A network management client topology management system and method
A topology management and client-side technology, applied in the field of network management, can solve the problems of lack and portability, and the topology management system cannot manage different types of devices, achieving high compatibility and saving development costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
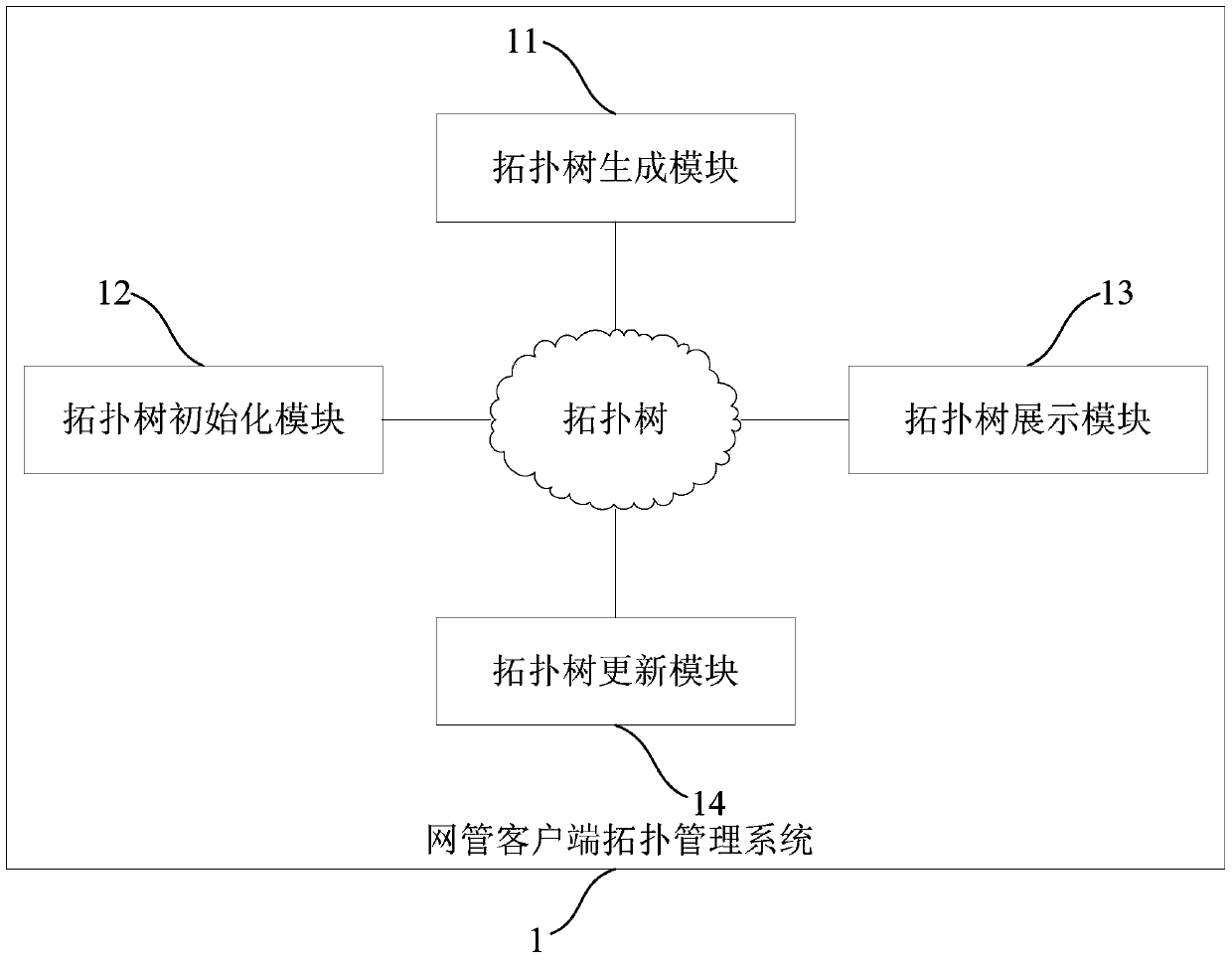
[0058] This embodiment provides a network management client topology management system 1, which is applied to the network management system. The network management system is divided into a server and a client. The topology management is mainly presented through the client. In the topology management, the server is mainly used to start the discovery program. , to write the discovered data into the database, and the client is mainly used to read the discovered results from the server, and display the read results with a logical topology diagram and a physical panel diagram. In the stage of topology discovery, the present invention utilizes the commonality among network devices to abstract the commonality, and manages it according to the level of area, subnet and equipment, presents the topology structure of the whole network, and searches layer by layer until the terminal device is found . On the network topology map, a more realistic device image is used to distinguish differen...
Embodiment 2
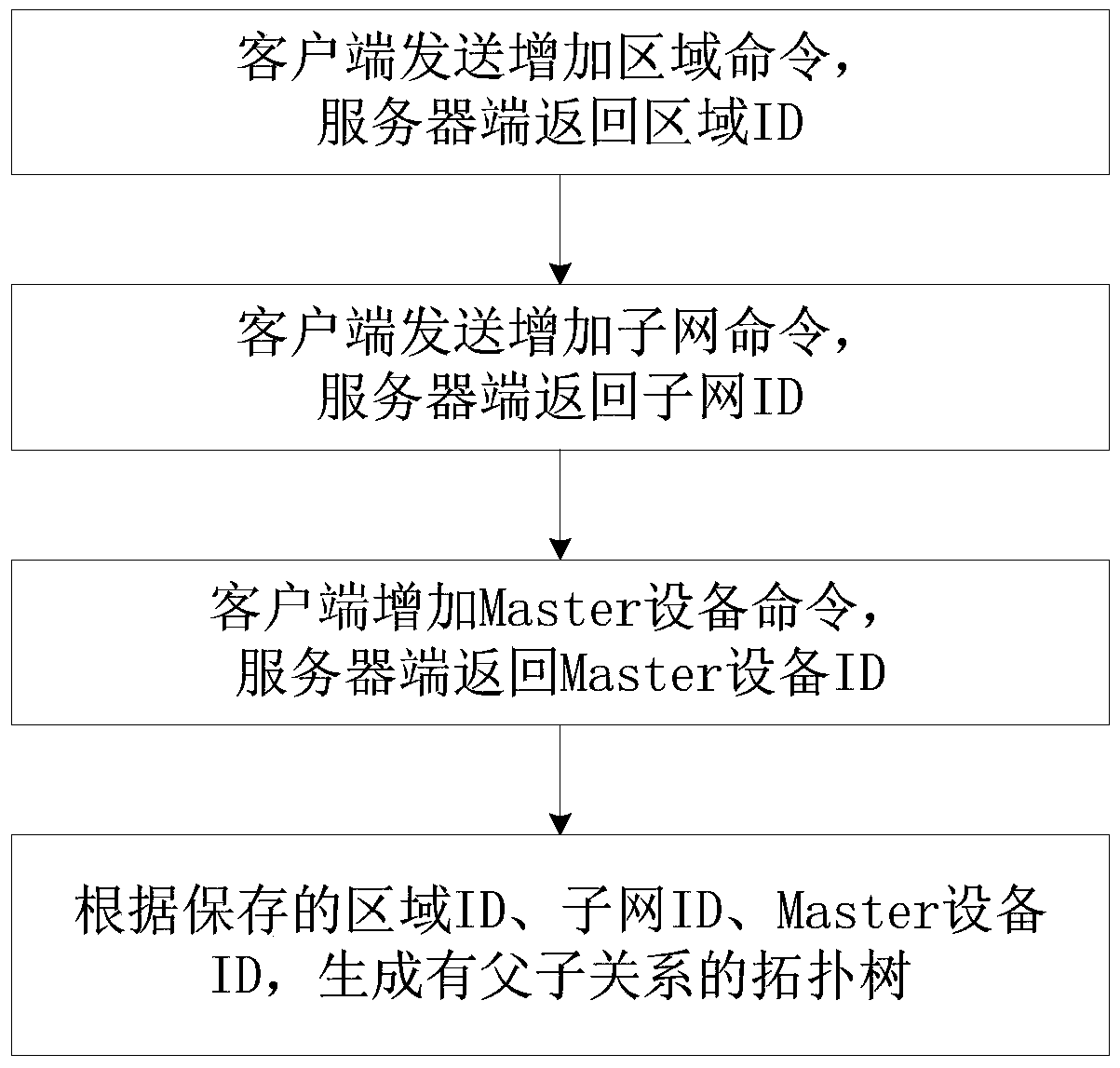
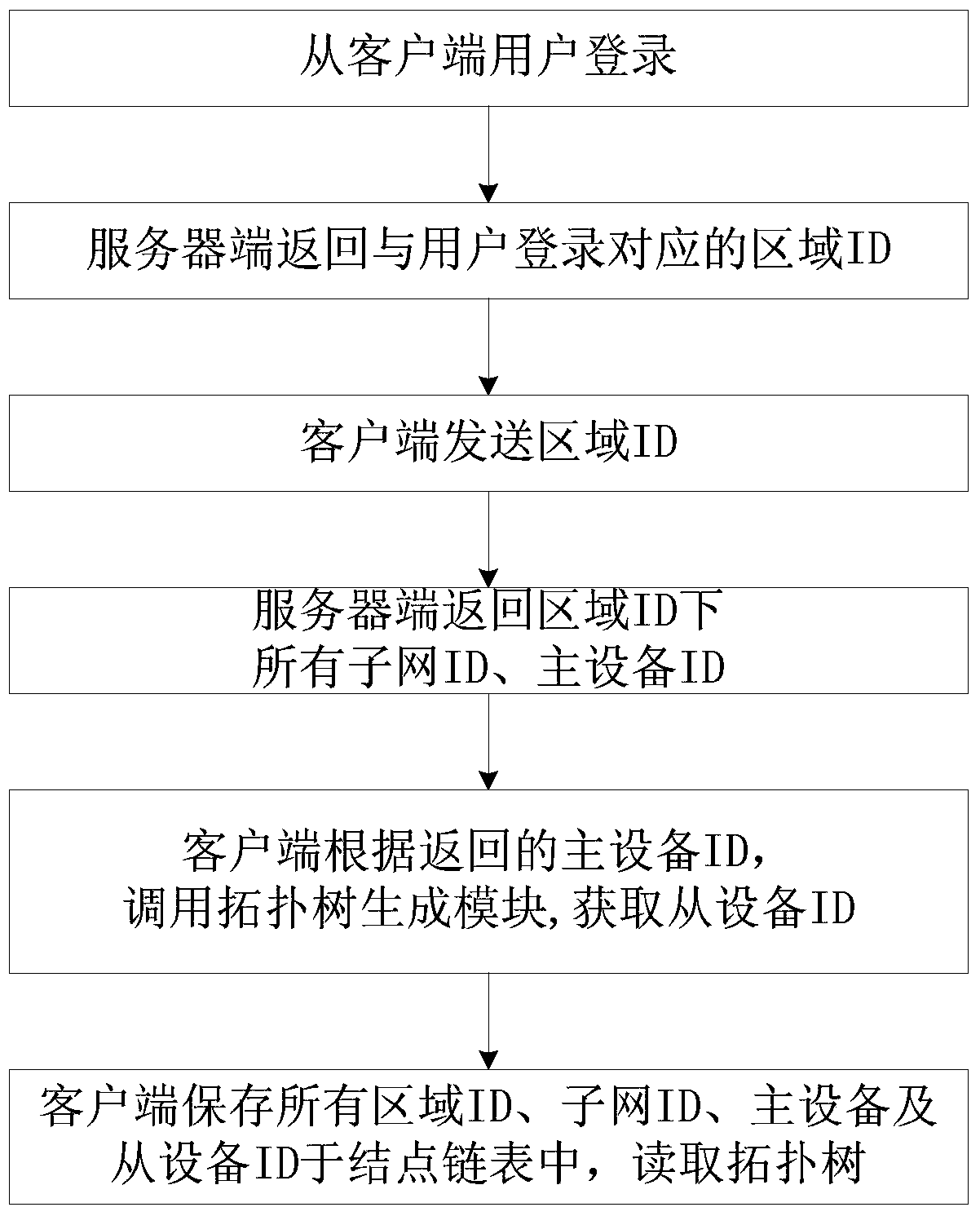
[0088] This embodiment provides a network management client topology management method, which is applied to a network management system composed of a server and a client, and the network topology in the network management system is managed according to the levels of areas, subnets, and devices, such as Figure 7 As shown, the network management client topology management method includes:
[0089] S1, receiving commands for adding area, adding subnet, adding master device, and sending master identity authentication, and receiving from the server side according to adding area command, adding subnet command, adding master device command and sending master identity authentication The regional identity authentication, subnet identity authentication, master device identity authentication, and all slave device identity authentications under the master device returned by the The identity authentication is stored in the node linked list, and the regional identity authentication, subne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com