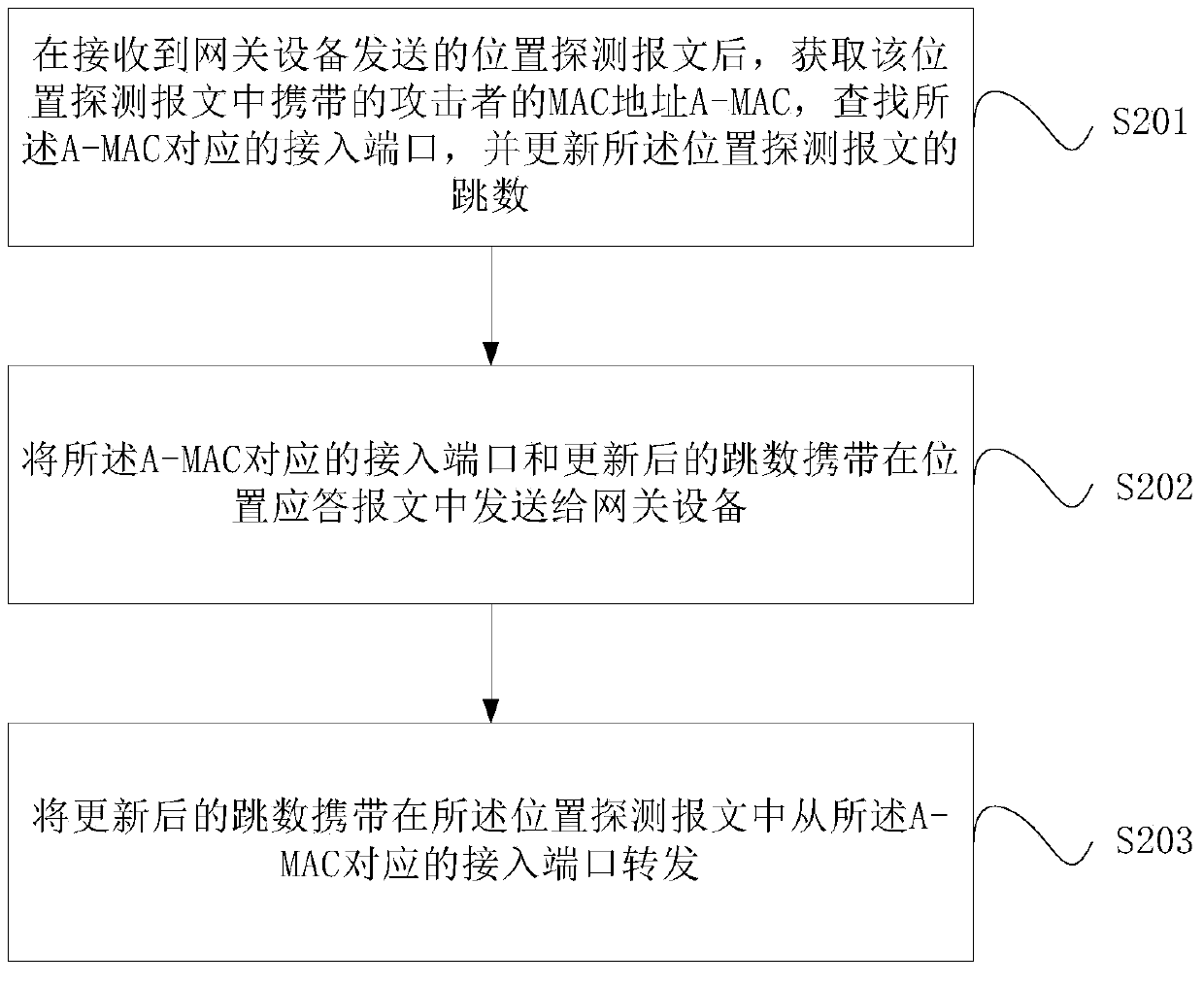
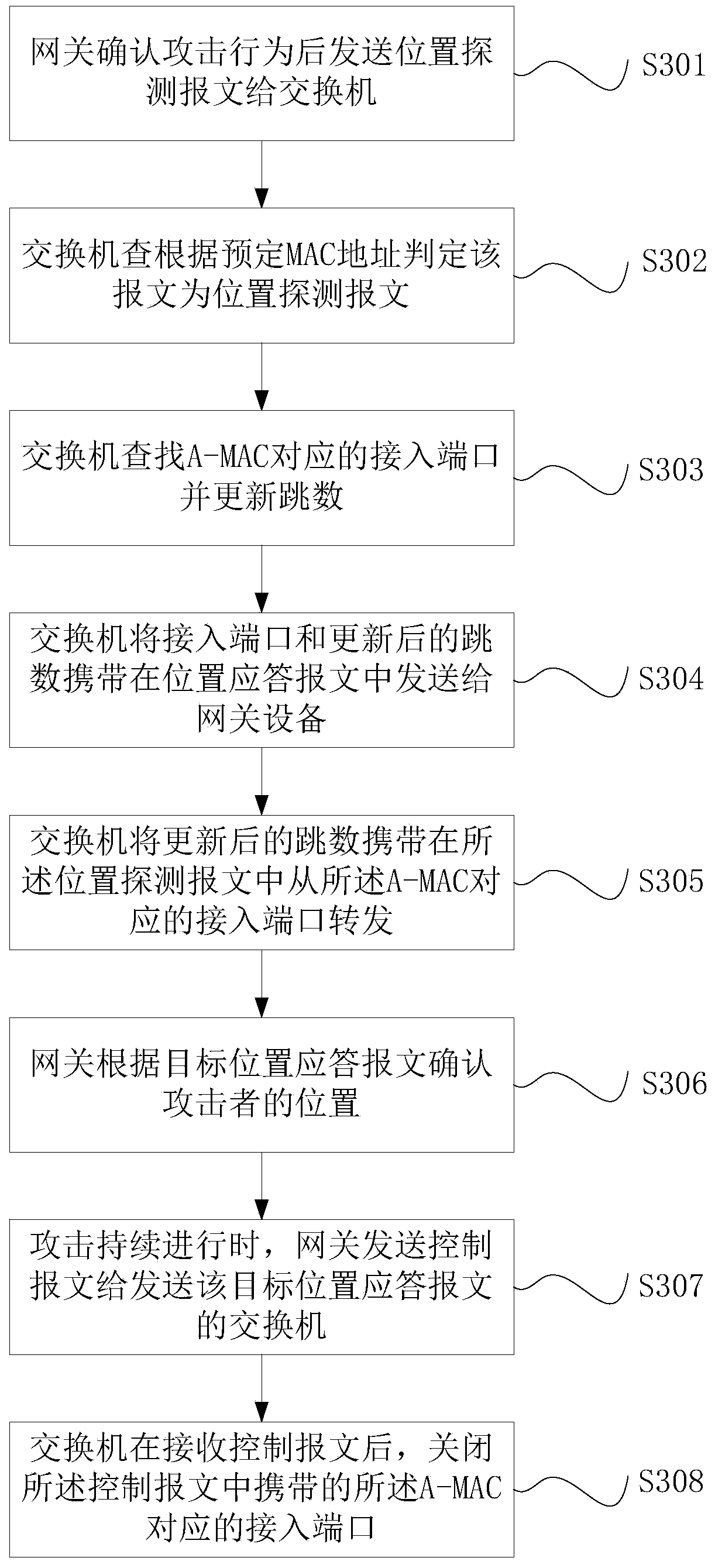
[0027] In practical applications, the gateway device usually identifies attack packets based on packet traffic and locally stored entries. Taking ARP (Address Resolution Protocol, Address Resolution Protocol) attack as an example, within 5 seconds, if the number of ARP packets received from the same source MAC (Media Access Control, Media Access Control) address exceeds a certain threshold, it is considered to have occurred At this time, the system will add this MAC address to the attack detection table entry, and filter out all ARP packets sent by the source MAC address before the attack detection table entry ages, so as to avoid being attacked. However, in this solution, the gateway device cannot know which host in the LAN is sending the attack message, and accordingly, the network administrator cannot take corresponding blocking measures.
[0028] In view of the problems existing in the above solutions, the present invention provides an attack positioning and auxiliary posi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com